ssl_association_remove removing TCP 443 - http handle 0000000004453240
Private key imported: KeyID 75:a5:a6:2c:01:a5:7c:34:a5:4a:a0:e9:c3:74:4f:18:...
ssl_load_key: swapping p and q parameters and recomputing u
ssl_init IPv4 addr '192.168.0.9' (192.168.0.9) port '443' filename 'C:\Users\chris_000\Desktop\key.pem' password(only for p12 file) ''
ssl_init private key file C:\Users\chris_000\Desktop\key.pem successfully loaded.
association_add TCP port 443 protocol http handle 0000000004453240
dissect_ssl enter frame #8 (first time)
ssl_session_init: initializing ptr 000000000A5D1790 size 712
association_find: TCP port 60866 found 0000000000000000
packet_from_server: is from server - FALSE
conversation = 0000000005771098, ssl_session = 000000000A5D1790
record: offset = 0, reported_length_remaining = 223
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 218, ssl state 0x00
association_find: TCP port 60866 found 0000000000000000
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 1 offset 5 length 214 bytes, remaining 223
packet_from_server: is from server - FALSE
ssl_find_private_key server 192.168.0.9:443
ssl_find_private_key: testing 1 keys
dissect_ssl3_hnd_hello_common found CLIENT RANDOM -> state 0x01
dissect_ssl enter frame #13 (first time)
ssl_session_init: initializing ptr 000000000A5D2280 size 712
association_find: TCP port 60867 found 0000000000000000
packet_from_server: is from server - FALSE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 175
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 170, ssl state 0x00
association_find: TCP port 60867 found 0000000000000000
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 1 offset 5 length 166 bytes, remaining 175
packet_from_server: is from server - FALSE
ssl_find_private_key server 192.168.0.9:443
ssl_find_private_key: testing 1 keys
dissect_ssl3_hnd_hello_common found CLIENT RANDOM -> state 0x01
dissect_ssl enter frame #14 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 965
dissect_ssl3_record found version 0x0301(TLS 1.0) -> state 0x11
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 960, ssl state 0x11
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 2 offset 5 length 77 bytes, remaining 965
dissect_ssl3_hnd_hello_common found SERVER RANDOM -> state 0x13
dissect_ssl3_hnd_srv_hello found CIPHER 0x0005 -> state 0x17
dissect_ssl3_hnd_srv_hello trying to generate keys
ssl_generate_keyring_material not enough data to generate key (0x17 required 0x37 or 0x57)
dissect_ssl3_hnd_srv_hello can't generate keyring material
dissect_ssl3_handshake iteration 0 type 11 offset 86 length 871 bytes, remaining 965
dissect_ssl3_handshake iteration 0 type 14 offset 961 length 0 bytes, remaining 965
dissect_ssl enter frame #16 (first time)
packet_from_server: is from server - FALSE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 314
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 262, ssl state 0x17
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 16 offset 5 length 258 bytes, remaining 267
ssl_generate_pre_master_secret: found SSL_HND_CLIENT_KEY_EXCHG, state 17
pre master encrypted[256]:
| 07 6a 72 cb 03 09 9c 0e 23 c6 23 7f 2c 3d 85 6b |.jr…..#.#.,=.k|
| 67 cf 4b eb 2a 4d 9d 06 2a 7c 75 b5 d5 bf fc 47 |g.K.M..|u….G|
| 5e d0 5b cd 86 0e 77 03 58 1d 49 a7 a5 fb 22 a7 |^.[…w.X.I…".|
| e0 b0 1d 3b 90 7d cb 61 35 24 9a f2 3d 3d 14 49 |…;.}.a5$..==.I|
| 25 8a 05 2e da 0c ee f7 01 8d 9c 1f 63 75 49 ba |%………..cuI.|
| b7 ea 43 1e b7 75 53 a7 40 6b d7 45 d9 65 4a ef |[email protected].|
| 2c b8 7a a5 88 b6 21 ce f9 3e a2 c1 70 b4 2a a1 |,.z…!..>..p..|
| e5 38 59 52 88 48 ee 0f e6 8a 60 65 37 d9 76 3b |.8YR.H….`e7.v;|
| fb e6 f0 5d c0 5b 93 e7 8d 27 dd d0 7c 6c 4b 99 |…].[…'..|lK.|
| 0e 3f e2 fd da ba d4 1d c7 87 19 28 30 40 24 c2 |.?………([email protected]$.|
| 00 e3 96 13 68 20 8c 85 9d ab 9e 61 7b b8 f1 15 |….h …..a{…|
| 5b e5 cd a5 d0 19 bf 4b f9 56 3f 80 a6 a2 f6 37 |[……K.V?….7|
| 69 14 b6 e2 28 97 2c 6b fc 16 19 0e 67 75 eb b2 |i…(.,k….gu..|
| f3 85 3e 06 bd 76 10 73 95 e7 bf bf 73 f3 c7 57 |..>..v.s….s..W|
| 35 09 d9 e0 34 59 97 b6 40 af fd 64 5e dd e2 7a |[email protected]^..z|
| cd 81 7f 7b e0 8a 51 3c cc a9 93 9e ef 0b 64 5a |…{..Q<……dZ|
ssl_decrypt_pre_master_secret:RSA_private_decrypt
decrypted_unstrip_pre_master[256]:
| 07 f9 03 9c 86 87 14 37 b8 47 54 e2 b4 d8 45 04 |…….7.GT…E.|
