Hi everyone, i am tracing some packets in wireshark and i have this problem that i found a packet that is an ack packet as the LEN = 0 and the only flag set is ack flag = 1, now usually while tracing i open an ack packet and in the TCP i select [Seq/Ack analysis] which tells me which packet this ack is for , now i did not find this [seq/ack analysis] and so i don't know what packet it is acknowledging even i tried to find the packet manually by calculating (seq no. + len) but i did not find it ...any help ? asked 03 Jun '15, 04:12 yas1234 edited 03 Jun '15, 04:21 grahamb ♦ |
One Answer:
Your approach doesn't work when TCP Segmentation Offload is enabled. At a trace at the sender you see (too) large segments are leaving the host and acknowledgements are arriving that acknowledge bytes in the middle of the sent segment. answered 03 Jun '15, 22:05 mrEEde so if the packet is not divided into segments i will not get this type of ack right?so how do i disable segmentation? (25 Jun '15, 06:45) yas1234 Depends on your operating system... http://lmgtfy.com/?q=disable+tcp+segmentation+offload (25 Jun '15, 07:04) mrEEde PERFECT THANK U! (25 Jun '15, 08:06) yas1234 If this answers your question can you please 'accept' the answer by clicking the checkmark. Thanks Matthias (25 Jun '15, 10:40) mrEEde i have a small more question, now if i disable the tso ..is it a Must to disable the TX also or not? ..and what is best ? i googled that but seems like always when the tso is off the tx is off also and i do not really get what tx do . (25 Jun '15, 11:12) yas1234 I don't know what TX means in this context but TSO has its purpose - to save CPU cycles on the Operating Systems - and many manufacturers have taken a lot of effort to make it work. The drawback is that trace analysis is a little more tricky. So if your main goal is to diagnose traffic then you may/must disable it. If your purpose is to run on an efficient TCPIP stack you leave it enabled... ;-) (25 Jun '15, 14:50) mrEEde actually i need to disable it but the problem now when i disabled it still my captures at the sender are not the same at the receiver, the sender is sending chunks of data and the receiver collects them into one packet then acknowledges it ,,i don't want that i want them both to match ...any help ? i attached the 2 captures https://www.dropbox.com/s/fu8zonho9wiqp9t/caps.zip?dl=0 (26 Jun '15, 02:39) yas1234 It looks like that you should try this command if you use Win2012 R2 or Win 8 netsh int tcp set global rsc=disabled Other wise you can provide the out put of the cmd: netsh int tcp show global (26 Jun '15, 03:42) Christian_R USING linux (26 Jun '15, 04:29) yas1234 ethtool -K ethY lro off. (26 Jun '15, 05:03) Christian_R showing 5 of 10 show 5 more comments |

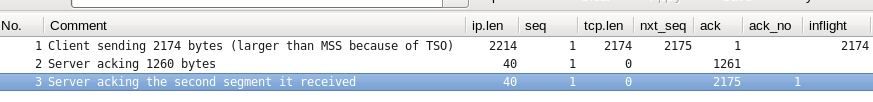
well, it's near to impossible to do "virtual" packet troubleshooting based on some problem descriptions ;-)
Can you please upload a small capture file somewhere (google drive, dropbox, cloudshark.org) and post the link here?