Hi everyone.
I'm decrypting MMS traffic with TLS between a client and a server, giving Wireshark the server private key, and everthing works fine, I can see the plain MMS messages.
In some cases the TLS handshake has some trouble with TCP retransmissions, reassembled PDU etc. In these cases can happen that wireshark is able only to decrypt half of the communication, the traffic from server to client.
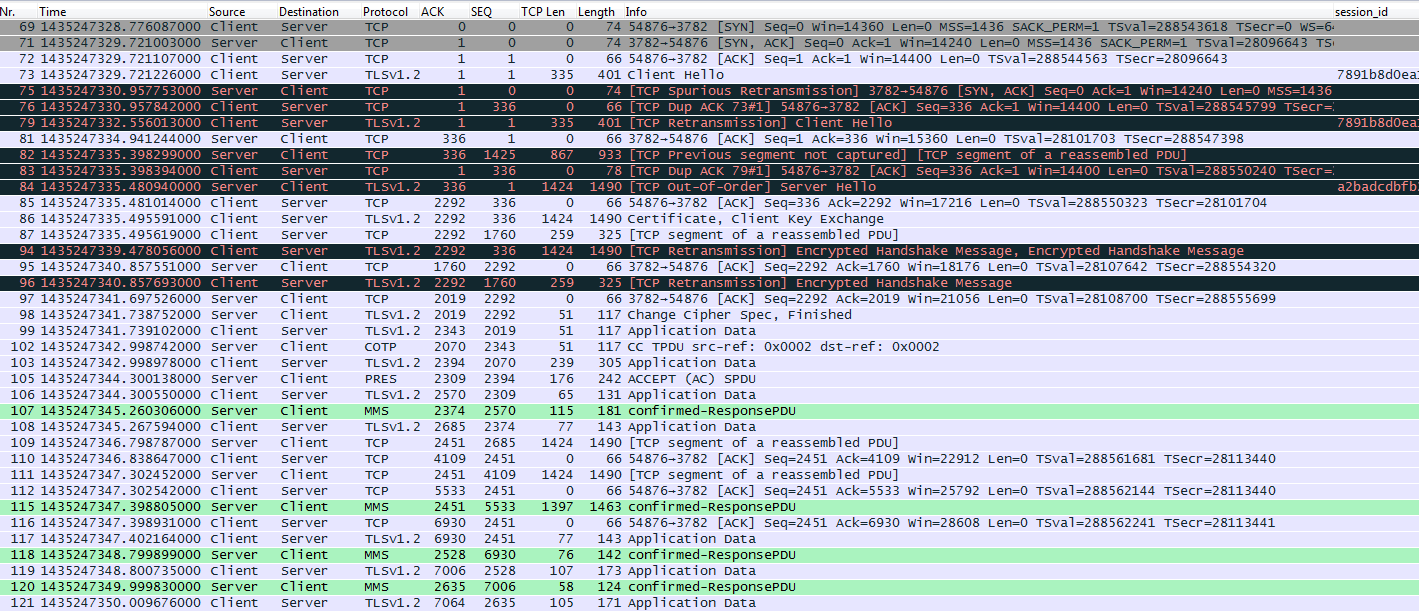
As you can see in the image the MMS traffic from the client is decrypted "Application Data".
My questions are: Does exist some wireshark setting to resolve this problem? If wireshark can calculate the master key (server side) and use it to decrypt the server traffic, shouldn't be able to decrypt also the client one with the same key?
UPDATE 1
I don't know, but maybe it's useful to show more info about frame 82 and 87:
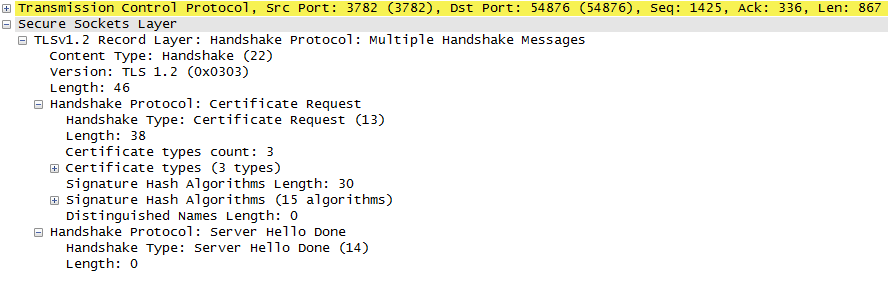
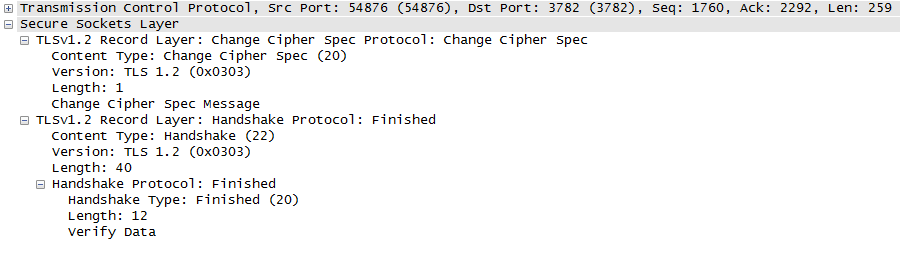
Frame 87 is the TLS Finished message from Client to Server, and it's decrypted, but the next TLS messages from Client to Server, in frame 94, are encrypted!
