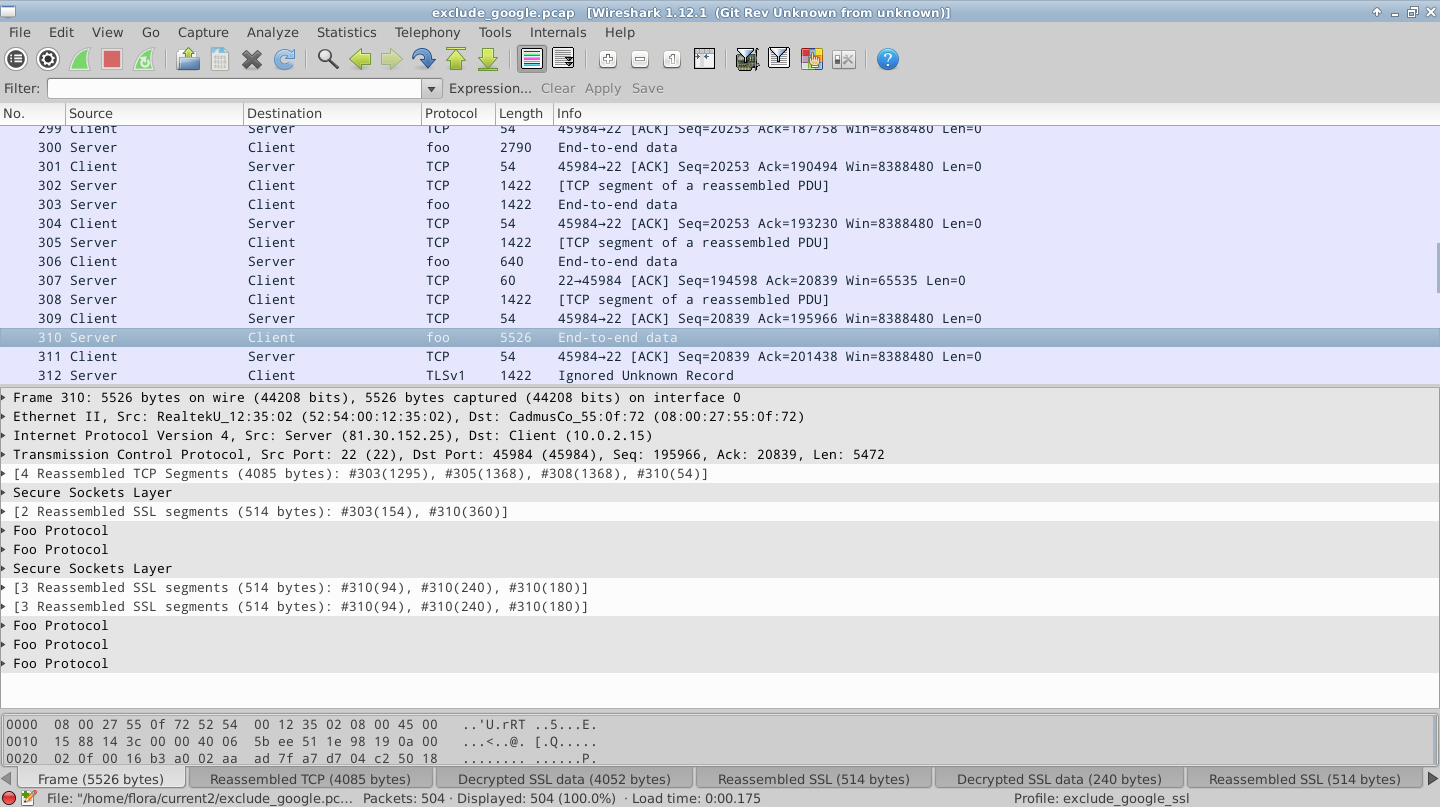
I'm developing a subdissector under SSL. When I test it, I found that most of the packets are dissected properly where some of them are dissected as "Ignored Unknown Record". I noticed these cases get (always) properly dissected: a single PDU embedded in a single SSL frame or multiple PDUs embedded in a single SSL frame. However, the case where a single PDU is a crosse multiple SSL frames is not (attached screenshot)! Dissection works fine if the next involved frame is a reassembled one (looks as "Application Data" in the Info column) but fails when it is a "[TCP segment of a reassembled PDU]". W]hen I tried to dissect the same dump without the related decryption keys, I found that the packets which appear as "[TCP segment of a reassembled PDU]" are the ones which dissected as"Ignored Unknown Record" when I use the keys. Based on that, I can only think there is something wrong with the reassembling but I'm not sure where? Here is my relate dump (no keys provided!) Part of My ssl_debug_file
asked 04 Aug ‘15, 09:18 flora edited 05 Aug ‘15, 05:54 |
This is a static archive of our old Q&A Site.
Please post any new questions and answers at ask.wireshark.org.