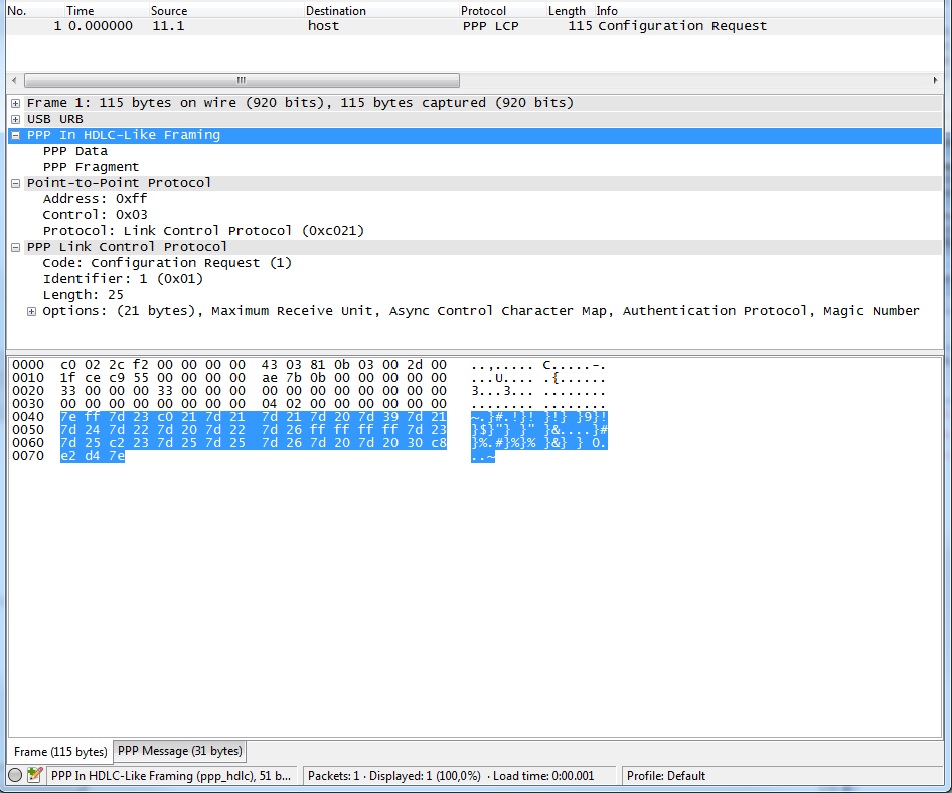
If I capture "PPP In HDLC-Like Framing" packets over USB interface wireshark decodes correctly the packets (Flag Sequence 0x7E is recognized and escaped chars are handled 0x7D plus xor 0x20).
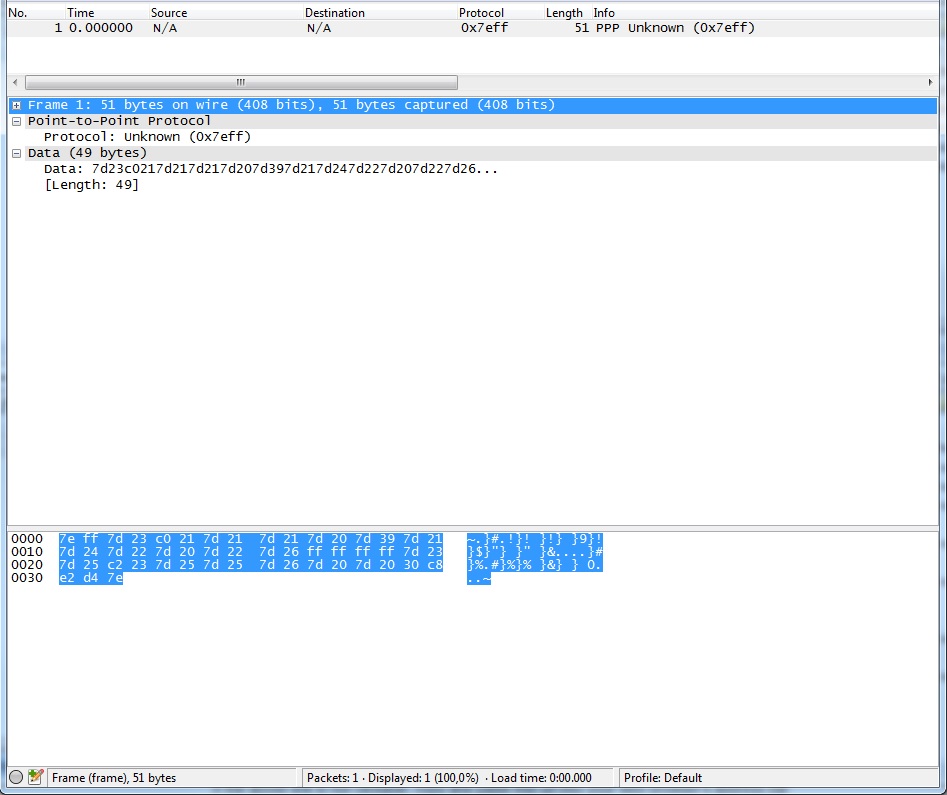
Instead if I try to convert an hexdump log of raw PPP packets into a pcap file with text2pcap (specifying as LINK_TYPE = 9 http://www.tcpdump.org/linktypes.html) they are not correctly recognized by Wireshark (Flag Sequence 0x7E and escaped chars are not handled).