| 73 28 ca b0 c0 14 7e 48 6b fb c1 01 9f 2e 4d ac |s(….~Hk…..M.|
| 16 b8 a0 b5 22 8b 47 9a f9 4f 81 b6 fb c6 c8 c6 |….".G..O……|
| ab af 11 8d c8 4c 6b 74 96 2c 9c f0 ef bb cf 3e |…..Lkt.,…..>|
| fd 3d 65 67 87 c9 ed 63 9d 1e 69 df 0f 48 86 47 |.=eg…c..i..H.G|
| f5 d7 9f ad 2e c4 46 39 68 b3 cf a8 83 8b 1f 6e |……F9h……n|
| f9 23 9b 7a f9 10 ff f2 0f 84 63 6c a9 25 0a 1f |.#.z……cl.%..|
| 48 7b 63 55 7b ab 3e 66 85 fd b7 71 9e eb 4f 8f |H{cU{.>f…q..O.|
| b9 af 94 13 98 75 52 1e 85 67 fc bd ba e5 f0 05 |…..uR..g……|
| 28 7d da e3 06 38 21 4b f1 7d 50 c3 9d 86 bd 83 |(}…8!K.}P…..|
| 3c 03 10 38 5a cf 3e 9d d8 73 b7 aa b5 f2 48 4b |<..8Z.>..s….HK|
| 74 af 39 4a fb e5 ce 33 27 e6 a6 08 a9 99 71 d1 |t.9J…3'…..q.|
| 80 a7 44 89 7e f4 9c 43 ac 57 2a ad fd ca 02 18 |..D.~..C.W…..|
| 2a a4 a7 3c 5d d8 32 dc fa e6 1e 30 14 53 7a a8 |*..<].2….0.Sz.|
| bb 5c f0 75 18 52 74 6e 3c 86 40 7d b4 af 2b 08 |..u.Rtn<[email protected]}..+.|
| d9 5f 75 cf 87 59 b8 88 6e dd a3 4f 27 ff ff ff |._u..Y..n..O'…|
pcry_private_decrypt: stripping 0 bytes, decr_len 256
ssl_decrypt_pre_master_secret wrong pre_master_secret length (256, expected 48)
ssl_generate_pre_master_secret: can't decrypt pre master secret
trying to use SSL keylog in c:\sslkeylogfile.log
failed to open SSL keylog
dissect_ssl3_handshake can't generate pre master secret
record: offset = 267, reported_length_remaining = 47
dissect_ssl3_record: content_type 20 Change Cipher Spec
dissect_ssl3_change_cipher_spec
packet_from_server: is from server - FALSE
ssl_change_cipher CLIENT
record: offset = 273, reported_length_remaining = 41
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 36, ssl state 0x17
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 32 offset 278 length 3561692 bytes, remaining 314
dissect_ssl enter frame #17 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 47
dissect_ssl3_record: content_type 20 Change Cipher Spec
dissect_ssl3_change_cipher_spec
packet_from_server: is from server - TRUE
ssl_change_cipher SERVER
record: offset = 6, reported_length_remaining = 41
dissect_ssl3_record: content_type 22 Handshake
decrypt_ssl3_record: app_data len 36, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
dissect_ssl3_handshake iteration 1 type 84 offset 11 length 1500765 bytes, remaining 47
dissect_ssl enter frame #19 (first time)
packet_from_server: is from server - FALSE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 318
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 313, ssl state 0x17
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 60867 found 0000000000000000
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #20 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 948
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 943, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #22 (first time)
packet_from_server: is from server - FALSE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 393
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 388, ssl state 0x17
packet_from_server: is from server - FALSE
decrypt_ssl3_record: using client decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 60867 found 0000000000000000
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #23 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 1460
need_desegmentation: offset = 0, reported_length_remaining = 1460
dissect_ssl enter frame #35 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 16409
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 16404, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #35 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 1111
need_desegmentation: offset = 0, reported_length_remaining = 1111
dissect_ssl enter frame #47 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 16409
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 16404, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #47 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 762
need_desegmentation: offset = 0, reported_length_remaining = 762
dissect_ssl enter frame #59 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 16409
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 16404, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #59 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 413
need_desegmentation: offset = 0, reported_length_remaining = 413
dissect_ssl enter frame #71 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 16409
