I am looking for a way to export single packets that have been decrypted with a wpa-pwd.
There is currently no such function in Wireshark for wifi decrypted frames. There is File -> Export PDUs, but that does not work for decrypted wifi frames.
What you can do:
File --> Export Packet Dissection --> as "C Arrays"- run a script (sample below) to convert that output to a format that text2pcap understands
Sample file:
https://wiki.wireshark.org/SampleCaptures?action=AttachFile&do=get&target=wpa-Induction.pcap
Example output of Export:
/ Decrypted CCMP data (631 bytes) /
static const unsigned char pkt439_1[631] = {
0xaa, 0xaa, 0x03, 0x00, 0x00, 0x00, 0x08, 0x00, / ........ /
0x45, 0x00, 0x02, 0x6f, 0x23, 0x5d, 0x40, 0x00, / E..o#]@. /
0x40, 0x06, 0x49, 0x07, 0xc0, 0xa8, 0x00, 0x32, / @.I....2 /
0x42, 0xe6, 0xc8, 0x64, 0xc9, 0xe9, 0x00, 0x50, / B..d...P /
0x71, 0x43, 0xd3, 0x97, 0x94, 0xfd, 0xd3, 0xe3, / qC...... /
0x80, 0x18, 0xff, 0xff, 0x45, 0xdc, 0x00, 0x00, / ....E... /
0x01, 0x01, 0x08, 0x0a, 0x03, 0x3a, 0x9f, 0x62, / .....:.b /
0x0d, 0x26, 0x71, 0x08, 0x47, 0x45, 0x54, 0x20, / .&q.GET /
0x2f, 0x77, 0x69, 0x6b, 0x69, 0x2f, 0x4c, 0x61, / /wiki/La /
0x6e, 0x64, 0x73, 0x68, 0x61, 0x72, 0x6b, 0x20, / ndshark /
0x48, 0x54, 0x54, 0x50, 0x2f, 0x31, 0x2e, 0x31, / HTTP/1.1 /
0x0d, 0x0a, 0x48, 0x6f, 0x73, 0x74, 0x3a, 0x20, / ..Host: /
0x65, 0x6e, 0x2e, 0x77, 0x69, 0x6b, 0x69, 0x70, / en.wikip /
Perl Script to convert that into text2pcap format:
my $n = 0;
while (<STDIN>) {
chomp;
next if (not /Decrypted CCMP data/);
while (<STDIN>) {
next if (/static const unsigned/);
last if (/^\}\;/);
s/\/\*.*$//;
s/\s+//g;
s/0x//g;
push(@hexdata,split(','));
}
# remove leading 8 bytes LLC
foreach (1..8) {shift(@hexdata)};
# print hex data in text2pcap format
while (@hexdata) {
printf "%06x ", $n;
foreach (1..16) { print shift(@hexdata) . ' '};
$n += 16;
print "\n";
}
$n = 0;
print "\n";
}
Run the perl script like this:
cat exported.c | perl convert.pl > exported.txt
text2pcap -e 0x800 exported.txt exported.pcap
Sample output of perl script: (text2pcap format)
000000 45 00 02 6f 23 5d 40 00 40 06 49 07 c0 a8 00 32
000010 42 e6 c8 64 c9 e9 00 50 71 43 d3 97 94 fd d3 e3
000020 80 18 ff ff 45 dc 00 00 01 01 08 0a 03 3a 9f 62
000030 0d 26 71 08 47 45 54 20 2f 77 69 6b 69 2f 4c 61
000040 6e 64 73 68 61 72 6b 20 48 54 54 50 2f 31 2e 31
000050 0d 0a 48 6f 73 74 3a 20 65 6e 2e 77 69 6b 69 70
000060 65 64 69 61 2e 6f 72 67 0d 0a 55 73 65 72 2d 41
000070 67 65 6e 74 3a 20 4d 6f 7a 69 6c 6c 61 2f 35 2e
000080 30 20 28 4d 61 63 69 6e 74 6f 73 68 3b 20 55 3b
000090 20 50 50 43 20 4d 61 63 20 4f 53 20 58 20 4d 61
0000a0 63 68 2d 4f 3b 20 65 6e 2d 55 53 3b 20 72 76 3a
0000b0 31 2e 38 2e 30 2e 39 29 20 47 65 63 6b 6f 2f 32
0000c0 30 30 36 31 32 30 36 20 46 69 72 65 66 6f 78 2f
0000d0 31 2e 35 2e 30 2e 39 0d 0a 41 63 63 65 70 74 3a
0000e0 20 74 65 78 74 2f 78 6d 6c 2c 61 70 70 6c 69 63
0000f0 61 74 69 6f 6e 2f 78 6d 6c 2c 61 70 70 6c 69 63
Resulting pcap file
only screenshot as cloudshark.org has closed the free public file upload.
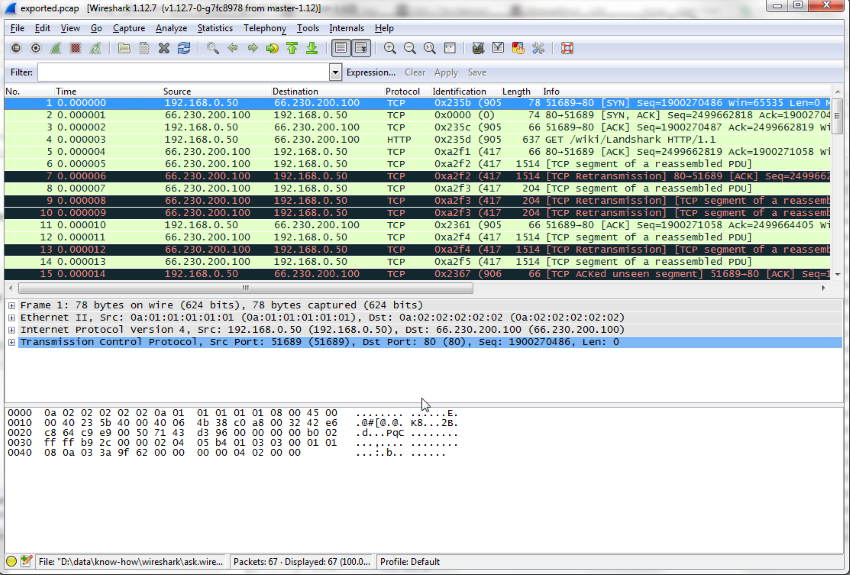
Regards
Kurt


voted for this answer because
as compared to the other one, it does not require to hand over the wpa "password" along with the capture, as I assume that avoidance of this need was the very goal of the exercise (leaving aside that I strongly suspect that if the wpa session has already been rekeyed since the EAPOL exchange took place, it would not work anyway)
it highlights things that are not obvious (i.e. that it depends on the output format choice whether deciphered packet contents can be exported or not)
I'm a perl fan myself ;-)