I tried changing "LINK_TYPE" with each of the types which reports "HDLC" with no success. Is it a limit of text2pcap or wireshark? In my opinion if the decoder finds the "LINK_TYPE" explicitly declared inside the pcap header it is not able to discard the Flag Sequence (0x7E) and de-escape the other chars instead when the packet is encapsulated inside the URB (where the "LINK_TYPE" is not specified for the URB PDU) it is decoded correctly. Can I conclude there is no way to use text2pcap for my needs? Thank you in advance. asked 17 Aug '15, 08:37 mmaz edited 17 Aug '15, 08:45 |
2 Answers:
The best that I could come up with as a possible workable solution would be to prepend the following 4 bytes to your data: ... and then assuming this data is saved in a file called, "ask45158.txt", run The extra 4 bytes are a dummy GRE header, and the Here's the sample tshark output of running
answered 17 Aug '15, 13:13 cmaynard ♦♦ |
Well, you'll have to adhere to the specified format for using a LINK_TYPE. In this case LINKTYPE_PPP is defined as: "PPP, as per RFC 1661 and RFC 1662; if the first 2 bytes are 0xff and 0x03, it's PPP in HDLC-like framing, with the PPP header following those two bytes, otherwise it's PPP without framing, and the packet begins with the PPP header.". So that means that the flag octet has no place in this format. The USB bulk data heuristics were created ad-hoc, to try to accomodate as much as possible the sample captures found 'in the wild', for which the format is 'unspecified'. So that's why the PPP over USB Bulk is being dissected, while LINKTYPE_PPP capture is considered malformed. answered 17 Aug '15, 12:06 Jaap ♦ Thank you for the reply. I tried: 1) removing the flag 0x7E at the beginning and at the end of the hexdump -> text2pcap creates a file where the packet is not correctly recognized because of the first 0x7D 2) removing also che first 0x7D and now the packet starts with 0xFF 0x03 -> text2pcap creates a packet which is recognized as "malformed" 3) removing all the 0x7D and xor-ing with 0x20 all the escaped bytes -> now text2pcap produces a valid pcap file comparable with the URB encapsulated. I can conclude LINKTYPE_PPP dissector doesn't fully adhere to RFC 1662 where the escaping with 0x7D is described. (17 Aug '15, 15:03) mmaz 1
You can also conclude that the description of LINKTYPE_PPP on [the tcpdump.org link-layer header types page(http://www.tcpdump.org/linktypes.html) needs to clarify that it is NOT for raw octet streams. It's for frames that have been un-stuffed and that have the Address, Control, Protocol, and Information fields from section 3.1 "Frame Format" of RFC 1662. I will update it. There is no LINKTYPE_ value for either octet-stuffed or bit-stuffed PPP-in-HDLC-like-framing packets, unfortunately, so, no, text2pcap can't do it directly - Chris Maynard's solution is the best that can be done. (17 Aug '15, 15:42) Guy Harris ♦♦ |

Thank you for your suggestion, I will follow it.
Do you have any env var which enables field expansion of tshark? Because using your command line I get a compact output:
It doesn't expand the PPP Link Control Protocol? His command line was intended to give compact output for everything above LCP - that's what
-O lcpdoes. If you want everything expanded, use-Vrather than-O lcp.It's working fine! I copied and pasted also the final ":" :-)
@mmaz
If an answer has solved your issue, please accept the answer for the benefit of other users by clicking the checkmark icon next to the answer. Please read the FAQ for more information.