I am using the latest development release. When I try to create a new SA for ISAKMP, it asks for Initiator Cookie and Encryption Cookie. I know the initiator cookie but I am not sure where I can I get this encryption. I know all the configuration of my VPN (encryption algorithm, authentication algorithm, pre-shared key) let me know if it is required here. I have to tried to input the pre-shared-key there but it does not take it. Please help. There is no documentation available for this. asked 18 Jun '12, 06:27 chetan1989 edited 11 Jul '13, 16:51 Kurt Knochner ♦ |
4 Answers:
IKEv1 Decryption First of all: Wireshark 1.8.0 implements only 3DES and DES for IKEv1 decryption (same for version 1.6.8).
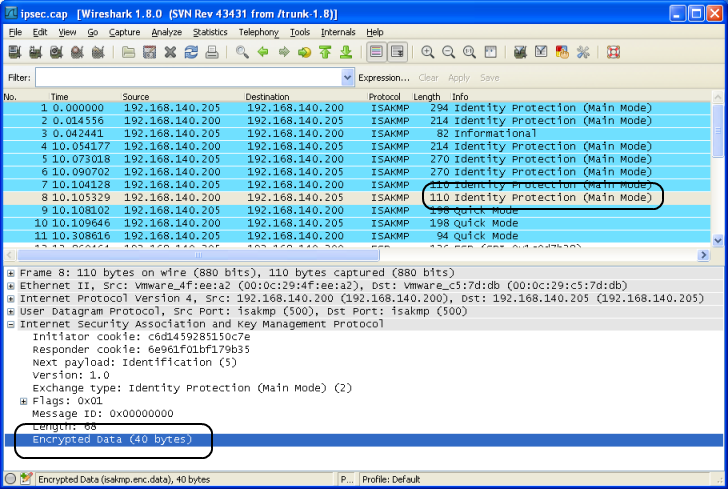
If you want do decrypt any other algorithm, the dissector needs to be extended (Volunteers are welcome!). You can file an enhancement request for this at https://bugs.wireshark.org, possibly with a link to this question. To get the required IKEv1 parameters for the dissector (Initiator's COOKIE and Encryption Key) you need debug output from your IPSEC implementation. I tested with strongSwan 4.4 on Linux and with this capture file (with the capture file and the data provided in this answer, you can