Hi everyone,
I'm trying to do something that appears simple enough for HTTP, but seems impossible for SSL/TLS. I would very much appreciate your take on this.
What am I trying to do?
- I'm trying to read the ssl fields provided by the ssl dissector so I can add additional information based on cross-sslrecord content.
- An example: showing on the frame containing a 'ClientHello' message, that renegotiation is not only supported but has also been requested by the server or client (i.e. like there is a HelloRequest message further down the line)
- I need to post-parse the ssl. fields, but they do not fill by default upon pcap load. I need to click a frame containing an SSL record, then I get access, in code, to the ssl. fields of that frame.
- I want the code to run on pcap load, but after the ssl dissector has been run completely. So I thought: post-dissector... but no; then I thought: replacing the ssl dissector with my own and my own dissector calls the original ssl dissector first. This is even a textbook example for 'chained dissector' from the wiki (https://wiki.wireshark.org/Lua/Dissectors)
The problem?
- Chaining does not seem to work with the SSL dissector.
- my code works perfectly if I choose another port than 443.
- 444 works (a port for which the TCP dissector table has no entry yet)
- 80 works (a port for which the TCP dissector table has an existing entry, namely 'HTTP')
- 443 does not work (the dissector table keeps showing me 'SSL' instead of my 'SSLTS'; on the other ports it does replace the original with mine)
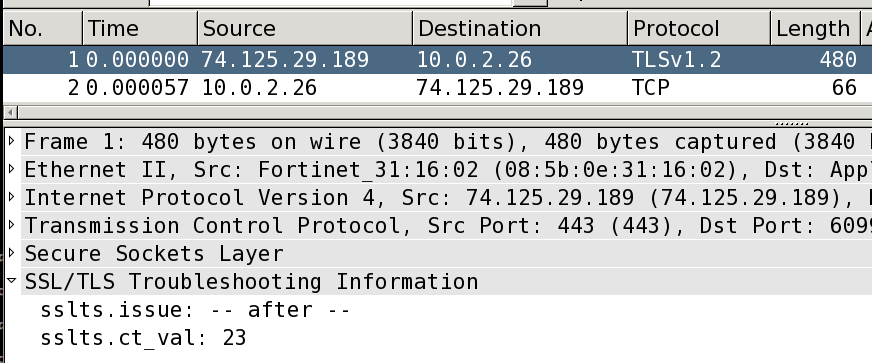
Here's the code I use: (change 443 to 80 => it works, you get extra fields, etc, if you use 443, you need to select 'Decode As...' on a stream)
do
local sslts = Proto("sslts","SSL/TLS Troubleshooting Information");
local sslts_issue = ProtoField.string("sslts.issue")
sslts.fields = {sslts_issue}
local original_ssl_dissector
function sslts.dissector(tvb,pinfo,tree)
original_ssl_dissector:call(tvb,pinfo,tree)
local subtree = tree:add(sslts,tvb)
subtree:add(sslts_issue,tvb(),"—")
end
local tcp_dissector_table = DissectorTable.get("tcp.port")
original_ssl_dissector = tcp_dissector_table:get_dissector(443)
tcp_dissector_table:add(443, sslts)
local function heur_dissect_sslts(tvbuf,pktinfo,root)
sslts.dissector(tvbuf,pktinfo,root)
pktinfo.conversation = sslts
return true
end
sslts:register_heuristic("tcp",heur_dissect_sslts)
end
My questions?
- Can it be done with the SSL dissector and LUA, or am I stuck doing it in C?
- If it can be done and someone did it, can you show/explain me how?
- Next to chained dissectors and post-dissectors, would there be any other way that I am missing at the moment?
Kind regards and many thanks in advance for when I get a response on this one :D
Thomas Schockaert
asked 01 Sep ‘15, 17:41

sstm
6●1●1●2
accept rate: 0%

And lest I forget, my version is this: Version 1.12.7 (v1.12.7-0-g7fc8978 from master-1.12)