I have a customer who is trying to establish a TLS connection to my server. They have loaded my certificates and the certificate exchange appears to be working properly. However, their client does not send data after the server has ACKed the clients Encrypted Handshake Message. Link to pcap added. link text Anyone have any ideas why the client wouldn't be sending application data? asked 13 Sep '16, 11:35 RFB edited 14 Sep '16, 09:55 |
One Answer:
If you look at the source address of the TCP RST, you will notice that it matches the IP address of the server (based on the source of the Server Hello). There are multiple strange things about your report:
Check:
answered 13 Sep '16, 15:26 Lekensteyn |

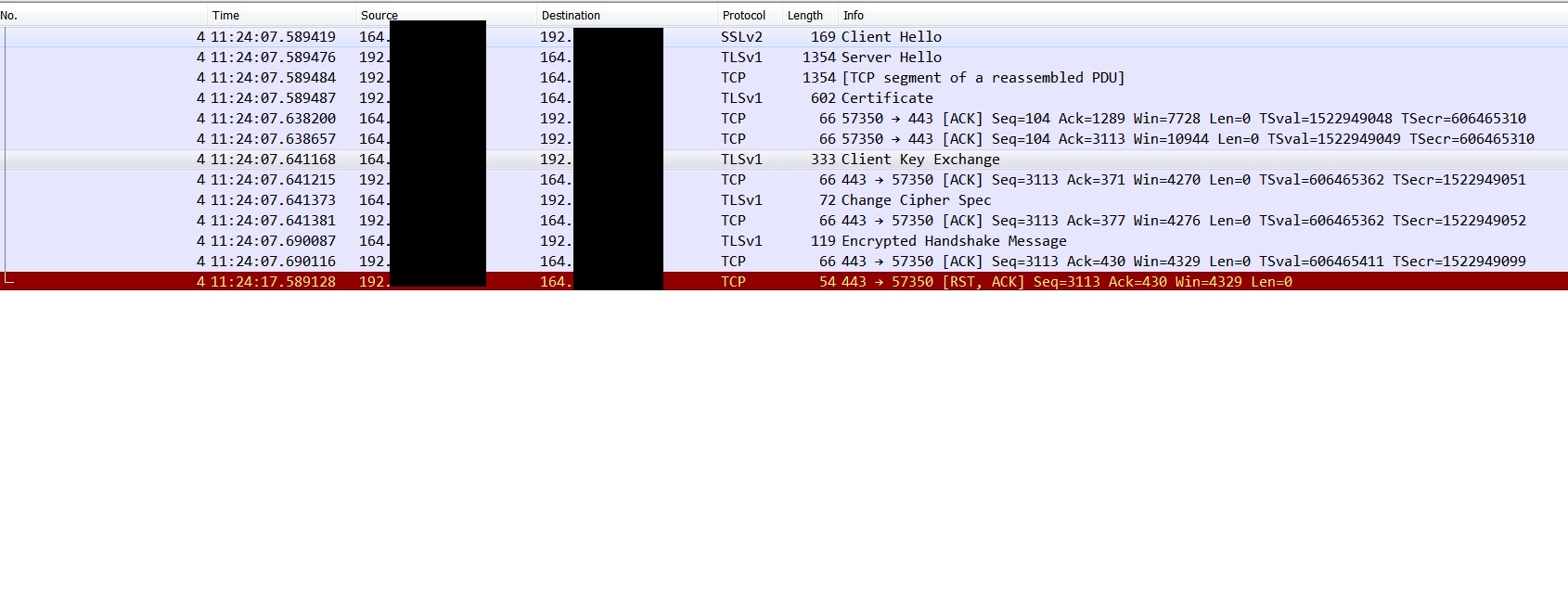
For better help you should include a packet capture file, not just a screenshot.
Added link to pcap in original post.
The pcap strengthens my analysis below, SSLv2 was killed long time ago. Your client should not send a SSLv2-compatible hello message. Btw, the Certificate message contains the hostname of your server which is not anonimized.