asked 21 Jul '14, 08:34 miky7 edited 22 Jul '14, 04:16 |
One Answer:
Well, doing packet analysis based on a 'blackened' screenshot is nearly impossible! If you want an answer that is even close to the reality, you should post a capture file somewhere (google drive, dropbox, cloudshark.org). If you have any concerns regarding privacy issues, you can anonymize the file with TraceWrangler, a tool of our member @Jasper. Now, based on the screenshot, I don't see any sign for a DDoS (distributed DoS), as there is only one IP address shown on the screenshot, which is not enough the talk about a distrubted DoS (DDoS). Regarding a DoS: The screenshot hides the time stamps and there is no information at all what the IO graph is showing. So, it's impossible to tell if this is a DoS or a port scan. However, based on my experience with DoS attacks, I'm almost sure that this is not a DoS attack, at least not an attack at the protocol level, as the IO graph would look different ;-) Regards answered 22 Jul '14, 03:48 Kurt Knochner ♦ edited 22 Jul '14, 04:35 grahamb ♦ |

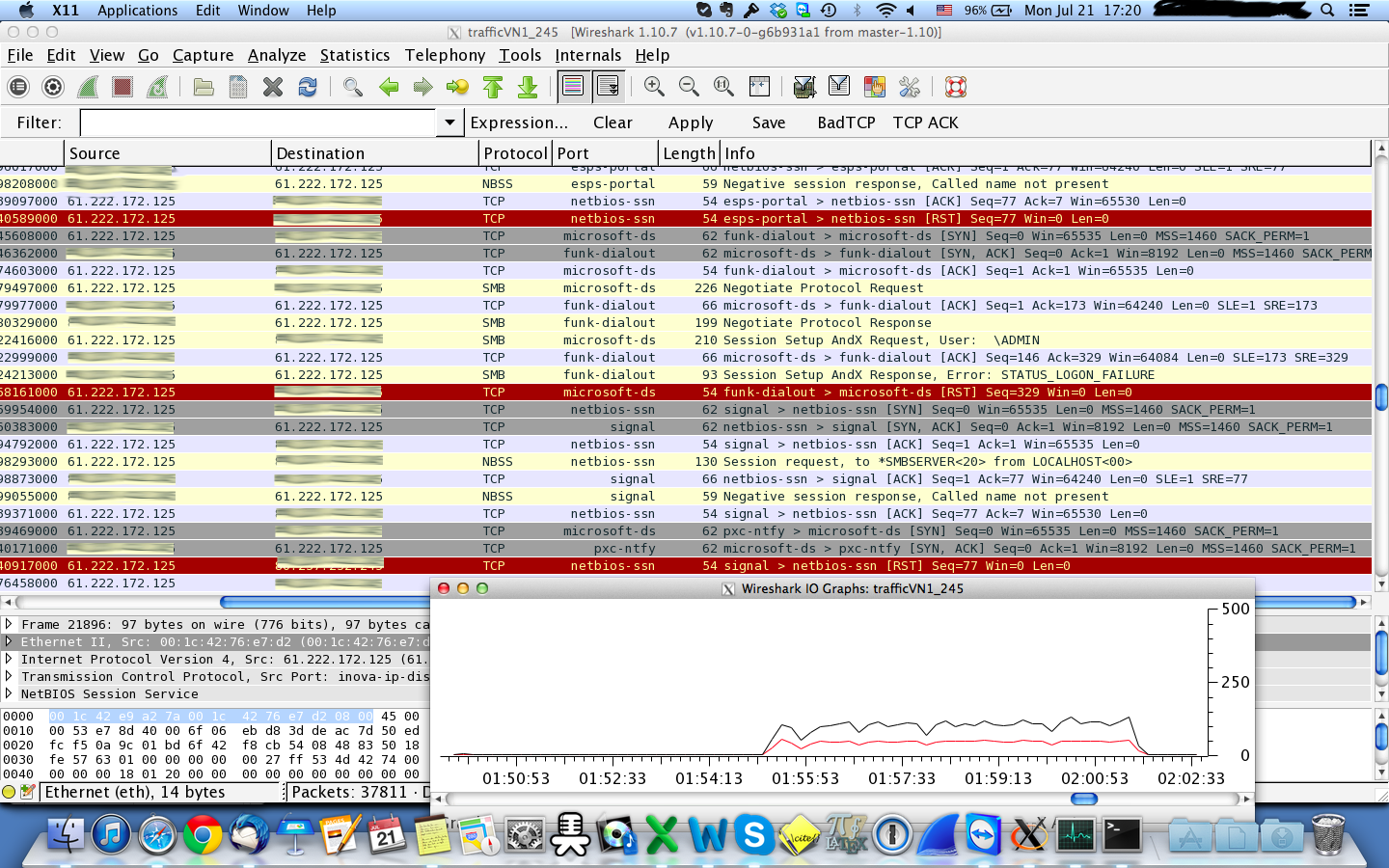 I am using wireshark to analyse traffic that I captured with tcpdump but I am not sure if what I see is a DoS attack or port scanning. The file used can be downloaded from
I am using wireshark to analyse traffic that I captured with tcpdump but I am not sure if what I see is a DoS attack or port scanning. The file used can be downloaded from
Thank you for the reply. I will edit the post to include the file
O.K., with access to the capture file (updated question), this looks much more like an attack, even a bit like an attempt to run a DDoS.
Reason:
So, actually it looks like a DDoS, even though the frequency of the packets is not very high. However: sometimes it's enough to make your DNS server fail, for whatever reason (please check the logs).
To answer you question in the title:
I used the function
and then I did some sorting in the TCP and UDP tabs. Then, with a bit of experience, you'll easily figure out if it's a port scan or an attempt to run a DDoS attack. See my explanations above.
Thank you very much for the reply! I also had the same impression but since it is the first time I saw a pcap capture, I was not sure. I also have some SYN flooding from a specific IP but the frequency is still quite low and the number of packets not that high. Perhaps an attempt to fool any IDS software?
maybe.
Or a test of a new tool. Or the preparation for the 'real' attack. Or kids playing with tools. Impossible to know ...