wireshark says this packet is malformed but our engineers agree it is ok so what do I do ? Should I raise a bug ? Packet 1833 - look at ptp section, I've highlighted the lengthField (you can see this in the bytes at the end as well). Apparently it is malformed after there - however when we look at the 1588 ptp spec it all seems to be ok. asked 05 Jul '12, 03:47 adetheheat showing 5 of 11 show 6 more comments |
One Answer:
Please raise a bug at the Wireshark Bugzilla database, with references to the protocol specification and a sample capture illustrating the issue. If the capture contains information that you don't want made public, mark the bug as private (Advanced fields) to restrict access to the capture to core developers. answered 05 Jul '12, 04:00 grahamb ♦ |

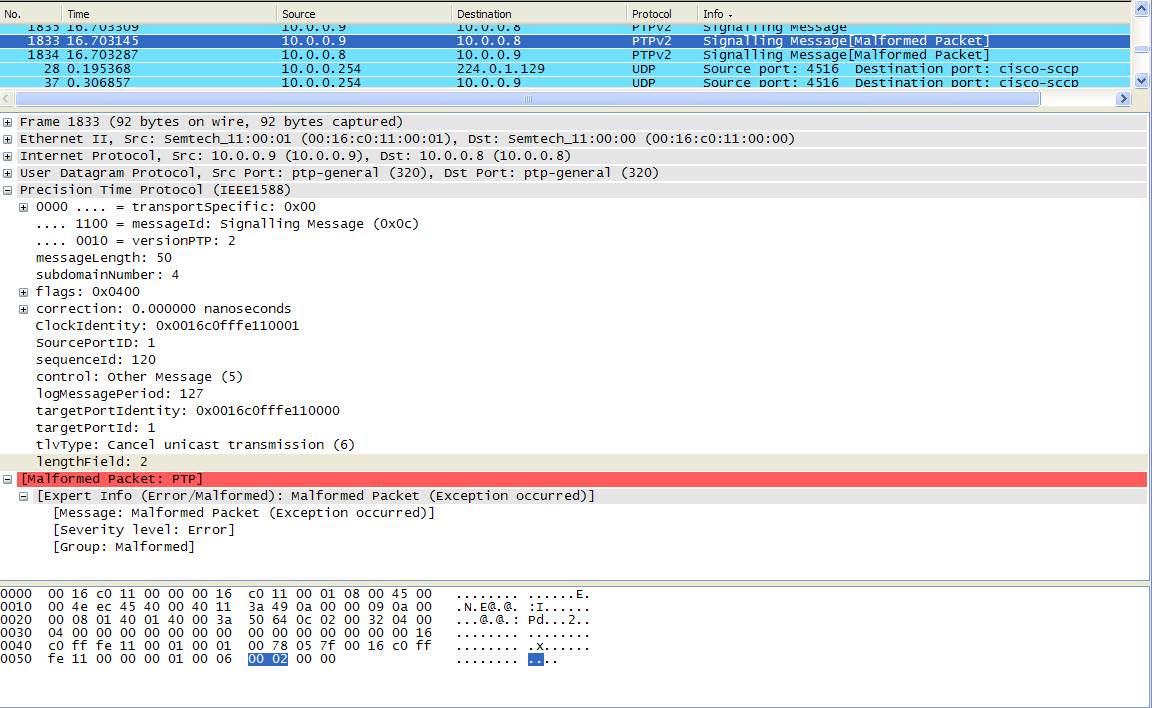
what are the last two bytes 0x00 0x00?? They don't get dissected.
in the 1588 standard they say the 1st of the 2 bytes is 4 bits is the message type (should be 0 in my case) and the next 4 bits is reserved. The 2nd byte is also reserved. So 00 00 is correct
it also says the length should be 2. Section 16.1.4.3 of ptp standard
for CANCEL_UNICAST_TRANSMISSION TLV specification
can you provide a free link to the specs?
Attached is the spec for the tlv bit at the end taken from the ptp 1588 standard: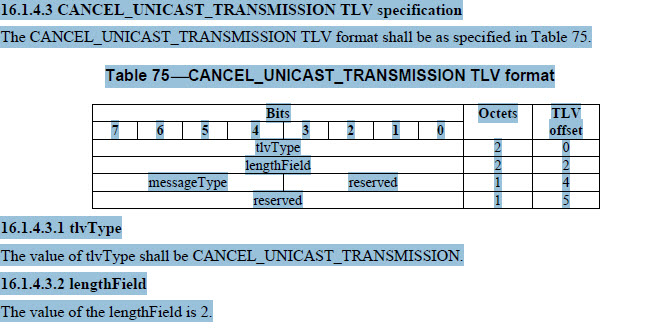
16.1.4.3.3 messageType (Enumeration4) The value of messageType shall indicate the type of unicast message transmission to be canceled. The coding of the enumeration is identical to that used in the messageType field of message headers; see 13.3.2.2 (below):
Message type Message class Value (hex) Sync Event 0 Delay_Req Event 1 Pdelay_Req Event 2 Pdelay_Resp Event 3 Reserved — 4-7 Follow_Up General 8 Delay_Resp General 9 Pdelay_Resp_Follow_Up General A Announce General B Signaling General C Management General D Reserved — E-F
can't do that I'm afraid. I've got a bug report raised about this - it's sort of already known about from the replies I've got so far.
Bug raised so won't be updating this thread further
For the record, the bug ID is 7437 and the difficulty in fixing it is the lack of free access to the spec. I think that adetheheat has provided enough info to fix this though.
google:
"16.1.4.3" ptp-> 2nd link ;-)