I am not able to trouble shoot this issue at all, I have attached the screen shots of wireshark capture for both failed and successful communications. kind of running in time crunch , any help much appreciated. Thanks, GK asked 08 May '14, 04:02 gk_vandamme edited 08 May '14, 04:04 |
2 Answers:
In the first session the client (192.168.0.6) closes the connection after having received the Server Hello, Certificate, Server Hello done from the server at 192.168.0.125. So it is probably the server's certificate that the client doesn't like. In the second session the SSL handshake continues, so the client (192.168.0.141) is happy with the server's certificate. So look at the clients certificate store and see if the certificate (chain) is trusted. As Kurt mentioned the failing client is using TLS1.2 - The server responds with a TLS1.0 Server Hello in both cases. Can you change it to use TLS1.0 also? answered 08 May '14, 06:02 mrEEde edited 14 May '14, 23:31 |
In that case the client does not accept the cert due to other reasons. Three possible reasons pop up in my mind.
Regards answered 09 May '14, 12:05 Kurt Knochner ♦ edited 09 May '14, 15:17
would that make any difference ? (14 May '14, 01:50) gk_vandamme FAILED HANDSHAKE CAPTURE (14 May '14, 01:54) gk_vandamme WORKING HANDSHAKE CAPTURE (14 May '14, 01:57) gk_vandamme Two possible things:
I can't see any clear sign for a problem in the capture file, so you'll probably have to enable some form of 'debugging/logging' on the client to figure out what's going wrong. As a first step, you could try to change the client config to use a different TLS version. Regards (14 May '14, 15:10) Kurt Knochner ♦ |

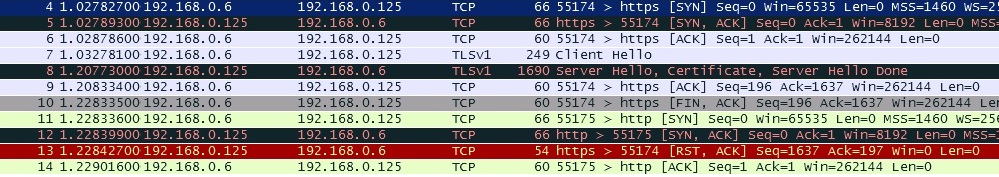
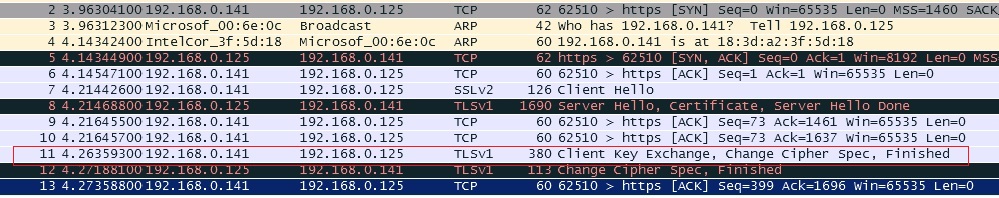 I have this issue where when a connection is happening between a client and a server (both are hosted on Hyper V) server being windows server 2008 R2 and the client being Windows 8.1 R2 communication fails (both are in the same network). However when I try the same procedure with windows 8.1 physical machine (server still being 2008 R2 on hyper V), communication successfully happens.
I have this issue where when a connection is happening between a client and a server (both are hosted on Hyper V) server being windows server 2008 R2 and the client being Windows 8.1 R2 communication fails (both are in the same network). However when I try the same procedure with windows 8.1 physical machine (server still being 2008 R2 on hyper V), communication successfully happens.
Checked that .. and the server certificate is added in all the trust stores of the client (Win 8.1) machine. still no luck.. :-(
You could export the certificate from the trace as .cer and doubleclick on it to have windows validate it ...