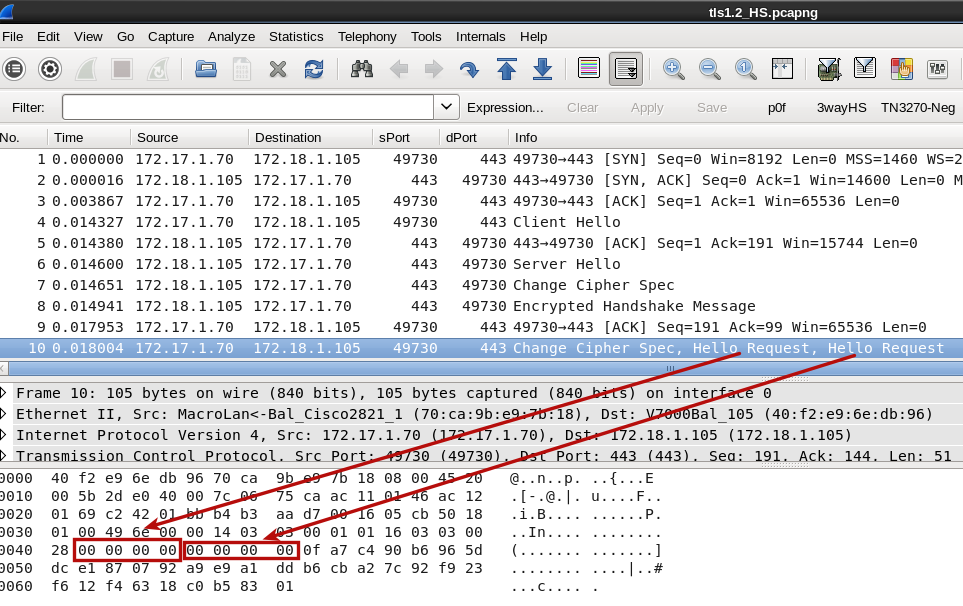
Hello, can somebody have a look and confirm that wireshark is right in interpreting 4 zeroes as Hello Requests. Anyone knows what that is? asked 04 Apr '15, 10:12 mrEEde edited 04 Apr '15, 22:48 |
One Answer:
Your capture is using an AEAD cipher suite. These have an explicit nonce in their TLSCipherText fragment data: This explicit nonce for AES-GCM cipher suites may be a 64-bit counter which is also the case in your capture. The heuristics of Wireshark works as follows: if the record fragment for a Handshake message can be "decoded" (because the initial byte is a valid handshake message type), it will be dissected. So what you are seeing is a bug that occurs when the records cannot be decrypted, and only occurs when using the AES-GCM AEAD cipher suites. answered 04 Apr '15, 10:45 Lekensteyn |

 Trace is available on Cloudshark
Trace is available on Cloudshark
Thanks for the explanation.