I am analyzing UDP traffic from one of the server. It is sending me multiple UDP packets with the same data. The only thing which is changing is "Time to leave" in IP layer. it is starting with 116 and then I get multiple UDP packets each with decrementing "Time to leave". ( up to 1 ) First of all I do not understand why I am receiving multiple packets. Second, how can I tell wireshark to skip all other (similar) UDP packets and keep only one ( since data is same )? I tried "editcap -d" without any luck. EDIT 1: I am trying to analyze the traffic between my console and game server. I do not know how server is configured. MY setup looks like below: pcap file can be found at: here asked 13 Nov '15, 13:06 ashitpro edited 13 Nov '15, 15:33 |
3 Answers:
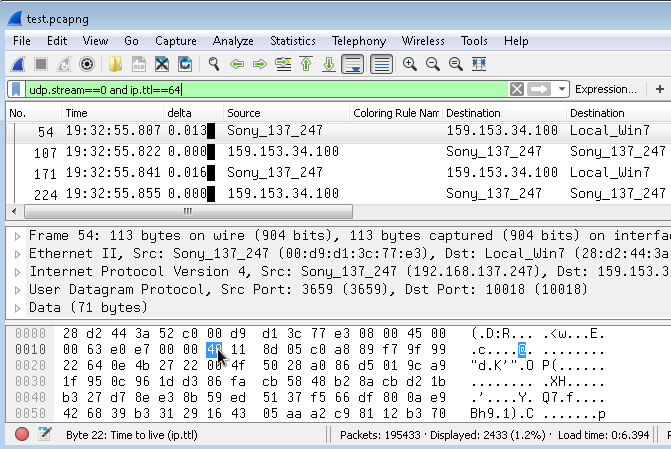
As the TTLs of the packets towards the PS4 are decrementetd - for whaterver reason - the TTL (Time to live - not Time To Leave) will also be 64 once as they are sent. TTL 64 is also the TTL for packets that are received from the console. So you can skip all those duplicates using udp.stream==0 and ip.ttl==64
answered 14 Nov '15, 10:57 mrEEde |
I would assume that there is a routing loop somewhere. The TTL is decremented with each pass of a packet through a router. Are they decrementing by one (so you get each packet 115 times) or faster? answered 13 Nov '15, 13:18 sindy Decrementing by 1. Hence I receive 115 packets. (13 Nov '15, 13:23) ashitpro Please provide some details regarding your network. Is the machine where you capture connected directly to the server, do you have just a single network card on the machine where you take the capture, do you have some capture/display filters set? What are the IP address and routing settings on the server and the machine where you take the capture And can you post the capture somewhere and provide a link? (13 Nov '15, 13:36) sindy I have added more information about my setup in question. Hope that helps. (13 Nov '15, 15:34) ashitpro OK. Please take & post another capture, this time on both the LAN and the WNC (if you are using Wireshark to capture, simply tick both interfaces before starting to capture, the result will be a pcapng file). Something is terribly wrong somewhere, the question now is where exactly. A capture at both interfaces should show whether your PC multiplicates the packets or whether they come that way from outside (and waste your connection bandwidth). The use of term "connection sharing" typically suggests that you use Microsoft Windows and that the PC acts as a router with NAT; however, 192.168.137.0/24 is not typical for such setup. So what is the OS on your PC? The "connection sharing" setup should be deducible from the capture at both interfaces. (14 Nov '15, 00:41) sindy |
You might want to take a look at this years Sharkfest presentation by Robert Bullen regarding his deduping tool "Super Deduper". It contains a download link on slide 15. https://sharkfest.wireshark.org/assets/presentations15/18.pptx answered 13 Nov '15, 17:04 Jasper ♦♦ |

With "windows 7 professional" OS - i am facing same problem ?