try it yourself). To get the value of "enc key" in the log, you need at least this debug option: Look for ICOOKIE and enc key in the Pluto debug log. HINT: If you use any other IPSEC implementation please read the manual how to get that information. Extract the values of ICOOKIE and ‘enc key’ WITHOUT spaces. HINT: The “enc key” spans two lines!! ICOOKIE: c6d1459285150c7e Use those values for
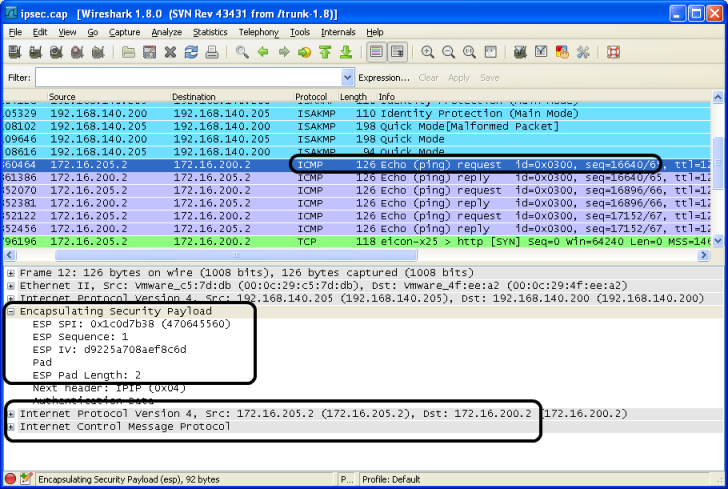
Test File: ipsec.pcap Result without decryption:
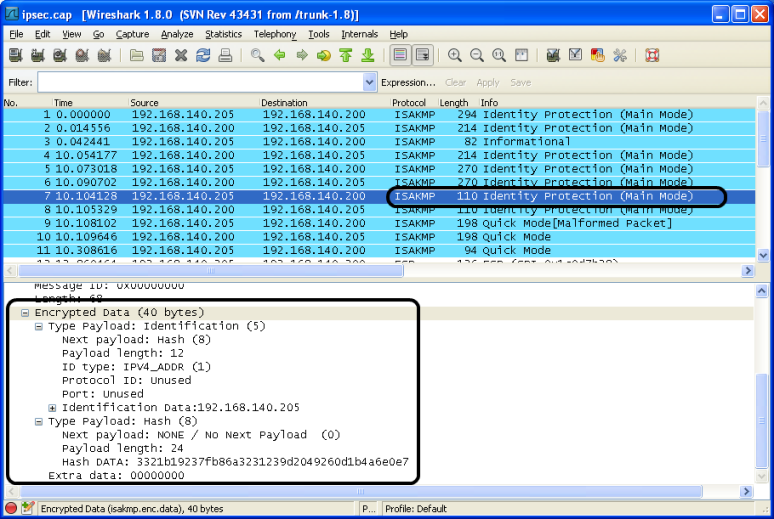
Result with decryption:
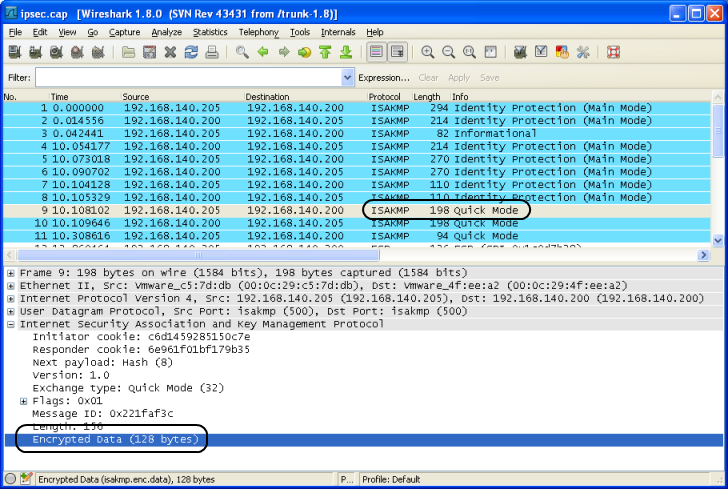
ESP Decryption To decrypt ESP packets with Wireshark 1.8.0, you need again debug output from your IPSEC implementation. For Linux and strongSwan, you'll get that information with this command:
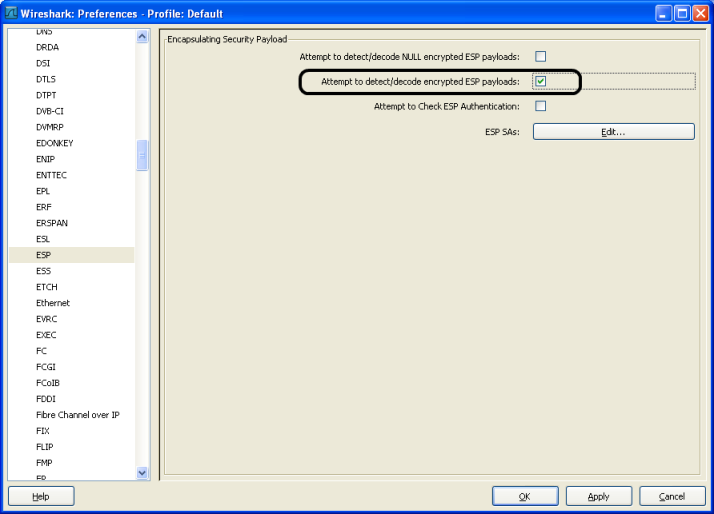
Output: Use those values for the ESP dissector parameters, as shown in the following screenshots. HINT: Take care not to add a space at the end of any parameter (SPI, key, etc.) as decryption will not work in that case. First enable ESP decryption.
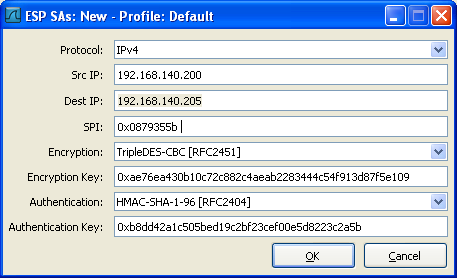
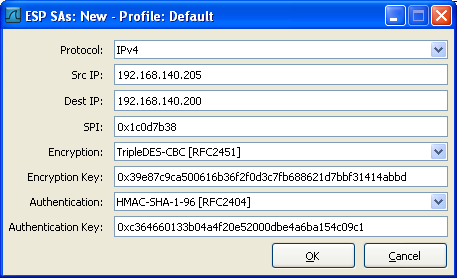
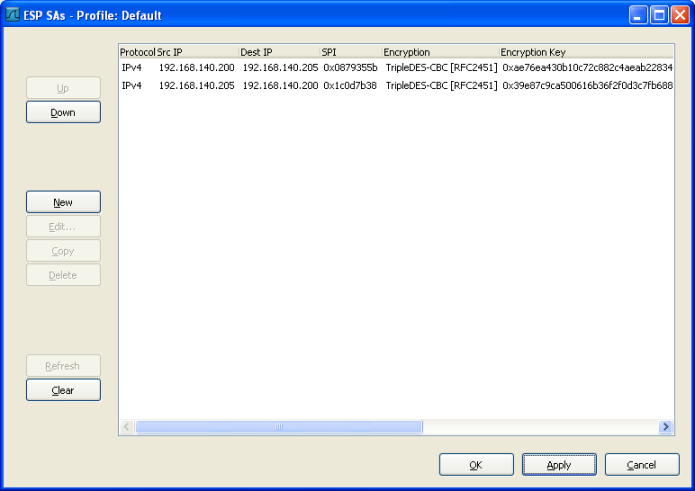
Then add the two ESP SAs (one for each direction!)
