Hi, I have a problem with Wireshark. The idea is that when listening on HTTP packets they show an error of 304 and 404 and i can't read the address of the page. I use it on the Back Track 5 R3. Before running the Wiresharka I use the command "echo 1/proc/sys/net/ipv4/ip_forward > and" arpspoof-i eth0-t 192.168.1.1 192.168.1.9 "in order to be able to listen. Gets them, but flawed with errors. PS: Sorry for my English. I see it:
asked 25 Aug '13, 07:04 Marcinxxl2 edited 25 Aug '13, 07:56 |
One Answer:
To quote the arpspoof man page:
so that command is ARP-spoofing so that traffic to 192.168.1.9 is redirected through 192.168.1.1, but it doesn't affect traffic from 192.168.1.9, so you will only see the HTTP replies to 192.168.1.9, not HTTP requests from 192.168.1.9, so you won't see the requests, and therefore will not see the URLs. As I said in my comment, the HTTP packets that get a 304 do so because the HTTP request said "send me the page only if it's been modified after this time" and it hasn't been modified since that time, and the HTTP packets that get a 404 do so because the HTTP request said "send me the page with this URL" and there IS no page with that URL; that's how HTTP works. answered 25 Aug '13, 11:56 Guy Harris ♦♦ edited 25 Aug '13, 11:58 Actually, sorry, my mistake. You know how to do that was in two pages? (25 Aug '13, 12:14) Marcinxxl2
I'm not sure I understand what you're asking here. (25 Aug '13, 12:50) Guy Harris ♦♦ |

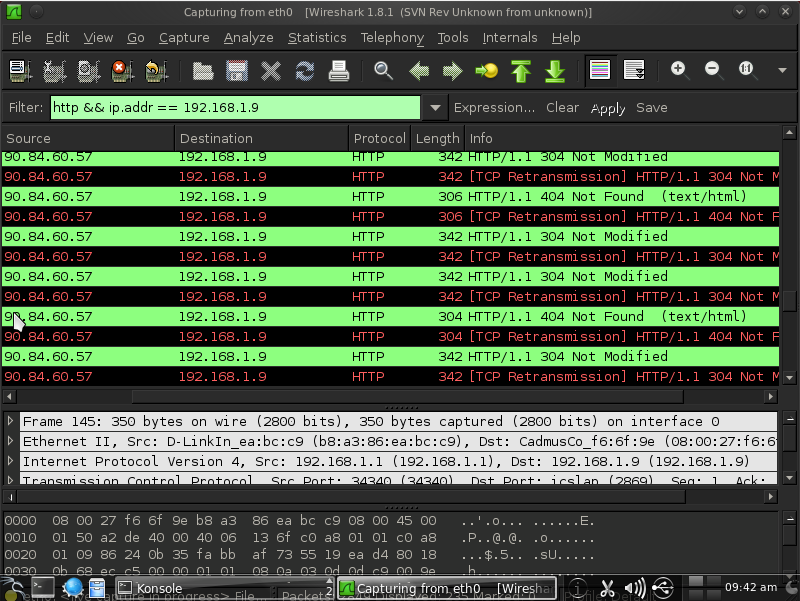
304 typically means that the system fetching the page has a cached copy and is asking 1) whether the page has been modified since a certain time (the time when the cached copy was fetched) and 2) for a copy of the page if it has been modified since then. 404, of course, means that the page in question doesn't exist.
By "the address of the page" I assume you mean the URL of the page; you'll see that in the HTTP request, not the reply. Are you not capturing the requests? Or are they not being sent from 192.168.1.9, so that they're not showing up with your display filter?
And intercepts the request and they are sent from this address. I do not know why all the HTTP packets give error 304 or 404. When I run Wireshark on listening computer does not show on these errors, and the URL of the page.