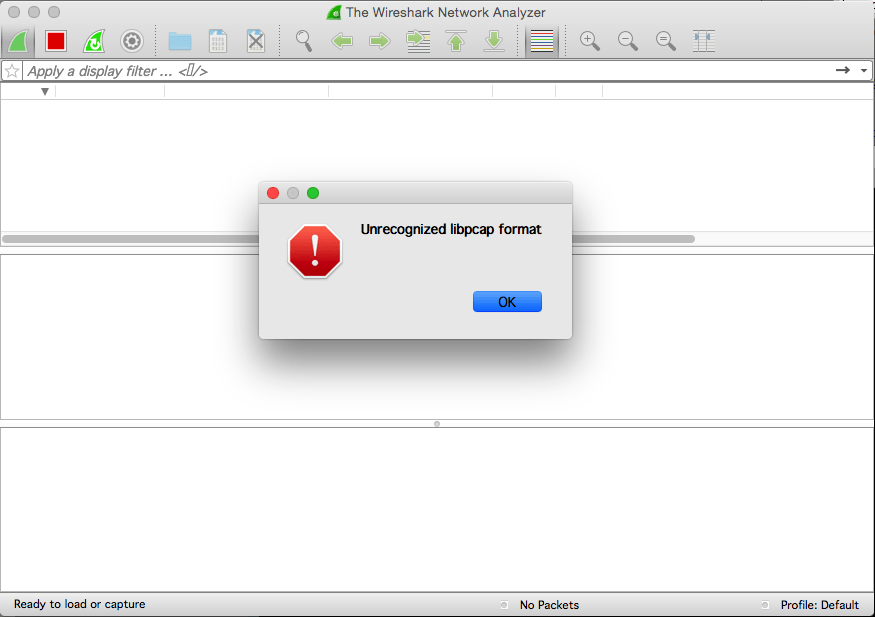
TShark 1.12.x, by default, doesn't write libpcap format with -w, it writes pcap-ng format, and dumpcap (which is what Wireshark uses to do capturing) ONLY reads libpcap format.
If you want to use TShark to capture on the server, you'd need to do tshark -F pcap -f "port not 22" -w -.
However, in your example, there is no good reason to use TShark; dumpcap would do better, and tcpdump would probably do even better:
ssh server1 'tcpdump -w - port not 22' | wireshark -k -i -
Furthermore, as your server is running FreeBSD 10, its tcpdump supports the -U flag, which causes the standard output buffers to be flushed after each packet batch, so the entire packet batch gets written to the standard output at that point rather than part of the last packet being written only when the next packet is seen, so you probably want to do
ssh server1 'tcpdump -U -w - port not 22' | wireshark -k -i -
(Note that -U should not be used if the remote machine's tcpdump is earlier than tcpdump 3.8 or if the libpcap is uses is earlier than libpcap 0.8; this means you will probably be able to use it on most machines these days.)
answered 06 Oct '14, 15:17

Guy Harris ♦♦
17.4k●3●35●196
accept rate: 19%