I have Wireshark installed in two laptops, one injecting custom packets into the network and another sniffing these injected packets. When I transmit the packets using the fist machine (Macbook Pro using Broadcom BCM 4331 interface card), I am able to see these packets in Wireshark with all the various fields such as SSI, Noise etc. But the Wireshark installed on the other machine (Dell Latitude E6410 using the Intel Corporation Centrino Ultimate-N 6300 interface card) shows the radio-tap header to be of length 18 only, and is missing parameters like Noise and timestamp. Could anyone explain why this is happening? Is it because different wireless drivers treat radio-tap in a different way? If so, how can I get the missing parameters like background noise? I have attached screen-shots of wireshark running on the two machines.
asked 18 Jun '12, 15:58 hektor edited 18 Jun '12, 19:04 cmaynard ♦♦ |
One Answer:
Some wirless network interaces do not make the additional information available. The details are dependent on the OS involved, the Wireshark version, and the mode you have set up in the interface. There is a good discussion at http://wiki.wireshark.org/CaptureSetup/WLAN#Link-Layer_.28Radio.29_packet_headers which should get you started. answered 18 Jun '12, 16:38 inetdog |

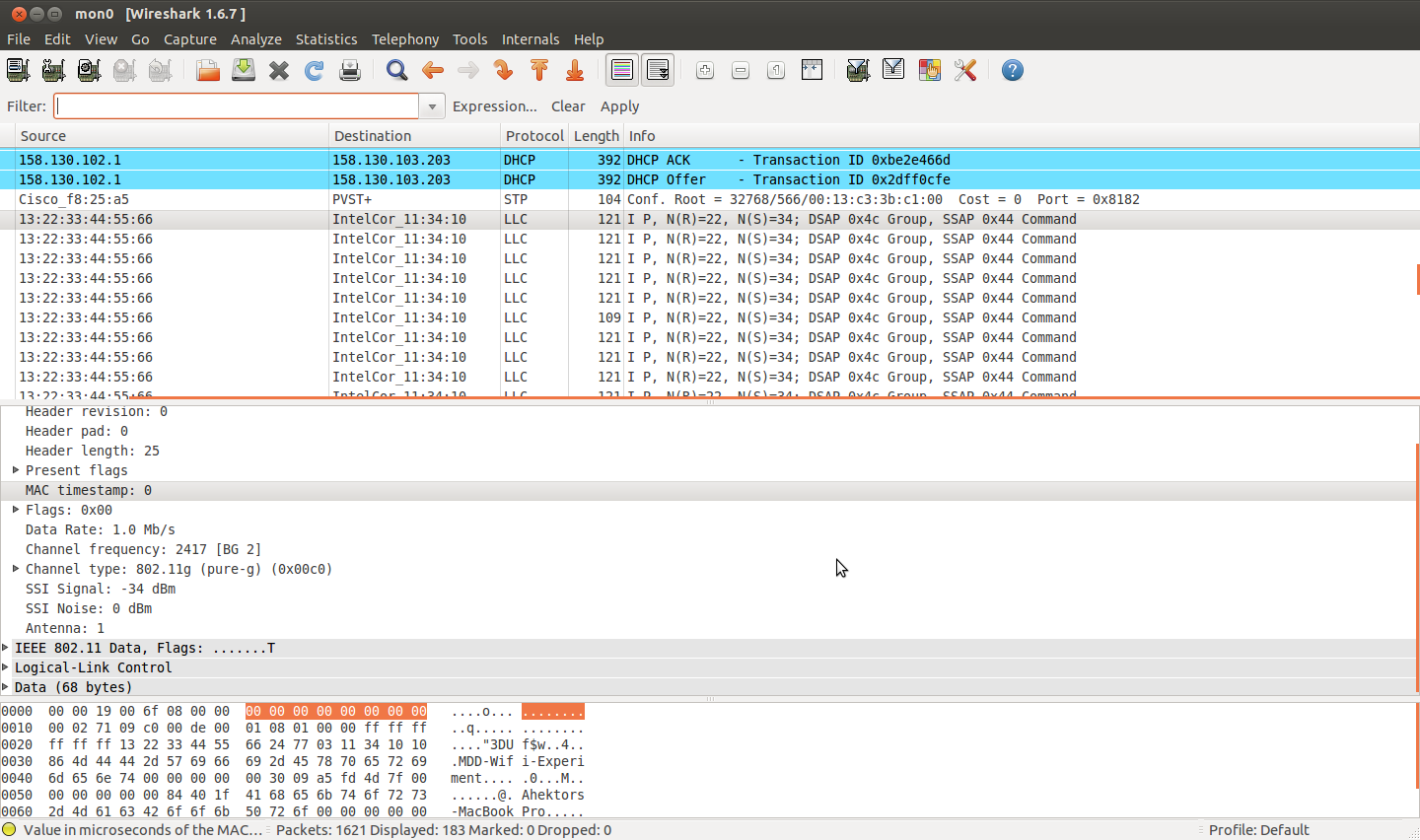
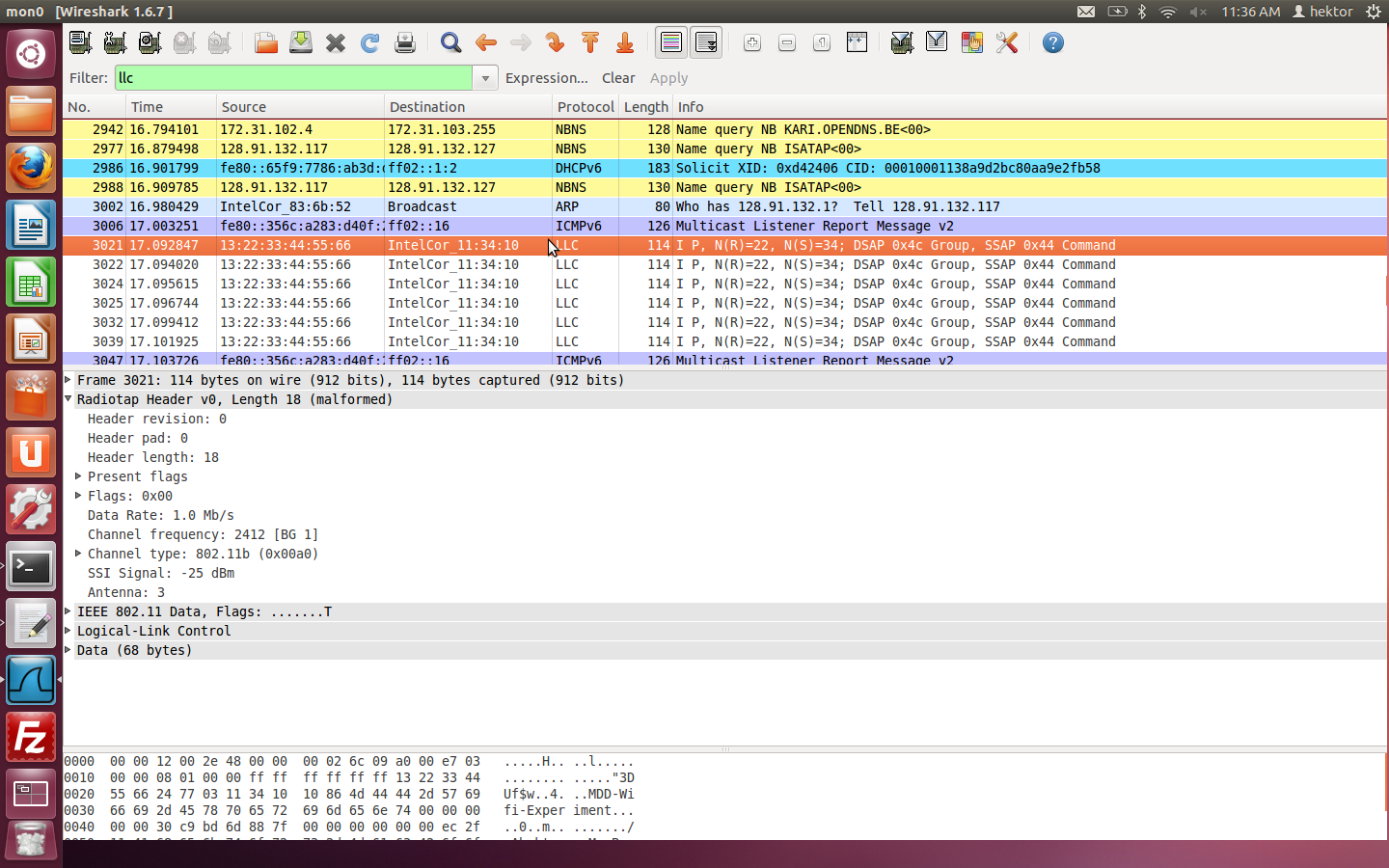
I am using airmon-ng to create the monitor interface and inject packets through it. All packets sniffed through the monitor interface in Wireshark running on the receiver machine show the radio-tap header to be malformed. I'm not sure whether this is a problem in the way i am constructing the packet using the radio-tap and ieee80211 headers. If it was, the packets wouldn't be able to go through right? Or could it be some sort of bug in Wireshark?
If the additional information is not available through Wireshark, is there another way through which i can determine these paramters?