I am using an app which says it uses ssl v3 to transporrt data. After running an ssl test I see that the server supports tls 1.1,1.2 and ssl v3 so I open Wirehsark and connect iphone with it by rvi setting. In that it says the protocol being used is tcp and then http. I'm confused. I basically want to find which cipher suite is being used. Is it possible to find this out? asked 18 Jun '17, 04:03 bangbam edited 19 Jun '17, 13:52 cmaynard ♦♦ |
One Answer:
You may have already seen this resource, but others may find it useful: "Getting a Packet Trace" from Apple's Developer Technical Q&A: https://developer.apple.com/library/content/qa/qa1176/_index.html#//apple_ref/doc/uid/DTS10001707-CH1-SECIOSPACKETTRACING (This covers both MacOS and iOS) I don't have a Mac, but the linked document suggests that an rvi interface can be treated pretty much like any other...I don't know how well Wireshark supports capturing on rvi interfaces, so you can use tcpdump. If your RVI is set up and started properly, you should be able to use tcpdump to capture only SSL/TLS traffic by specifying TCP port 443, like so (rviX is your RVI interface): sudo tcpdump 'tcp port 443' -i rviX -w mytrace.pcap [run your tests] [end tcpdump] If you want to capture both HTTP and HTTPS traffic, try: sudo tcpdump 'tcp port 80 or tcp port 443' -i rviX -w mytrace.pcap [run your tests] [end tcpdump] Once you have this pcap file, you can load it in Wireshark and identify cipher suites as follows: 1) Use Statistics->Conversations (in the main menu) to list conversations contained in the capture file, like so: 2) Highlight the specific conversation in which you're interested, and use 'Follow Stream' in the Conversations dialog to display that conversation. Dismiss the 'raw data' display that pops up; we won't need that for what we're doing. 3) In the the main Wireshark display:
answered 23 Jun '17, 10:48 wesmorgan1 edited 23 Jun '17, 14:39 |

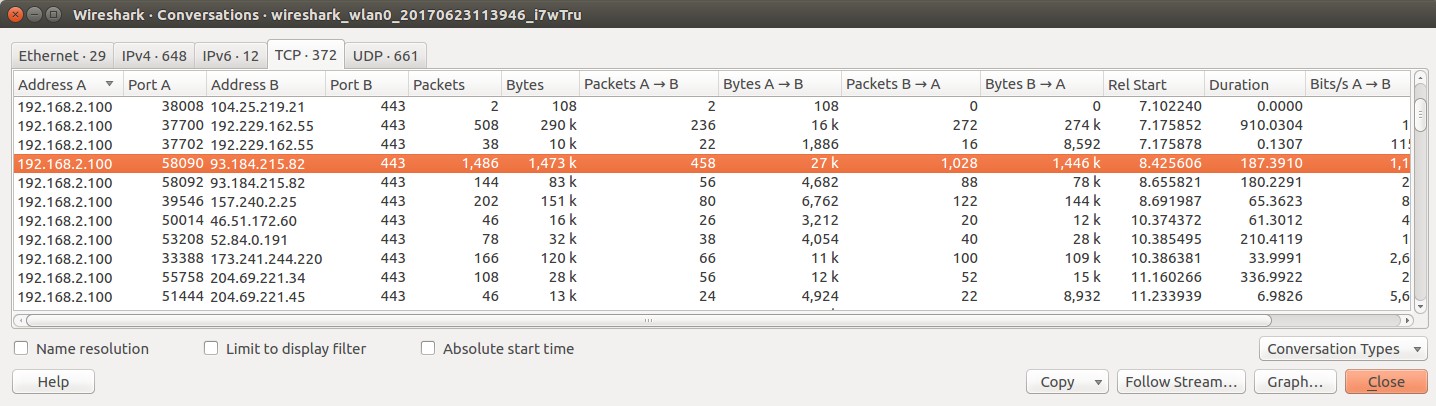
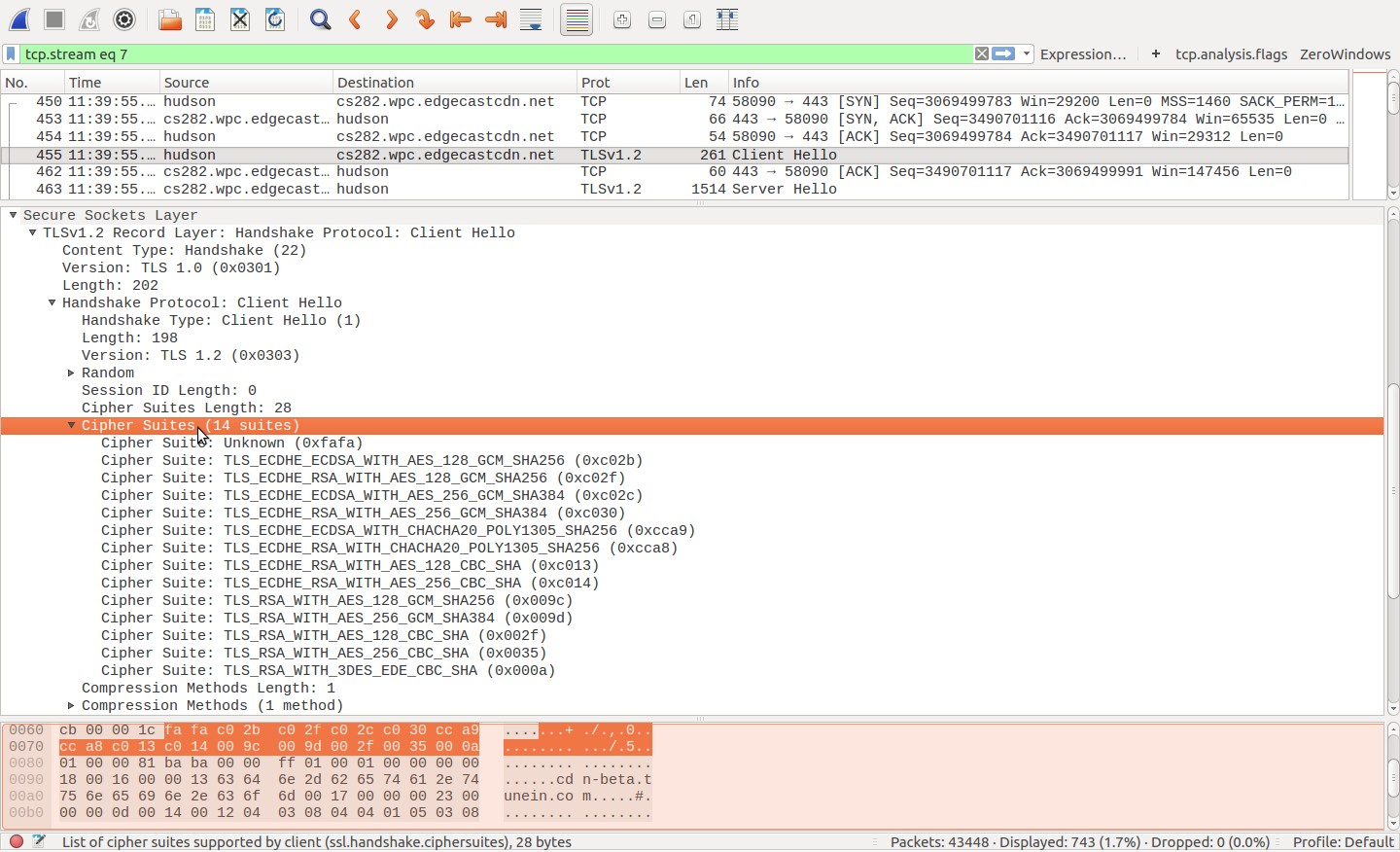
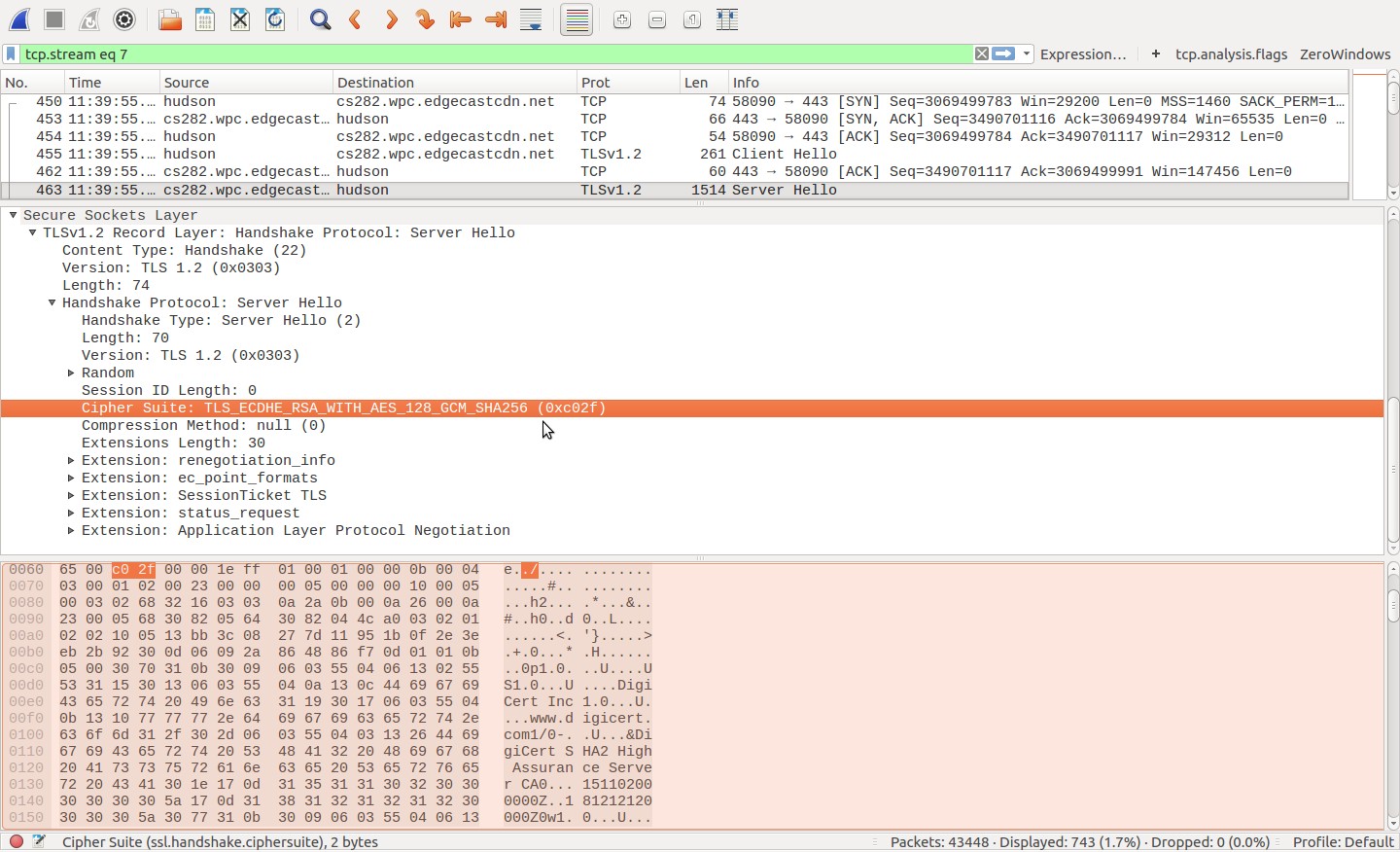
I don't think you've actually captured the SSL traffic. Are you capturing on the right port? Maybe visit the Wireshark SSL wiki page for more information?
ok then how can i determine which protocol is being used