In the same way "Follow TCP Stream" joins packets for easier analysis. Is there a way to follow HTTP redirects without doing it manually?
asked 01 Dec '13, 11:31 elgalu edited 01 Dec '13, 11:32 |
One Answer:
Wireshark does not provide that functionality and it would be hard to implement for several reasons (see also the comment of @Guy Harris). In some cases you will see the redirect and the following request in the same TCP connection, if the client uses HTTP/1.1 and it reuses the same connection to the same server. However, as shown in your example, there can also be redirects to a different host (request: rubygems.org, redirect: production.s3.rubygems.org), hence the client must use a different TCP connection. What you can do is to support the manual process as much as possible, with the features/tools Wireshark provides (and/or tshark)
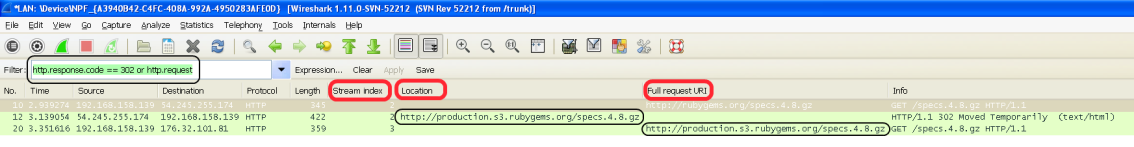
The whole thing will look like the following screenshot
The filtered frames will show the redirect and (in most cases) directly following the request to the redirected page. If there is a lot of traffic, you could further filter the requests, based on client IP (ip.addr) and User-Agent header (http.user_agent). Then simply take the TCP stream values and build your next filter:
Unfortunately you still can't 'follow' both streams at once, but at least you will be able to do the manual analysis a bit faster ;-)) You can to the same thing with tshark and some scripting! As an alternative, you could write a Listener/Tap (in C or Lua) and filter things there, but that's quite some work to do, and probably not worth the time, if you don't have to follow hundreds of redirects per day. Regards answered 02 Dec '13, 13:46 Kurt Knochner ♦ edited 02 Dec '13, 13:52 |

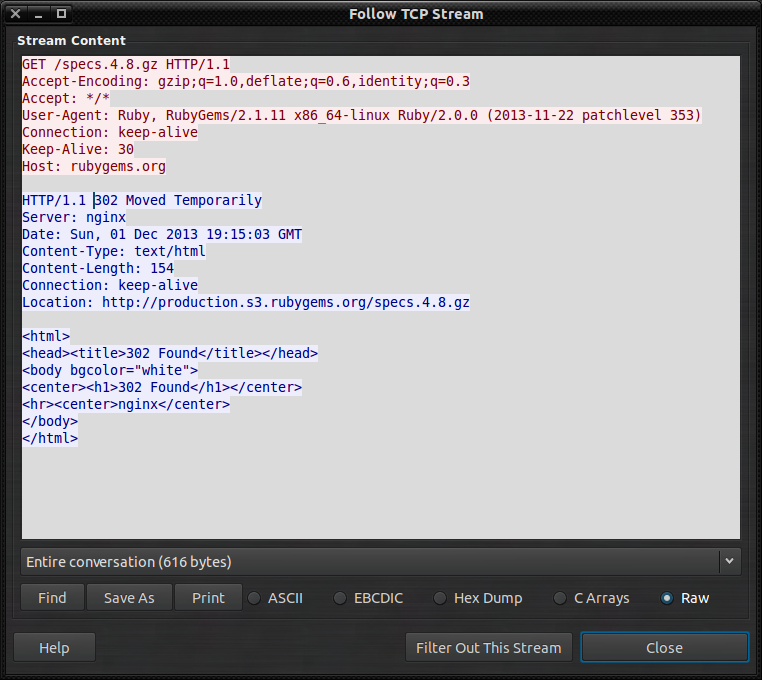
...because it's a network analyzer, not a Web browser or other Web client. It shows you what happened on the network, and if the program that sent the request that got the redirect didn't follow the redirect, then following-the-redirect didn't happen on the network.
Very helpful and detailed small guide! Thanks!!!