![alt text][1] Hi all, I'm trying to understand the data length and segment length calculation. I tried to take the IP total length and subtract the Ip Header length and the Tcp Header length but there seem to a difference for some frames. What is the reason? Cheers, A asked 26 Jul '15, 21:00 adriannuix edited 29 Jul '15, 18:11 |
2 Answers:
There the follwing length now: answered 28 Jul '15, 23:59 Christian_R edited 02 Aug '15, 13:29 I updated the link for a full file. Thank you (29 Jul '15, 18:12) adriannuix In the new trace I can´t see any uncommon length like at the old trace?! (29 Jul '15, 20:43) Christian_R I have spotted some, for example Frame 51 and Frame 52. (02 Aug '15, 16:09) Christian_R |
The problem is that the packet was written to the trace file with an incorrect frame.len of 66 bytes. If the original ip.len was 58 bytes and it is traveling over ethernet (which adds 14 bytes to the frame.len) wireshark thinks that the packet is only containing ip header plus tcp header plus 12 bytes tcp timestamp options in total 52 bytes.) answered 02 Aug '15, 13:13 mrEEde edited 03 Aug '15, 00:38 @mrEEde: Just out of curiosity. What do you think about Frame51 and Frame52 in the trace? Look at the IP.ID and the TCP Checksum. I think the Frame 52 is a corrupted version of Frame 51. Perhaps only in the capture file not really on the wire. (Because the corrupted Frame is always behind the original Frame). (02 Aug '15, 16:06) Christian_R Christian, frame 52 is not corrupted, it is an incomplete copy of frame 51 with no payload. As the tcp.checksum is calculated including the payload and the payload is missing, wireshark detects it as incorrect. (02 Aug '15, 23:34) mrEEde @mrEEde: Thank you. So you think the same as I, that the strange frames only appear in the trace file. And the frames you posted in the picture of your updated answr are exactly the frames I have meant. (03 Aug '15, 00:26) Christian_R |

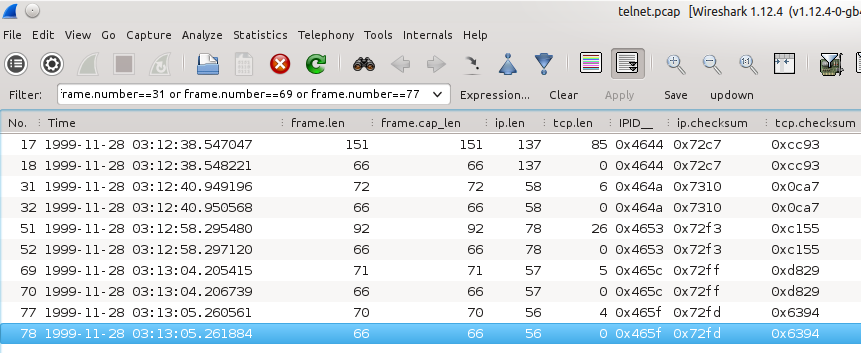 This seems to be a problem with the packet capturing tool (tcpdump on linux?).
This seems to be a problem with the packet capturing tool (tcpdump on linux?).
Could you post the packet on cloudshark or google drive so that it can be examined?
It is difficult to analyze with a screen shot.
https://drive.google.com/file/d/0B2E18hcsiwRnZ1U3UjFXSzVtcnM/view?usp=sharing