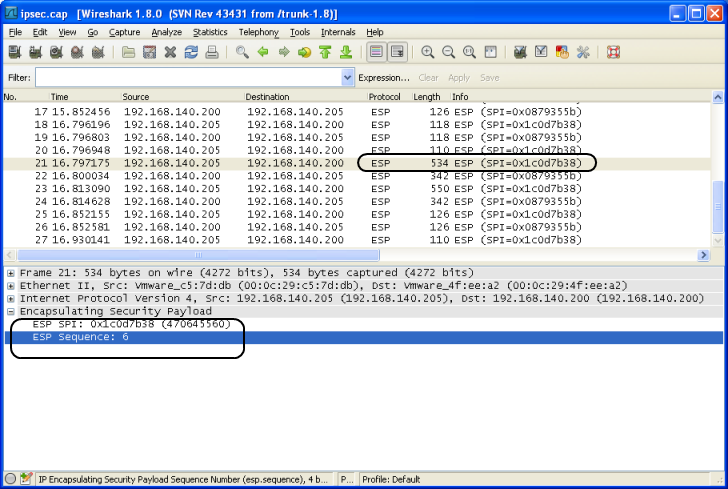
If the parameters match the capture file data, Wireshark will be able to dissect the ESP packets. Result without decryption:
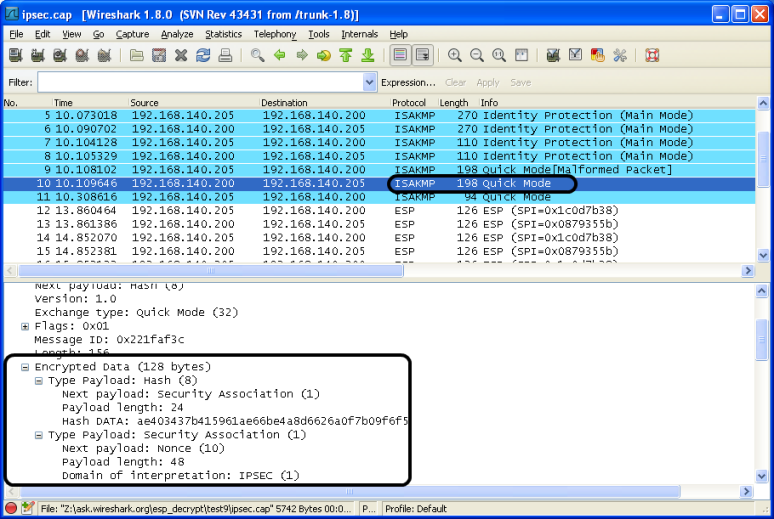
Result WITH decryption:
Regards answered 23 Jul '12, 09:10 Kurt Knochner ♦ edited 17 May '15, 06:37 |
did you add the PSK under the ESP options?
BTW: Did you check this?
Especially, if your version of Wireshark is built with libcrypt! Regards answered 18 Jun '12, 07:36 Kurt Knochner ♦ edited 18 Jun '12, 07:36 Thanks for your reply. I don't see option to create New Encryption Key, there is an option to create a new SA (Security Association) wherein I provide the Encryption Key. But when I try to put the same key in ISAKMP Encryption Key field it gives me an error "error in field 'Encryption Key': Error parsing hex string" I don't know how to get the hex value. P.S. My wireshark is built with Gcrypt. I don't think that could be a problem because I can decrypt ESP packets easily (18 Jun '12, 07:46) chetan1989
O.K. I think I misunderstood your request. Do you want to decrypt IKE Phase I packets 5+6 (the encrypted ones) and possibly the whole IKE Phase II traffic? (18 Jun '12, 08:36) Kurt Knochner ♦ Yes you are correct (18 Jun '12, 12:08) chetan1989 |
Hi, If you are using racoon (from ipsec-tools), you can see the encryption key from the debug logs of racoon. e.g: 2012-07-11 11:35:55: DEBUG: final encryption key computed: 2012-07-11 11:35:55: DEBUG: 79d5eabc 78ae740b 47258300 f8de371e a4a9da87 4facf41 Also, I had found issues in decryption when i use aes algorithm. With 3des, decryption works fine. answered 11 Jul '12, 01:53 divya |
If you are looking for the cookie and encryption key in answered 11 Feb '17, 20:41 dlenski edited 11 Feb '17, 20:42 |

can you give command: ip xfrm state --- for windows?
Could you fix/update the images referenced above? They all show as broken links now.