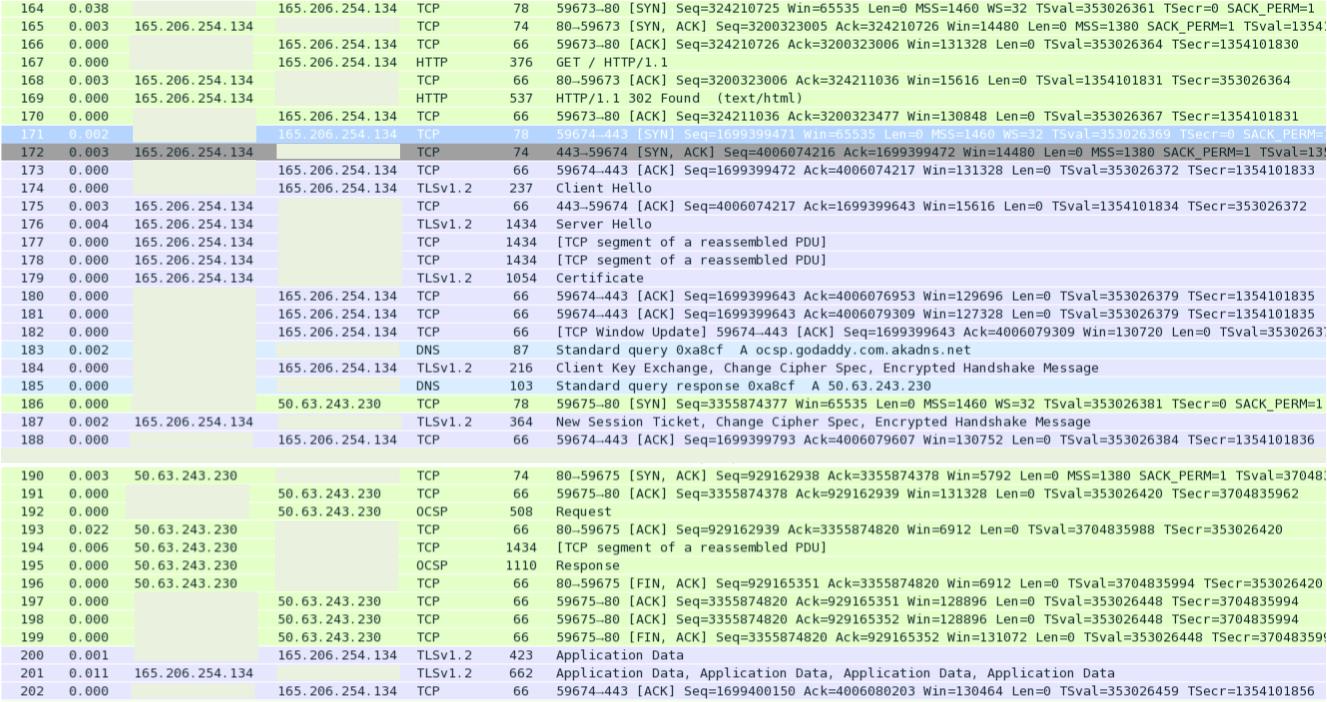
As requested:
ssl_association_remove removing TCP 443 - http handle 0x10c187820
Private key imported: KeyID dd:29:74:15:7b:e6:76:47:f5:f0:68:3e:8a:55:61:62:...
ssl_load_key: swapping p and q parameters and recomputing u
ssl_init IPv4 addr '127.0.0.1' (127.0.0.1) port '443' filename '/Users/haguerc/Downloads/snakeoil2_070531/rsasnakeoil2.key' password(only for p12 file) ''
ssl_init private key file /Users/haguerc/Downloads/snakeoil2_070531/rsasnakeoil2.key successfully loaded.
association_add TCP port 443 protocol http handle 0x10c187820
Private key imported: KeyID 8f:7d:52:a1:b2:f3:d0:83:0b:bf:d8:7f:f0:36:54:2f:...