UPDATE 2
Maybe the problem in in the trace capture phase: for info, I get the pcap traces using default parameters with Wireshark 1.12.3 on Windows 7 (Client Side) and with tcpdump on Centos 6 (server side). Both capture sides show the same problem I'm trying to solve.
UPDATE 3
I provide another tarce with the same issue + the ssl debug log. I want to point out that the Change Cipher Spec message from the client is received but not present in the ssl debug log (frame 57)
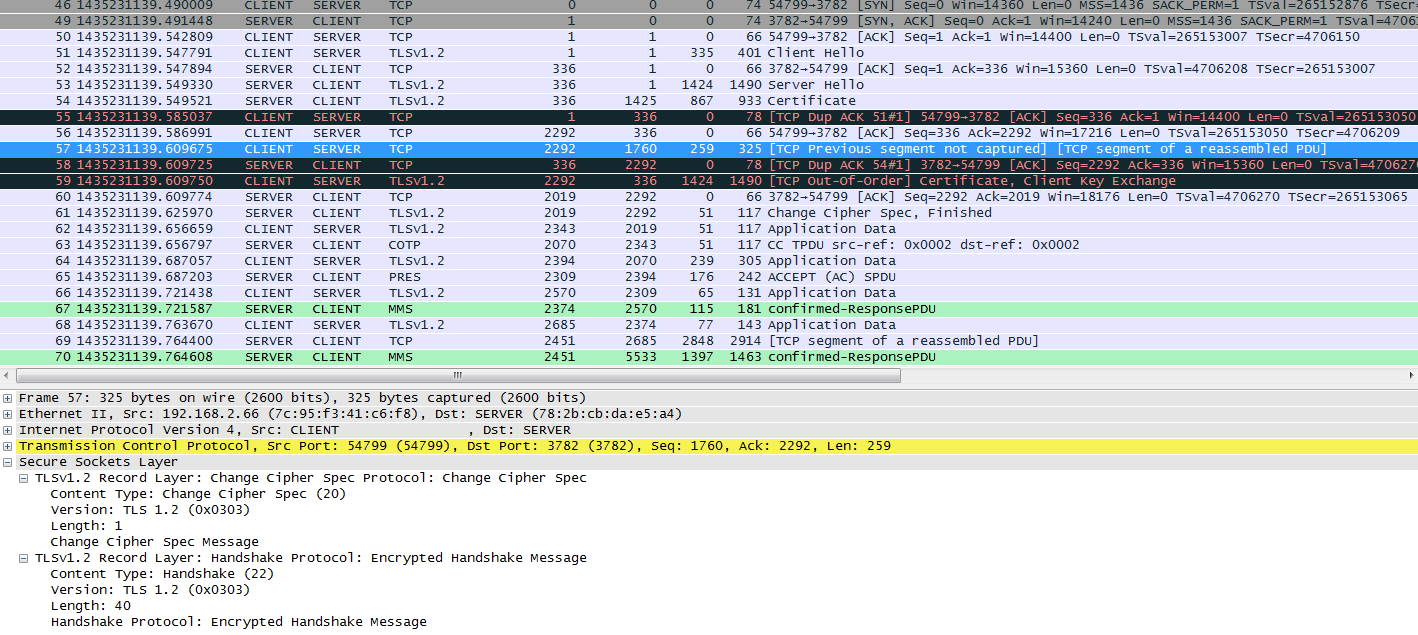
dissect_ssl enter frame #51 (first time)
ssl_session_init: initializing ptr 0000000008A50780 size 712
association_find: TCP port 54799 found 0000000000000000
packet_from_server: is from server - FALSE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 335
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 330, ssl state 0x00
association_find: TCP port 54799 found 0000000000000000
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 1 offset 5 length 326 bytes, remaining 335
packet_from_server: is from server - FALSE
ssl_find_private_key server IPSERVER:3782
ssl_find_private_key: testing 4 keys
dissect_ssl3_hnd_hello_common found CLIENT RANDOM -> state 0x01
dissect_ssl enter frame #53 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 1424
dissect_ssl3_record found version 0x0303(TLS 1.2) -> state 0x11
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 86, ssl state 0x11
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 2 offset 5 length 82 bytes, remaining 91
dissect_ssl3_hnd_hello_common found SERVER RANDOM -> state 0x13
dissect_ssl3_hnd_srv_hello found CIPHER 0x009D -> state 0x17
dissect_ssl3_hnd_srv_hello trying to generate keys
ssl_generate_keyring_material not enough data to generate key (0x17 required 0x37 or 0x57)
dissect_ssl3_hnd_srv_hello can't generate keyring material
record: offset = 91, reported_length_remaining = 1333
need_desegmentation: offset = 91, reported_length_remaining = 1333
dissect_ssl enter frame #54 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 2149
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 2144, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 11 offset 5 length 2140 bytes, remaining 2149
dissect_ssl enter frame #54 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 51
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 46, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 13 offset 5 length 38 bytes, remaining 51
dissect_ssl3_handshake iteration 0 type 14 offset 47 length 0 bytes, remaining 51
dissect_ssl enter frame #57 (first time)
packet_from_server: is from server - FALSE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 259
dissect_ssl enter frame #59 (first time)
packet_from_server: is from server - FALSE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 1424
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 1091, ssl state 0x17
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 11 offset 5 length 1087 bytes, remaining 1096
record: offset = 1096, reported_length_remaining = 328
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 262, ssl state 0x17
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 16 offset 1101 length 258 bytes, remaining 1363
ssl_generate_pre_master_secret: found SSL_HND_CLIENT_KEY_EXCHG, state 17
pre master encrypted[256]:
…
ssl_decrypt_pre_master_secret:RSA_private_decrypt
decrypted_unstrip_pre_master[255]:
…
pcry_private_decrypt: stripping 207 bytes, decr_len 255
pre master secret[48]:
…
