I have a wireshark capture of implementations of DTLS protocol.I have the PSK and I have converted it to corresponding hex.DTLS uses TLS_PSK_WITH_AES_128_CCM_8 cipher suite. My question is hoe can I get the encrypted data from wieshark asked 28 Oct '15, 02:33 kalu |
One Answer:
To decrypt DTLS you don't need a PSK. What you need is the private key of the server, similar to SSL Decryption (actually it's technically the same). Hare are some online resources to start with:
After that, please use the following sample capture file (includes the private key) to make some tests and then apply that to your environment:
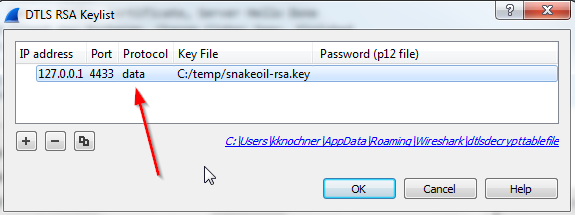
BTW: You'll have to add the RAS key for DTLS under
The Protocol field defines the protocol within DTLS, like SPDY or similar. If your protocol is unknown to the DTLS dissector (it will be flagged red if you try), please choose 'data'.
Decryption will work, but Wireshark won't be able to dissect the payload. In that case you can only see the decrypted data bytes in the packet bytes pane.
Regards answered 28 Oct '15, 09:26 Kurt Knochner ♦ edited 28 Oct '15, 10:03 |

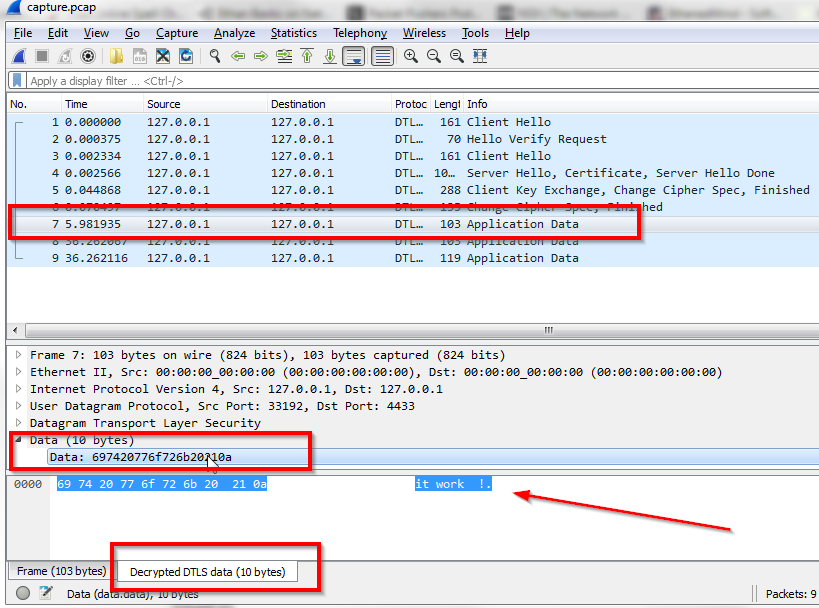
Hauke has added support for DTLS decryption using PSKs since v1.11.3-rc1-417-g0f05597, the preference should be visible at Preferences -> Protocols -> DTLS for 1.12 and newer. Wouldn't that work here?
Ah, you're right. I completely missed that enhancement! Thanks for the hint.