Hi guys, I am trying to connect to a public webservice, which requires from its clients to have their own certificate. The whole communication is secure. So I think we could talk about the Client-authenticated TLS handshake. The certificate is installed on the machine (Local Computer and User). It is verified from a CA. But it seems to me, that the client does not send any client certificate, I have tried it in a browser and programatically:
asked 03 Dec '13, 07:37 thespycry |
2 Answers:
The server does request a certificate, which you can see with a display filter (ssl.handshake.type == 13), in the Info column of the Server Hello (Certificate Request) or with OpenSSL. HOWEVER: Your request is sent through a Proxy (CONNECT method used). If that is a 'simple' proxy, than it would be no problem to forward the client cert request to the browser. If you don't see the client cert request in the capture file (ssl.handshake.type == 13), then your proxy is (most certainly) intercepting SSL/TLS connections to scan the content, which is quite common in corporate environments. In that case it is impossible/hard to forward the client cert request to the client. The 'better' proxy products (means more expensive) do offer a workaround for this problem. On those devices you can store a client cert (plus key) and the proxy will answer the client cert request on behalf of the client, with the stored credentials. Please ask your proxy admin:
If your proxy is not able to handle client cert requests, there are two workarounds
Regards answered 04 Dec '13, 03:44 Kurt Knochner ♦ edited 04 Dec '13, 03:47 |
I don't see a "Certificate Request" sent by the server therfore the client doesn't send its certificate. answered 03 Dec '13, 08:33 mrEEde OK the question is, why isn't the server requesting the certificate ? what reason could it have? (04 Dec '13, 00:05) thespycry |

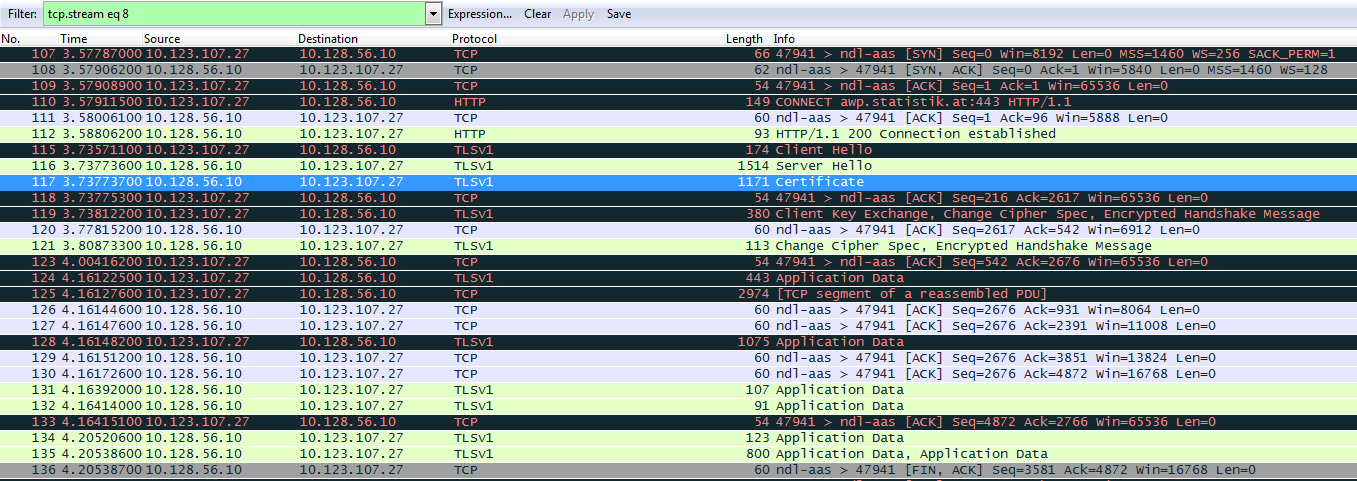
alright, so if I understand correctly, we see the cert request from server while using the openssl command, because we are on the one side of the ssl 'tunnel'. We do not see it with wireshark, because we are only intercepting a ssl connection. So, YES, the server always sends the client cert request, but it does not come through the proxy so it seems, like the server isn't asking.
erm... no. I can see the client cert request, because I am accessing the target server via the internet, without proxy.
Yes. And, if you would have used openssl in your environment, you would not see it due to the assumed proxy behavior.
I don't know if it always sends the request, but it did in my tests.
Yes.
If you check the certificate of the server in the browser. What do you see as issuer (Certificate Authority)? If you see something related to your corporate proxy, then you know the SSL traffic was intercepted. I'm pretty sure it is, as the Server Hello in your screenshot looks totally different than in my tests.
Yes, you are right, in the Server Hello Message, there are 2 Certificates: one is asp.statistik.at and the other one is our organisation name. The issuer of the statistik.at is our organization. ! Man you are so much helpful.. Thank you really much !! :)
there you have it! ;-)
you're welcome.
Hint: If a supplied answer resolves your question can you please "accept" it by clicking the checkmark icon next to it. This highlights good answers for the benefit of subsequent users with the same or similar questions. For extra points you can up vote the answer (thumb up).