I am trying to capture only the EAPOL packets from my WLAN. I have read on the CaptureFilters wiki page that this should work with: But when i put that into wireshark it does not capture anything. So i played with the display filters, i think the equivalet there is: which also shows nothing on a data set that definitely contains EAPOL packets. Instead i could just set: as the display filter and it works perfectly, the right packets show up. Is it possible to set that somehow as capture filter? Bug in Wireshark or wrong filter? asked 03 Jan '16, 13:59 Jake edited 03 Jan '16, 14:02 showing 5 of 13 show 8 more comments |
One Answer:
I use ether proto 0x888e as a capture filter in Windump or tcpdump, such as: but it's really only good for the 4-way WPA handshake. Group rekeys are encrypted, so tougher to get. Share your trace and we can have a look. Exactly where do you put this filter when configuring?
If it is a trace with 802.11 headers, this will likely not work. Try: Without capture filter: With Capture filter in place: answered 03 Jan '16, 15:10 Bob Jones edited 04 Jan '16, 05:13 I put that into the display filter field (in the Wireshark gui), but eth.type was just a guess, i understand now that this is a other header and it works fine with llc.type. My question ist still how to set that as capture filter? (03 Jan '16, 16:45) Jake I just did a test on Windows with Wireshark - with a capture filter of ether proto 0x888e At the same time, I ran another Wireshark process but this time with no capture filter, with only a display filter of eapol and confirm both show the same exact packets. Note that the open capture had 40K+ total packets, displaying only 15, while the capture filter Wireshark only captured and display 15. If I can get a screenshot posted, I will do so. This is on a Windows7 system with AirPcapNx. (04 Jan '16, 05:07) Bob Jones Thanks for your effort! But i did the same test, my capture options are exactly the same as on the screenshoot and i get nothing. I tried some of the other capture filter presets and they all worked, even "ether proto" with other numbers (for example 0x0800 - IPv4). So is it a bug? Wireshark 2.0.0 (from the offical repo) on Manjaro Linux. (04 Jan '16, 08:11) Jake Tested on Kali2 w/ Wireshark 1.12.6 (whatever is in the repository) and it works as expected, just like my Windows screenshots. Maybe you found something with Wireshark2/Linux? (04 Jan '16, 08:57) Bob Jones Okay, so i tested it with Kali 2 and got nothing again... Then i found out that the wlan adapter has something to do with it: All the tests were on my Intel 3160, if i use a USB TL-WN722N instead i get at least some packets, but only 1-2 from a 4 way handshake (totally random which one), while the 2.Wireshark without filter captures all. (04 Jan '16, 10:37) Jake |

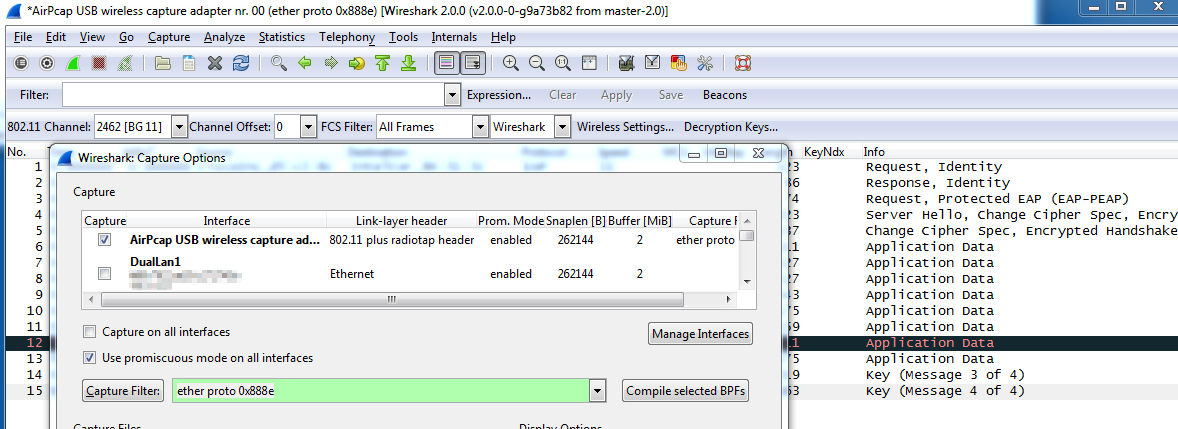
Do the packets you're capturing display in Wireshark/TShark with Ethernet headers or 802.11 headers? If they show 802.11 headers (from what is probably a monitor mode capture),
eth.typewon't be a valid field - you'll need to usellc.type, as Bob Jones indicated.If you use a display filter of
eapol:Yes, it is a wpa handshake with 802.11 headers from my card in monitor mode.
OK, so what are the OUI and PID values in the SNAP header for the EAPOL packets?
I am not sure what OUI/PID are, so here is the whole LLC header:
If you select the
Type: 802.1X Authentication (0x888e)item in the packet details pane, then, in the hex/ASCII dump pane, does it show data in the "Frame" tab or the "Decrypted WEP data"/"Decrypted CCIP data"/"Decrypted TKMP data" tab of that pane?What tabs? I see only these 2 bytes highlighted in the hex pane after selecting that.
The hex pane doesn't have two named tabs?
No. I dont have added any WPA decryption keys to the config so far, thats probably the reason.
Have you read the comments under Bob Jones Answer? An idea why is that?
So the frame you're showing hasn't been decrypted? And you're capturing in monitor mode? But when you capture with
ether photo 0x888e, packets like that one aren't captured?Yes, yes and yes. (*proto not photo)
(Damn you autocorrect!)
So, in the capture options dialog, is there a "Compile BPFs" or "Compile selected BPFs" button? If so, what gets shown if, before starting a capture with the filter
ether proto 0x888e, you push that button? It should pop up a window with text; what's the text?(Why won't OSQA allow a comment to begin with fixed-width text?)
(Why does it always change the layout after posting?)
Because it assumes most of what you're typing is free-form text, which it wraps. If you want fixed-formatted text, you either need to put it in backquotes or begin each line with 4 spaces. (And you can't begin a comment with a 4-space indent, which is why I added the parenthesized note to your comment.)