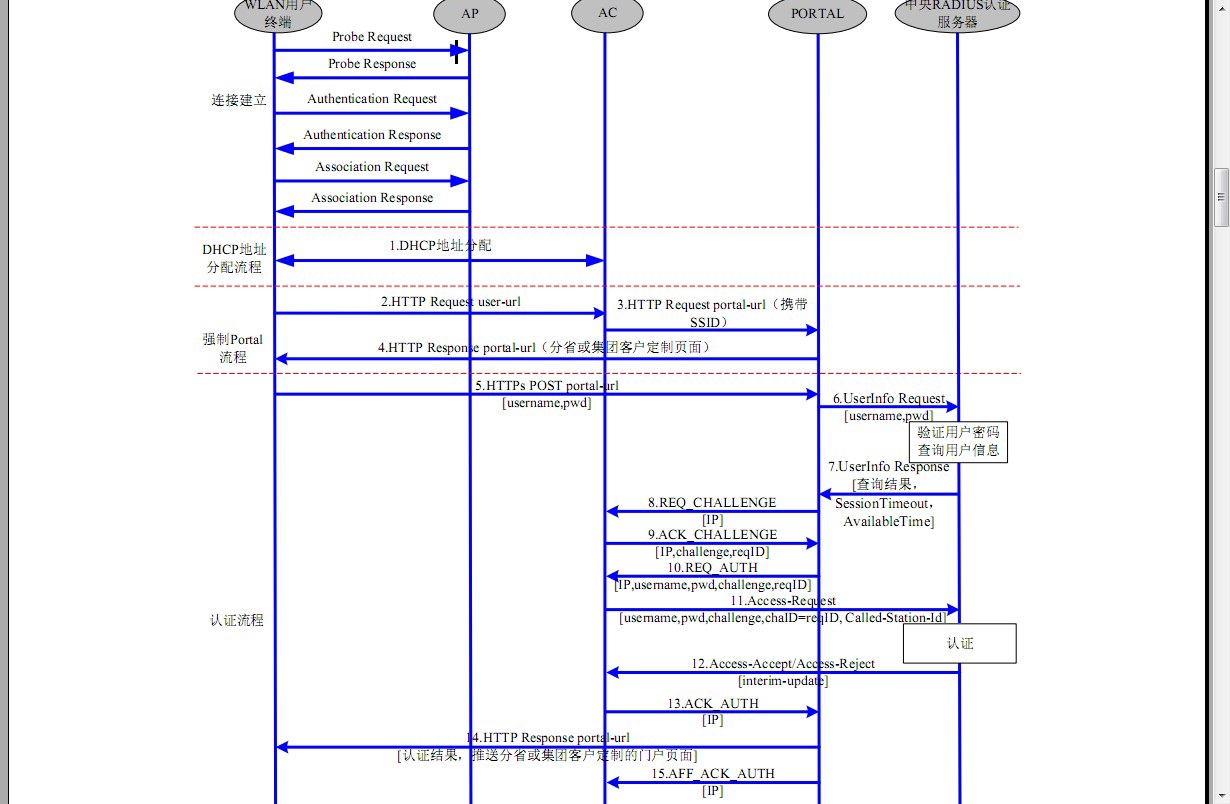
I want to dissect challenge and auth process as below. After analyzing, I find packets 16806~16814 in the file, but how to dissect them with tshark/wireshark? Are they sccp packages? The processes 8~13 are what I concerned. asked 03 Dec '13, 17:43 metamatrix |
One Answer:
From the capture file I conclude
Now, there are those packets you mentioned: #16806 - #16814 You see communication between those two systems.
So, it looks like there is sccp (Cisco Skinny) involved, due to port 2000. However, I believe the communication is from 192.168.1.89:2000 (sccp) --> 192.168.1.21:50100. So, port 2000 is just a random source port and thus not related to Skinny. The data in the frames do not fit the Skinny protocol, as the first 4 bytes should be the length of the Skinny payload and if you look at the frames, that's not gonna work (length is way too large). So, I guess this is a custom protocol used by your H3C wireless controller that is unknown to Wireshark. You should be able to figure out which service accepts data on port 50100 on the Radius server (192.168.1.21) by running these commands Windows (as Administartor from an elevated DOS box)
Then look for the string ":50100" and post those lines +/-2 here. It will look similar to this Linux (as root)
That will help to understand which component is using the (yet unknown) protocol. With that information you can search the documentation of the H3C wireless controller (search for port 50100) or ask in their support forum. Regards answered 10 Dec '13, 04:42 Kurt Knochner ♦ edited 10 Dec '13, 06:58 Thank you, Kurt. I think the unkown protocol using port 2000 is not a coincidence. Since I found a document that mentions challenge info also using port 2000. (http://wenku.baidu.com/view/e0beea2f647d27284b73513f.html?qq-pf-to=pcqq.c2c page 10).And I also found first 2 bytes of the data possibly mean some type. So I think I can use the port 2000 and first 2 bytes of data to distinguish the step of wlan user logon process, can I? (10 Dec '13, 21:34) metamatrix Thank you, Kurt. I've found the H3C portal protocol specification :) (http://wenku.baidu.com/view/8a698abec77da26925c5b0b5.html). (10 Dec '13, 21:57) metamatrix Is there also an english version of the document? (11 Dec '13, 07:20) Kurt Knochner ♦ I'm afraid there is no English version of the document that can be found. Chinese version is shared by somebody on internet, and in baidu doc most of documents are in Chinese. (11 Dec '13, 18:40) metamatrix |

 The file:
The file:
Any one have ideas?