ssl_load_key: swapping p and q parameters and recomputing u
ssl_init IPv4 addr '165.206.254.134' (165.206.254.134) port '443' filename '/Volumes/SOLERA/wildcard.rsa.pem' password(only for p12 file) ''
ssl_init private key file /Volumes/SOLERA/wildcard.rsa.pem successfully loaded.
association_add TCP port 443 protocol http handle 0x10c187820
dissect_ssl enter frame #174 (first time)
ssl_session_init: initializing ptr 0x113210790 size 712
association_find: TCP port 59674 found 0x0
packet_from_server: is from server - FALSE
conversation = 0x10ce04ab0, ssl_session = 0x113210790
record: offset = 0, reported_length_remaining = 171
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 166, ssl state 0x00
association_find: TCP port 59674 found 0x0
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 1 offset 5 length 162 bytes, remaining 171
packet_from_server: is from server - FALSE
ssl_find_private_key server 165.206.254.134:443
ssl_find_private_key: testing 2 keys
dissect_ssl3_hnd_hello_common found CLIENT RANDOM -> state 0x01
dissect_ssl enter frame #176 (first time)
packet_from_server: is from server - TRUE
conversation = 0x10ce04ab0, ssl_session = 0x113210790
record: offset = 0, reported_length_remaining = 1368
dissect_ssl3_record found version 0x0303(TLS 1.2) -> state 0x11
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 65, ssl state 0x11
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 2 offset 5 length 61 bytes, remaining 70
dissect_ssl3_hnd_hello_common found SERVER RANDOM -> state 0x13
ssl_restore_session Cannot restore using an empty SessionID
trying to use SSL keylog in
failed to open SSL keylog
cannot find master secret in keylog file either
dissect_ssl3_hnd_srv_hello found CIPHER 0xC014 -> state 0x17
dissect_ssl3_hnd_srv_hello trying to generate keys
ssl_generate_keyring_material not enough data to generate key (0x17 required 0x37 or 0x57)
dissect_ssl3_hnd_srv_hello can't generate keyring material
record: offset = 70, reported_length_remaining = 1298
need_desegmentation: offset = 70, reported_length_remaining = 1298
dissect_ssl enter frame #179 (first time)
packet_from_server: is from server - TRUE
conversation = 0x10ce04ab0, ssl_session = 0x113210790
record: offset = 0, reported_length_remaining = 4675
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 4670, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 11 offset 5 length 4666 bytes, remaining 4675
dissect_ssl enter frame #179 (first time)
packet_from_server: is from server - TRUE
conversation = 0x10ce04ab0, ssl_session = 0x113210790
record: offset = 0, reported_length_remaining = 347
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 333, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 12 offset 5 length 329 bytes, remaining 338
record: offset = 338, reported_length_remaining = 9
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 4, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 14 offset 343 length 0 bytes, remaining 347
dissect_ssl enter frame #184 (first time)
packet_from_server: is from server - FALSE
conversation = 0x10ce04ab0, ssl_session = 0x113210790
record: offset = 0, reported_length_remaining = 150
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 70, ssl state 0x17
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 16 offset 5 length 66 bytes, remaining 75
ssl_generate_pre_master_secret: found SSL_HND_CLIENT_KEY_EXCHG, state 17
ssl_decrypt_pre_master_secret session uses DH (17) key exchange, which is impossible to decrypt
ssl_generate_pre_master_secret: can't decrypt pre master secret
trying to use SSL keylog in
failed to open SSL keylog
dissect_ssl3_handshake can't generate pre master secret
record: offset = 75, reported_length_remaining = 75
dissect_ssl3_record: content_type 20 Change Cipher Spec
dissect_ssl3_change_cipher_spec
packet_from_server: is from server - FALSE
ssl_change_cipher CLIENT
record: offset = 81, reported_length_remaining = 69
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 64, ssl state 0x17