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 16404, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #71 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 64
need_desegmentation: offset = 0, reported_length_remaining = 64
dissect_ssl enter frame #72 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 250
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 245, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #74 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 1460
need_desegmentation: offset = 0, reported_length_remaining = 1460
dissect_ssl enter frame #85 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 16409
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 16404, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #85 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 1111
need_desegmentation: offset = 0, reported_length_remaining = 1111
dissect_ssl enter frame #97 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 16409
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 16404, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #97 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 762
need_desegmentation: offset = 0, reported_length_remaining = 762
dissect_ssl enter frame #98 (first time)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 000000000A5D2280
record: offset = 0, reported_length_remaining = 1431
dissect_ssl3_record: content_type 23 Application Data
decrypt_ssl3_record: app_data len 1426, ssl state 0x17
packet_from_server: is from server - TRUE
decrypt_ssl3_record: using server decoder
decrypt_ssl3_record: no decoder available
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #8 (already visited)
packet_from_server: is from server - FALSE
conversation = 0000000005771098, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 223
dissect_ssl3_record: content_type 22 Handshake
dissect_ssl3_handshake iteration 1 type 1 offset 5 length 214 bytes, remaining 223
dissect_ssl enter frame #13 (already visited)
packet_from_server: is from server - FALSE
conversation = 0000000005771240, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 175
dissect_ssl3_record: content_type 22 Handshake
dissect_ssl3_handshake iteration 1 type 1 offset 5 length 166 bytes, remaining 175
dissect_ssl enter frame #14 (already visited)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 965
dissect_ssl3_record: content_type 22 Handshake
dissect_ssl3_handshake iteration 1 type 2 offset 5 length 77 bytes, remaining 965
dissect_ssl3_handshake iteration 0 type 11 offset 86 length 871 bytes, remaining 965
dissect_ssl3_handshake iteration 0 type 14 offset 961 length 0 bytes, remaining 965
dissect_ssl enter frame #16 (already visited)
packet_from_server: is from server - FALSE
conversation = 0000000005771240, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 314
dissect_ssl3_record: content_type 22 Handshake
dissect_ssl3_handshake iteration 1 type 16 offset 5 length 258 bytes, remaining 267
record: offset = 267, reported_length_remaining = 47
dissect_ssl3_record: content_type 20 Change Cipher Spec
dissect_ssl3_change_cipher_spec
record: offset = 273, reported_length_remaining = 41
dissect_ssl3_record: content_type 22 Handshake
dissect_ssl3_handshake iteration 1 type 32 offset 278 length 3561692 bytes, remaining 314
dissect_ssl enter frame #17 (already visited)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 47
dissect_ssl3_record: content_type 20 Change Cipher Spec
dissect_ssl3_change_cipher_spec
record: offset = 6, reported_length_remaining = 41
dissect_ssl3_record: content_type 22 Handshake
dissect_ssl3_handshake iteration 1 type 84 offset 11 length 1500765 bytes, remaining 47
dissect_ssl enter frame #19 (already visited)
packet_from_server: is from server - FALSE
conversation = 0000000005771240, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 318
dissect_ssl3_record: content_type 23 Application Data
association_find: TCP port 60867 found 0000000000000000
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #20 (already visited)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 948
dissect_ssl3_record: content_type 23 Application Data
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #22 (already visited)
packet_from_server: is from server - FALSE
