According to this and this, Wireshark should have a HTTP2 dissector. Since I couldn't found "HTTP2" option under "Protocols", is there a way to install HTTP2 dissector? I'm using Version 2.2.0 (v2.2.0-0-g5368c50 from master-2.2) on Mac. BTW why don't I have http2 option by default? Edit
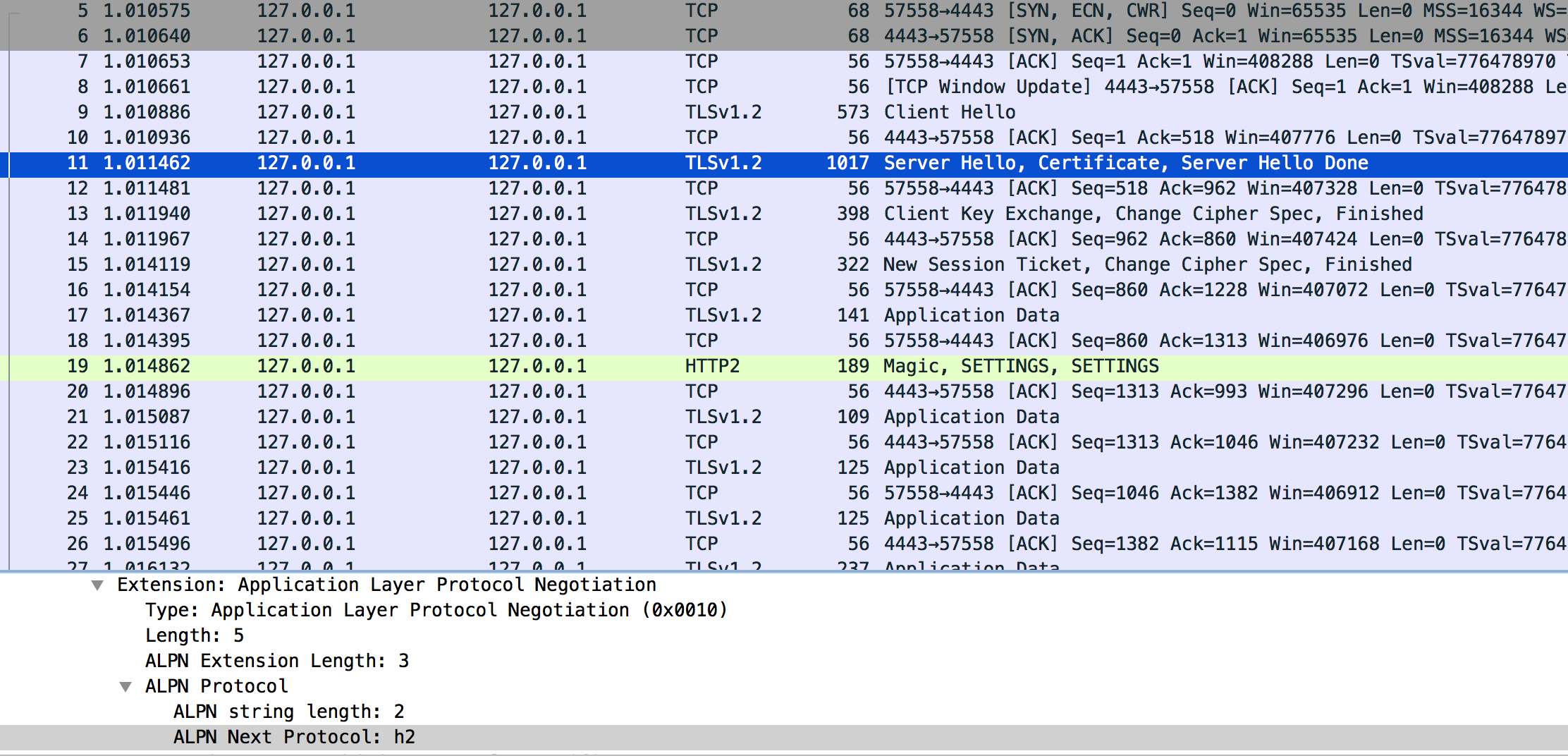
You can download pcapng file here The issue is that many HTTP/2 packets are not recognized as HTTP/2, I'd expect to see something like this, which is the output visiting from browser and decrypting using SSLKEYLOG: asked 21 Sep '16, 10:12 laike9m edited 24 Sep '16, 04:45 |
One Answer:
If you looked under Preferences for the HTTP2 dissector, you won't find it there because the HTTP2 dissector has no configurable preferences. You can find protocols at Analyze -> Enabled Protocols..., there I certainly see the HTTP2 dissector. It was already added in Wireshark version 1.12. answered 21 Sep '16, 14:01 Lekensteyn Thx Lekensteyn, you're right. Do you know how WIreShark recognize HTTP/2 packet? Some of my packets are recognized as HTTP/2 packets, but "TLSv1.2". (23 Sep '16, 16:41) laike9m @laike9m You have encrypted HTTP/2 traffic without keys, so Wireshark cannot decrypt it. Look for the "SSLKEYLOGFILE" method to learn more about decrypting such traffic. (24 Sep '16, 02:30) Lekensteyn @Lekensteyn Well in fact WireShark can decrypt it(I can see the decrypted data), but just won't dissect it as HTTP/2. I'm going to read some source code to find out. (24 Sep '16, 02:34) laike9m Normally, Wireshark indicates the highest layer protocol which it could dissect in the frame. Therefore, if a single http2 pdu is split into several frames, only the last one of them is marked as containing http2, and all the ones before are only marked as containing the transport protocol, which is TLSv1.2 in this case. If this is true, you should see a second tab in the "packet bytes" pane of the frame marked as http2, which has more bytes than the frame, because it contains the http2 payload reassembled from all the frames into which it was split. (24 Sep '16, 02:44) sindy @laike9m Wireshark recognizes that some traffic is HTTP/2 based on the indication in the ALPN/NPN TLS Hello Extension (identifier "h2") or using heuristics (a magic string before the body). (24 Sep '16, 02:47) Lekensteyn @Lekensteyn ALPN is h2, you can see in the screenshot above. (24 Sep '16, 02:56) laike9m @laike9m