Hi All, We are seeing too many tcp retransmissions from the exchanges we have integrated with. Here is one of the issues we are seeing, and it causes timeouts. I am very new to this, so would like some insights about how to resolve such kind of issues. I can provide a bigger set of data if required. Attached is the screenshot. Thanks, Dhaval asked 06 Aug '14, 13:24 dhavalkotecha edited 06 Aug '14, 13:27 |
One Answer:
Based on the screenshot I think the problem is the "client" not adding the tcp timestamp option in packet #4 as negotiated in the 3-way handshake. What can be done?
It would help to add a capture file to cloudshark.org instead of just adding screenshots for detailed analysis of this kind of problems. answered 11 Aug '14, 06:16 mrEEde Hi mrEEde,i have a query as per my understanding a host that receives a TCP segment with a TCP timestamp must compare the current timestamp in the segment with what it considers the previous timestamp. If the timestamp is equal or greater than the previous one, it is acceptable. Otherwise, the segment should not be acknowledged. But as you said packet without timestamp so server is discarding it,so is this a normal behaviour to drop packet if it doesnt have timestamp.I tried to google it but no concrete answer found. (11 Aug '14, 23:22) kishan pandey I'm not good at reading RFCs but I think RFC1323 says we always have to send a TSVal and echo what we've received... 3.2 TCP Timestamps Option (12 Aug '14, 03:39) mrEEde ok,thanks mrEEde (12 Aug '14, 04:55) kishan pandey |

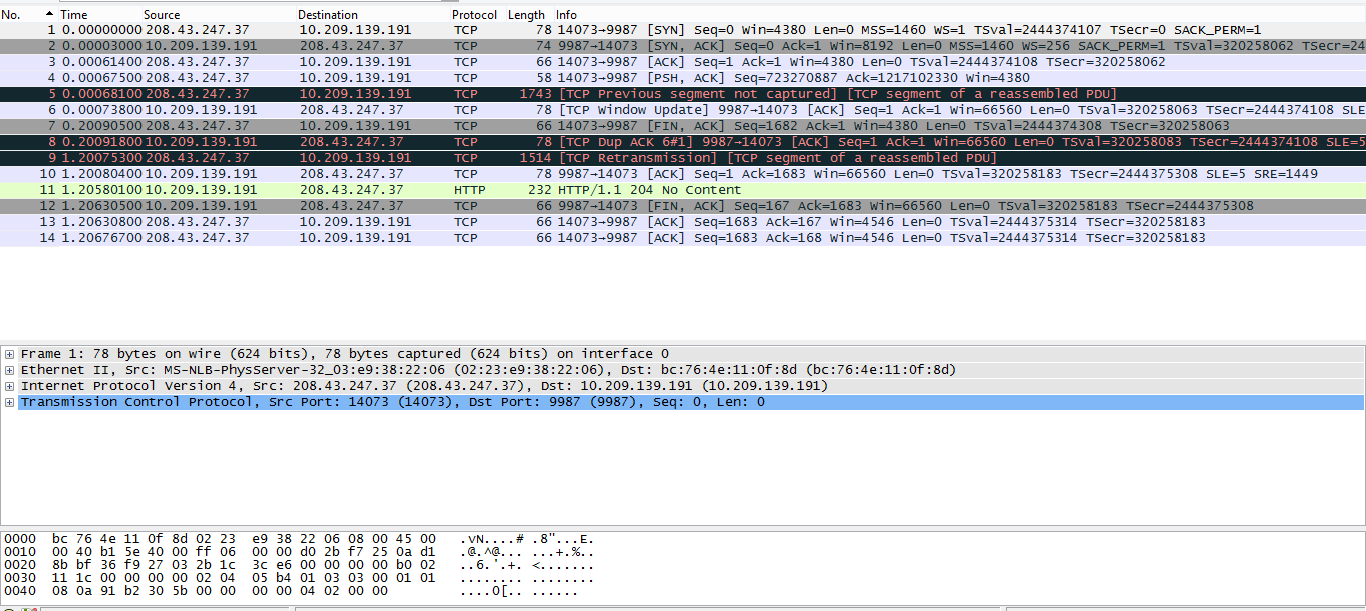
there is only one retransmission in your example, which is perfectly normal for almost any network out there. So, based on the information you provided so far, it's impossible to answer your question.
Oh wait... What is your question?