conversation = 0000000005771240, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 393
dissect_ssl3_record: content_type 23 Application Data
association_find: TCP port 60867 found 0000000000000000
association_find: TCP port 443 found 0000000004D24240
dissect_ssl enter frame #13 (already visited)
packet_from_server: is from server - FALSE
conversation = 0000000005771240, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 175
dissect_ssl3_record: content_type 22 Handshake
dissect_ssl3_handshake iteration 1 type 1 offset 5 length 166 bytes, remaining 175
dissect_ssl enter frame #14 (already visited)
packet_from_server: is from server - TRUE
conversation = 0000000005771240, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 965
dissect_ssl3_record: content_type 22 Handshake
dissect_ssl3_handshake iteration 1 type 2 offset 5 length 77 bytes, remaining 965
dissect_ssl3_handshake iteration 0 type 11 offset 86 length 871 bytes, remaining 965
dissect_ssl3_handshake iteration 0 type 14 offset 961 length 0 bytes, remaining 965
dissect_ssl enter frame #16 (already visited)
packet_from_server: is from server - FALSE
conversation = 0000000005771240, ssl_session = 0000000000000000
record: offset = 0, reported_length_remaining = 314
dissect_ssl3_record: content_type 22 Handshake
dissect_ssl3_handshake iteration 1 type 16 offset 5 length 258 bytes, remaining 267
record: offset = 267, reported_length_remaining = 47
dissect_ssl3_record: content_type 20 Change Cipher Spec
dissect_ssl3_change_cipher_spec
record: offset = 273, reported_length_remaining = 41
dissect_ssl3_record: content_type 22 Handshake
dissect_ssl3_handshake iteration 1 type 32 offset 278 length 3561692 bytes, remaining 314

Hi,
I tried to open the file in the tar archive but there are not packets. The private key is missing also.
I'm using Wireshark 1.12.8 on Windows.
there is a .cap file and the private key inside:
Never mind, the extension of the file in the archive is missing, that confused me a little bit.
I can decrypt the sample traffic.
I run the browser on another VM, where Wireshark is installed.
Thanks
The Private Key uploaded to Wireshark is the one from the VM running IIS, right ?
Yes. I've uploaded the files here
the .pfx is password protected, can you send it as a pm it to me ?
The password is PasswordForCertificate.
Sorry, I forgot that.
I've also updated the file with the certificate in PEM format converted using openssl.
did you select any other other options beside the default ones ?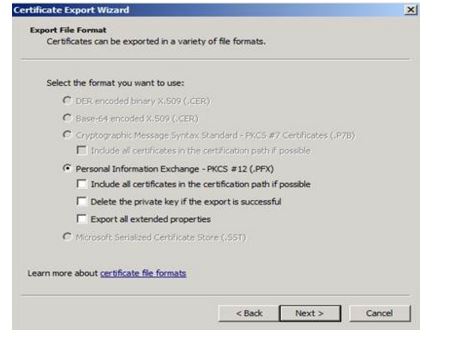
Yes the first and the last ones.
try to export it the same options selected as on my screenshot. next convert the private key file in PKCS12 format to PEM format:
openssl pkcs12 -nodes -in your.pfx -out key.pem -nocerts -nodes
c:\OpenSSL-Win32\bin> openssl rsa -in key.pem -out keyout.pem
let me know if that works
I didn't work...
can you please upload the new files...
I'm trying to post the link but I get invalid captcha...
I can't post it here because of SPAM filtering.
when you open the "keyout.pem" do you see it in the following format:
-----BEGIN RSA PRIVATE KEY-----
blablalablablalbalalbalbalbb blablalblalblablalbblblalba..
-----END RSA PRIVATE KEY-----
Yes. I've updated the contents of the first file I've shared with the new files.
Have you tested these files?
well, I'm still not able to decrypt it. Just to double check, you did the export on the server NOT the client, right ? and you are sure that it's the correct one ?
Yes. I do not have any other certificates on the server. I also tried with other cipher suites without any luck.
From https://wiki.wireshark.org/SSL
"The RSA key file can either be a PEM format private key or a PKCS#12 keystore. If the file is a PKCS#12 keystore (typically a file with a .pfx or .p12 extension), the password for the keystore must be specified in the Password field."
Tried with the .pfx you provided, still no luck. I'm puzzled.
Will try to reproduce it tomorrow.
I've tried that also.
Just tried with Wireshark 2.0.0.rc1 with the same results.
one note, the certificate and Private Key match (it was mentioned in other posts that a mismatch can cause issues) but this is not the case ...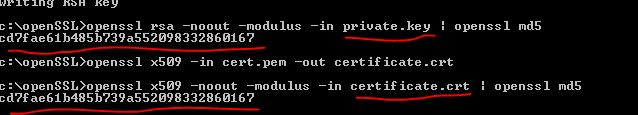
guys, please post comments as comments not "answers". I've just spent several minutes of my spare time cleaning up your "answers".
Please read the FAQ for more information.