ssl_generate_keyring_material:PRF(pre_master_secret)
pre master secret[48]:
…
client random[32]:
…
server random[32]:
…
tls12_prf: tls_hash(hash_alg SHA384 secret_len 48 seed_len 77 )
tls_hash: hash secret[48]:
…
tls_hash: hash seed[77]:
…
hash out[48]:
…
PRF out[48]:
…
master secret[48]:
…
ssl_generate_keyring_material sess key generation
tls12_prf: tls_hash(hash_alg SHA384 secret_len 48 seed_len 77 )
tls_hash: hash secret[48]:
…
tls_hash: hash seed[77]:
…
hash out[168]:
…
PRF out[168]:
…
key expansion[168]:
…
Client Write key[32]:
…
Server Write key[32]:
…
Client Write IV[4]:
…
Server Write IV[4]:
…
ssl_generate_keyring_material ssl_create_decoder(client)
ssl_create_decoder CIPHER: AES256
decoder initialized (digest len 48)
ssl_generate_keyring_material ssl_create_decoder(server)
ssl_create_decoder CIPHER: AES256
decoder initialized (digest len 48)
ssl_generate_keyring_material: client seq 0, server seq 0
ssl_save_session stored session id[32]:
…
ssl_save_session stored master secret[48]:
…
dissect_ssl3_handshake session keys successfully generated
record: offset = 1363, reported_length_remaining = 61
need_desegmentation: offset = 1363, reported_length_remaining = 61
dissect_ssl enter frame #61 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 51
dissect_ssl3_record: content_type 20 Change Cipher Spec
dissect_ssl3_change_cipher_spec
packet_from_server: is from server - TRUE
ssl_change_cipher SERVER
record: offset = 6, reported_length_remaining = 45
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 40, ssl state 0x3F
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
ssl_decrypt_record ciphertext len 40
Ciphertext[40]:
…
Plaintext[32]:
…
dissect_ssl3_handshake iteration 1 type 20 offset 0 length 12 bytes, remaining 16
dissect_ssl enter frame #62 (first time)
packet_from_server: is from server - FALSE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 51
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 46, ssl state 0x3F
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 54799 found 0000000000000000
association_find: TCP port 3782 found 0000000004FCE830
dissect_ssl enter frame #63 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 51
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 46, ssl state 0x3F
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
ssl_decrypt_record ciphertext len 46
Ciphertext[46]:
…
Plaintext[38]:
…
ssl_add_data_info: new data inserted data_len = 22, seq = 0, nxtseq = 22
association_find: TCP port 3782 found 0000000004FCE830
dissect_ssl3_record decrypted len 22
decrypted app data fragment[22]:
…
dissect_ssl3_record found association 0000000004FCE830
dissect_ssl enter frame #64 (first time)
packet_from_server: is from server - FALSE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 239
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 234, ssl state 0x3F
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 54799 found 0000000000000000
association_find: TCP port 3782 found 0000000004FCE830
dissect_ssl enter frame #65 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 176
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 171, ssl state 0x3F
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
ssl_decrypt_record ciphertext len 171
Ciphertext[171]:
…
ssl_decrypt_record: allocating 203 bytes for decrypt data (old len 72)
Plaintext[163]:
…
ssl_add_data_info: new data inserted data_len = 147, seq = 22, nxtseq = 169
association_find: TCP port 3782 found 0000000004FCE830
