I have Wireshark 1.8.3 on two machines, one a Win7 x64 box and the other Win XP SP3 (32-bit). Between 1 and 3 times per day the Win7 X64 machine tries to connect to TCP port 61899 of www.wireshark.org (174.137.42.75). My routers firewall blocks these attempts but WTF? Is there some option to disable this "phoning home"? BTW Wireshark is NOT running during these attempts. asked 08 Nov '12, 05:57 AnnoyedOne edited 08 Nov '12, 05:58 |
2 Answers:
I don't think that there is such feature in Wireshark itself (at least I cannot find anything in the source code). Furthermore: If Wireshark is not running how could it cause those requests? Most certainly something else on your system tries to create that connection (maybe a browser). INTERESTINGLY that port (61899) is actually open on www.wireshark.org and if you connect to it with a browser, you will see something that's called Riverbed FlyRUM. What is this??
UPDATE: It's javascript code hosted on www.wireshark.org that connects to that port. As soon as you browse to www.wireshark.org, the script in your browser tries to establish a connection to that port. So, my first assumption (see above) was right. So, NO Wireshark is NOT phoning home! Regards answered 08 Nov '12, 06:08 Kurt Knochner ♦ edited 08 Nov '12, 07:11 |
Current and past versions of Wireshark shouldn't phone home on their own. A future version might do so if we ever get around to adding a "check for updates" feature. The connections to www.wireshark.org:61899 and the page that Kurt found are for upcoming Riverbed product enhancements (called FlyScript) that a team is working on inside Riverbed. They needed a real-world environment for testing and I agreed to let them use the Wireshark web servers. They aren't quite ready for public consumption and a team of sharks equipped with lasers will be visiting Kurt momentarily. As The 1x1.gif URL implies, it's a beacon used to measure the performance of connections to www.wireshark.org. It isn't used to track visits beyond www.wireshark.org and it's not really accurate to call it a tracking/web bug. I use Google Analytics on the various wireshark.org sites and have used WebTuna in the past. Both use "web bugs" in the traditional sense. @AnnoyedOne Can you confirm whether or not you had www.wireshark.org open in a browser when the connection to www.wireshark.org:61899? It might be helpful to the team developing the new feature set. answered 08 Nov '12, 10:33 Gerald Combs ♦♦ edited 08 Nov '12, 10:42 1 no time... sharks everywhere ... two of them eliminated ... fire, fire! see you tomorrow.. HOPEFULLY !!! (08 Nov '12, 18:56) Kurt Knochner ♦ @Gerald Combs It took me a few days of Googling etc to figure out, thanks to Kurt, that it was the Wireshark website trying to use port 61899. It was difficult to determine that because my router is configured to send me warning email when something attempts to use a non-standard and/or non-allowed port. Those log only told me what machine was sending the requests not what process/webpage etc. I've now configure my router to silently drop all www.wireshark.org:61899 attempts. Please allow any auto-update feature to be disabled. And I mean off-entirely. No phoning home. (09 Nov '12, 08:07) AnnoyedOne |

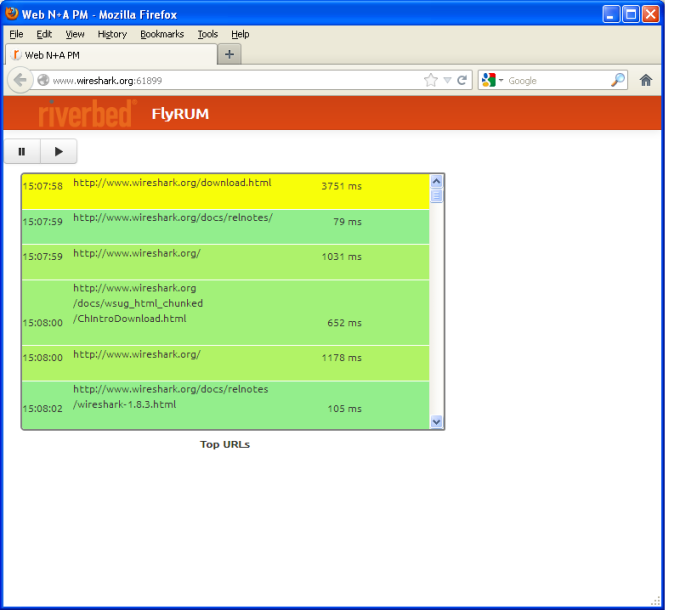
Thanks for that.
http://www.wireshark.org:61899/beacon/1x1.gif
That'll be (silently) blocked once I post this.
looks like a tracking/web bug.
Yup. That bug is now "squashed" :-)