I have a tcp capture - it appears to be completely duplicate. In other words, the client sends a SYN followed by a second SYN within a different frame 206/207, same time stamp in both frames, TSVal is same for both frames. The SYN, ACK is frames 212, 213 ( for 206, 207 ) Frame 214 ACK's frame 206 Frame 215 Dup ACK's (frame) 214#1 This duplication process continues for the conversation. It appears the TCP conversation is occurring twice on the same socket. The second conversation seems to be marked as 'DUP' all the way through. I added two screen shot- it seems the upload truncated the img This continues for the entire 100 meg transfer.. Thanks in advance for assistance jim asked 22 Jan '16, 12:22 JimSax
|
This is a static archive of our old Q&A Site.
Please post any new questions and answers at ask.wireshark.org.

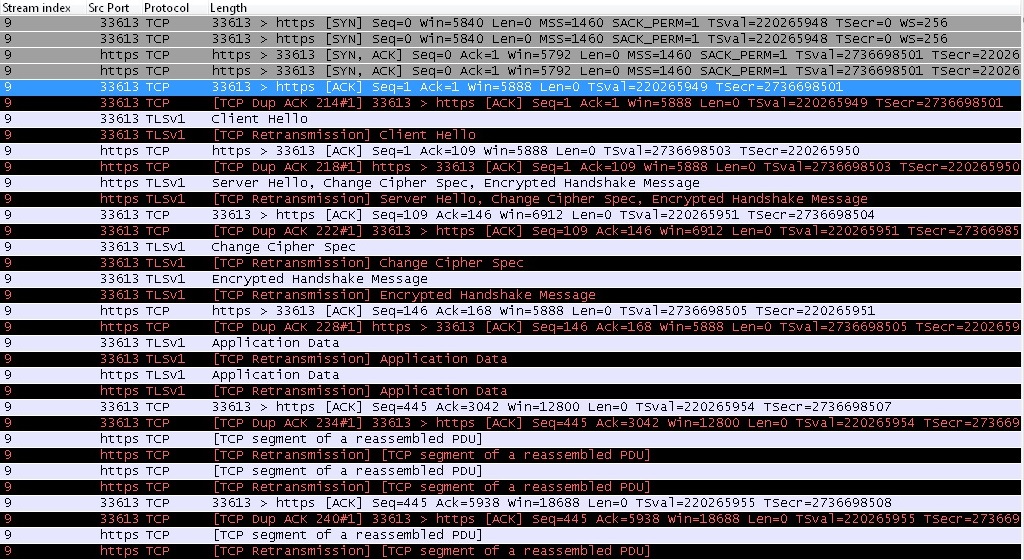
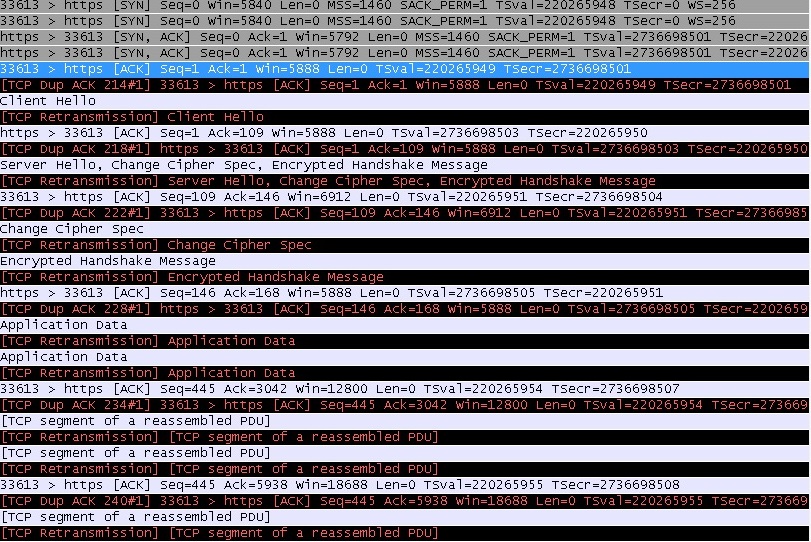
Seems to me like a wrong setting of monitoring on a switch, can you provide more details on how the capture has been taken? Are the source and destination MAC addresses of the two packets (the original and the duplicate) also the same? Are there any sessions in the same capture which don't show this anomaly?
Sindy, thanks for weighing in, further analysis on my side showed multiple webservers running. I cannot explain this yet, but shutting down one of the webservers removed the duplicate issue. The server is rhel 6 with multiple IP addresses, so a bit more analysis to do here. I cannot say I have ever seen a duplicate conversation such as this.... perplexing, but interesting.
As @sindy already told you, you should find the root cause for this behaviour at least to be able to explain this behaviour for yourself.
If you then need to deduplicate a trace like this you could use editcap with the option -D. Editcap is part of the wireshark distribution. The man page can be found here: https://www.wireshark.org/docs/man-pages/editcap.html