Could you also upload a capture file? Maybe you have a situation like Sindy described, or you have encountered a bug in the SSL/HTTP2 dissectors. (24 Sep '16, 03:00) Lekensteyn @Lekensteyn uploaded. (24 Sep '16, 03:26) laike9m @laike9m Do you happen to have the SSL keys (premaster is sufficient, via File -> Export SSL session keys) for this session as well? (24 Sep '16, 03:38) Lekensteyn This is the self-gen cert and key that I used, http://www.filedropper.com/certkey. I didn't (and don't want to) visit the server using browser but using a h2 command line tool. Not sure what premaster is but these are all I have, BTW cipher algorithm is AES256-SHA, which I know is not suitable for h2 communication, but I since I don't want to use SSLKEYLOG and browser, I have to use non-DH cipher. But I've also tested the browser&SSLKEYLOG way, WireShark works in this case. (24 Sep '16, 03:54) laike9m premaster was the wrong terminology, I meant SSL session keys. With your provided sample pcap and keys I can successfully decrypt and see the HTTP2 packets (tested with Wireshark 2.0.5 and the one from git master). What is exactly the issue you are observing? (24 Sep '16, 04:07) Lekensteyn @Lekensteyn In the screenshot I post, HTTP/2 packets are not recognized as HTTP/2, or do you think that's the expected output? See updated question. (24 Sep '16, 04:41) laike9m Found a similar issue here: https://ask.wireshark.org/questions/41458/unable-to-decode-http2-traffic, but in version 2.2.0 there's no Enable HTTP2 heuristic option. (24 Sep '16, 05:42) laike9m @laike9m The previous heuristics was very weak and got removed in 2.0. It looks like there are issues when you specify "http" as protocol in the RSA keys dialog. Try specifying "http2" instead. Note the "Application Data Protocol" in the SSL tree, if it says "http-over-tls" (or something like that), it seems to have the issue of not invoking the http2 dissector. (24 Sep '16, 05:53) Lekensteyn There was a bug that broke ALPN matching, it will be fixed by https://code.wireshark.org/review/17907 (will probably be backported to the next versions, 2.2.1 and maybe 2.0.7). (24 Sep '16, 06:20) Lekensteyn @Lekensteyn Yeah specifying http2 works well. (24 Sep '16, 13:01) laike9m showing 5 of 16 show 11 more comments |

do you use profiles?
if you go to
Analyze->Enabled Protocolsand fillhttpinto the search field at the bottom, is the HTTP2 above ticked?