I'm having an issue with failed SMB communications and cannot determine the source of the response behavior from a Windows 7 PC. Was hoping that anyone might be able to help. Here's the response packet: No. Time Source Destination Protocol Info 1425 34.647499 192.168.1.74 192.168.1.68 SMB Negotiate Protocol Response Frame 1425: 475 bytes on wire (3800 bits), 475 bytes captured (3800 bits) Ethernet II, Src: Dell_24:7e:41 (00:21:9b:24:7e:41), Dst: Xerox_c3:73:c7 (00:00:aa:c3:73:c7) Internet Protocol, Src: 192.168.1.74 (192.168.1.74), Dst: 192.168.1.68 (192.168.1.68) Transmission Control Protocol, Src Port: microsoft-ds (445), Dst Port: 60933 (60933), Seq: 1, Ack: 195, Len: 409 NetBIOS Session Service SMB (Server Message Block Protocol) 0000 00 00 aa c3 73 c7 00 21 9b 24 7e 41 08 00 45 00 ....s..!.$~A..E. 0010 01 cd 41 9e 40 00 80 06 00 00 c0 a8 01 4a c0 a8 [email protected] 0020 01 44 01 bd ee 05 31 a6 d8 8b 95 e2 ce 1c 80 18 .D....1......... 0030 01 04 85 9e 00 00 01 01 08 0a 00 0d 45 17 00 03 ............E... 0040 f3 e9 00 00 01 95 ff 53 4d 42 72 00 00 00 00 88 .......SMBr..... 0050 01 c8 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0060 4e 03 00 00 01 00 11 09 00 03 32 00 01 00 04 11 N.........2..... 0070 00 00 00 00 01 00 00 00 00 00 fc e3 01 80 f1 99 ................ 0080 ad 07 98 4f cb 01 2c 01 00 50 01 40 de 4e df 0e ...O..,[email protected] 0090 59 3b 48 bd 5f 89 c6 ca bd 06 05 60 82 01 3c 06 Y;H._...... The Win 7 machine appears to be asking the client to begin signing but I've tried everything I can think of to simulate this behavior - Security Policies, Lanman registry edits, etc. to no avail. Successful communication does not include the mechToken in the security blob. When we see this, all comms stop. Does anyone know what can cause this behavior? Any assistance will be greatly appreciated. Thanks! asked 30 Nov '10, 10:15 MarkMcD |
One Answer:
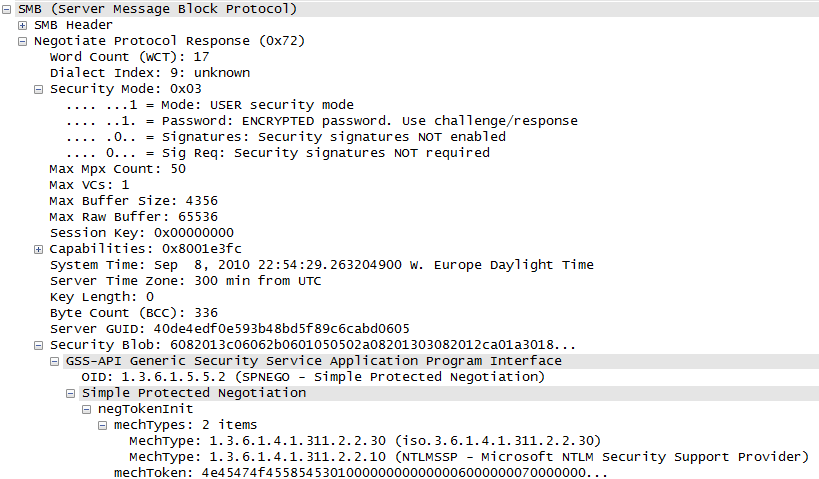
I converted your hex dump to a trace file to get this SMB decode of your packet:
The interesting part is the server offering two authentication mechanisms to the client: The well understood NTLMSSP or a less known mechType 1.3.6.1.4.1.311.2.2.30. This mechtype can be found in a patent filed by Microsoft. The text can be found here It looks like the the "Microsoft live sign-on assistant" tampers with the SMB authentication. One report is found in a technet forum A topic in the discussion shows reads For reference, please see the following samba bug report: https://bugzilla.samba.org/show_bug.cgi?id=7577 Alas, your post does not state the client OS. Given the postings I would not be surprised to hear that it's a samba client. The obvious solution would be a) to uninstall the Live sign-on assistant or b) apply the fix to the samba client answered 07 Dec '10, 13:54 packethunter edited 07 Dec '10, 14:52 |

Wow..packethunter, talk about going the mile! (converting it to pcap, I mean)