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 6 offset 86 length 4641658 bytes, remaining 150
dissect_ssl enter frame #187 (first time)
packet_from_server: is from server - TRUE
conversation = 0x10ce04ab0, ssl_session = 0x113210790
record: offset = 0, reported_length_remaining = 298
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 218, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 4 offset 5 length 214 bytes, remaining 223
ssl_save_session_ticket stored session_ticket[208]:
| 5e a8 e9 32 60 3d 43 7d f9 73 d7 d7 7d 4d 0f c2 |^..2`=C}.s..}M..|
| 32 f4 2c 27 b6 04 fa 5c e1 ae f8 61 e1 d0 2f 0a |2.,'...\...a../.|
| 73 cf ac 37 30 16 e2 db 73 c5 22 9f 4c b2 fd cb |s..70...s.".L...|
| 61 04 4e ac 61 4a 1b 1f 4d 68 ac cf e3 60 0d 03 |a.N.aJ..Mh...`..|
| f2 17 f0 c8 49 60 39 3d df c4 b7 e0 a3 c3 fb a8 |....I`9=........|
| cc e0 f3 54 50 4d e1 c4 5a 72 f8 d6 03 80 d2 03 |...TPM..Zr......|
| d1 c0 d3 82 97 46 69 0d 7c db 5f 5e 9d 55 00 7e |.....Fi.|._^.U.~|
| c7 a0 ab d0 b4 c3 64 a2 86 8e e2 19 81 aa 26 af |......d.......&.|
| 0e b4 2b 69 39 59 bf 52 0e f0 69 25 7f c6 f8 64 |..+i9Y.R..i%...d|
| 1b 58 6d 23 2c 63 d2 8b 4f 6b a2 33 50 dc 6b cb |.Xm#,c..Ok.3P.k.|
| 2f 6c 62 46 4a 43 5a ad 6d 88 e0 fe 85 71 32 5d |/lbFJCZ.m....q2]|
| 60 a8 61 d9 2e b8 a3 a7 9b 72 66 b4 80 85 ec c4 |`.a......rf.....|
| 8f 2f 91 43 8c 16 2c 15 86 df 10 d2 0c 5f 61 cb |./.C..,......_a.|
ssl_save_session_ticket stored master secret[48]:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
record: offset = 223, reported_length_remaining = 75
dissect_ssl3_record: content_type 20 Change Cipher Spec
dissect_ssl3_change_cipher_spec
packet_from_server: is from server - TRUE
ssl_change_cipher SERVER
record: offset = 229, reported_length_remaining = 69
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 64, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 227 offset 234 length 973435 bytes, remaining 298
dissect_ssl enter frame #200 (first time)
packet_from_server: is from server - FALSE
conversation = 0x10ce04ab0, ssl_session = 0x113210790
record: offset = 0, reported_length_remaining = 357
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 352, ssl state 0x17
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 59674 found 0x0
association_find: TCP port 443 found 0x110d43980
dissect_ssl enter frame #201 (first time)
packet_from_server: is from server - TRUE
conversation = 0x10ce04ab0, ssl_session = 0x113210790
record: offset = 0, reported_length_remaining = 596
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 368, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0x110d43980
record: offset = 373, reported_length_remaining = 223
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 48, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0x110d43980
record: offset = 426, reported_length_remaining = 170
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 112, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0x110d43980
record: offset = 543, reported_length_remaining = 53
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 48, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0x110d43980</code></pre></div><div class="answer-controls post-controls"></div><div class="post-update-info-container"><div class="post-update-info post-update-info-user"><p>answered <strong>07 Nov '14, 10:38</strong></p><img src="https://secure.gravatar.com/avatar/e9731598241220667226ea8b75584a70?s=32&d=identicon&r=g" class="gravatar" width="32" height="32" alt="dribniff's gravatar image" /><p><span>dribniff</span><br />
6●4●4●5
accept rate: 0%


Post the SSL debug out put as text straight in your question. Use the "code" button to format it for easier viewing.
It's possible that the TLS session is using a DH key exchange which makes it more difficult to decrypt, see this question from StackExchange. In Firefox, click on the padlock | More Information ... and then in the "Technical Details" section what is the reported connection info.
Have you also read through the Wireshark Wiki page on SSL, it's here?