dissect_ssl3_record decrypted len 147
decrypted app data fragment[147]:
…
dissect_ssl3_record found association 0000000004FCE830
dissect_ssl enter frame #66 (first time)
packet_from_server: is from server - FALSE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 65
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 60, ssl state 0x3F
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 54799 found 0000000000000000
association_find: TCP port 3782 found 0000000004FCE830
dissect_ssl enter frame #67 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005A815F8, ssl_session = 0000000008A50780
record: offset = 0, reported_length_remaining = 115
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 110, ssl state 0x3F
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
ssl_decrypt_record ciphertext len 110
Ciphertext[110]:
…
Plaintext[102]:
…
ssl_add_data_info: new data inserted data_len = 86, seq = 169, nxtseq = 255
association_find: TCP port 3782 found 0000000004FCE830
dissect_ssl3_record decrypted len 86
decrypted app data fragment[86]:
…
dissect_ssl3_record found association 0000000004FCE830
Thanks
asked 02 Jul ‘15, 07:02

theo66
91●3●5●12
accept rate: 50%





Do you have the TCP Protocol preference setting “Do not call subdissectors for error packets” checked?
No I don’t. By checking that setting all the trace remains encrypted.
Out-of-order packets confused the SSL dissectors in the past, perhaps that is the case here. Could you generate a SSL debug log? You can enable this via Preferences -> Protocols -> SSL.
I get the debug log from another trace with the same issue. I show yout these 2 packet as example: the first from the client, the second from the server.
dissect_ssl enter frame #66 (first time) packet_from_server: is from server - FALSE conversation = 0000000005A815F8, ssl_session = 0000000008A50780 record: offset = 0, reported_length_remaining = 65 dissect_ssl3_record: content_type 23 Application Data decrypt_ssl3_record: app_data len 60, ssl state 0x3F packet_from_server: is from server - FALSE decrypt_ssl3_record: using client decoder decrypt_ssl3_record: no decoder available association_find: TCP port 54799 found 0000000000000000 association_find: TCP port 3782 found 0000000004FCE830dissect_ssl enter frame #67 (first time) packet_from_server: is from server - TRUE conversation = 0000000005A815F8, ssl_session = 0000000008A50780 record: offset = 0, reported_length_remaining = 115 dissect_ssl3_record: content_type 23 Application Data decrypt_ssl3_record: app_data len 110, ssl state 0x3F packet_from_server: is from server - TRUE decrypt_ssl3_record: using server decoder ssl_decrypt_record ciphertext len 110 Ciphertext[110]: … Plaintext[102]: … ssl_add_data_info: new data inserted data_len = 86, seq = 169, nxtseq = 255 association_find: TCP port 3782 found 0000000004FCE830 dissect_ssl3_record decrypted len 86 decrypted app data fragment[86]: … dissect_ssl3_record found association 0000000004FCE830It seems that the client encoder is missing. As soon as possible I find a way to attach all the debug log.
@theo66 Can you show more of the log? Specifically, I am looking for the part where the SSL state changes to 0x3F. Are unusual messages following that transition? Are the
tcp.streamfields (“Stream number” under the TCP layer) the same for both streams? They should be the same, if not, then it could explain your issue.@Lekensteyn I checked, tcp.stream is the same for both streams. I’ve updated the question with the ssl log.