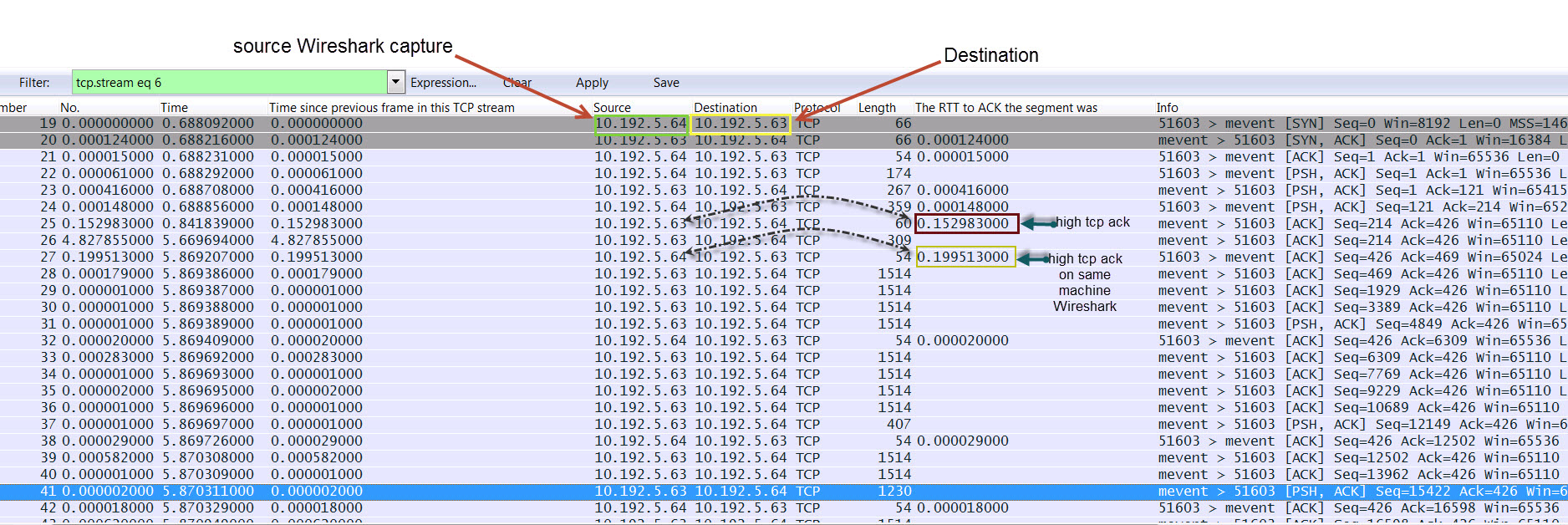
Hi All, I am trying to analyze TCP agent based application that mostly using PSH flags. The application suffering fro some latencies that message should not exceed 50msec. Now as the agent is kind of interactive that change messages and not TCP buffered PSH flags nature its could be that communication is idle to up to 5sec. The problem is that i can see that destination sometimes TCP ACK to source around 180~200msec , but i can see the same issue on the source where the Wireshark capture made ,and my question is what i can i understand from high values ACK 180~200 if its exist on the machine where capture taken should i treat such as pure network congestion or some kind of OS environmental issues like blocking antivirus etc.. Please advice Thanks asked 18 Sep '13, 05:02 tbaror |
One Answer:
Please watch the following video. It pretty much explains what's going on in your sample capture file. Wireshark Tutorial of TCP Nagle and Delayed Ack interaction Regards answered 20 Sep '13, 06:53 Kurt Knochner ♦ edited 20 Sep '13, 06:53 Thanks Kurt exactly the answer i was looking for. Thanks (23 Sep '13, 22:33) tbaror |

Please post the capture somewhere accessible to others, e.g. Cloudshark or a file sharing service and posting the link back here. Diagnosing issues by looking at a screen capture is very difficult.
If you put the capture on Cloudshark, you can also add comments on the packets.
Done uploaded to Cloudshark.