So....here's a snippet of what I have:
tshark -n -r _web-72.52.135.69-Mon-2015-11-30--19-36-02.pcapng
1 0.000000000 10.0.2.35 -> 72.52.135.69 TCP 66 61481â80 [SYN] Seq=0 Win=65535 Len=0 MSS=1460 SACK_PERM=1
2 0.068716000 72.52.135.69 -> 10.0.2.35 TCP 66 80â61481 [SYN, ACK] Seq=0 Ack=1 Win=14600 Len=0 MSS=1380 SACK_PERM=1
3 0.068913000 10.0.2.35 -> 72.52.135.69 TCP 64 61481â80 [ACK] Seq=1 Ack=1 Win=65535 Len=0
4 0.069064000 10.0.2.35 -> 72.52.135.69 HTTP 606 GET / HTTP/1.1
5 0.138513000 72.52.135.69 -> 10.0.2.35 TCP 64 80â61481 [ACK] Seq=1 Ack=549 Win=15344 Len=0
6 2.740825000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
7 2.740868000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
8 2.740878000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
9 2.740893000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
10 2.740899000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
11 2.740903000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
12 2.740946000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
13 2.740950000 10.0.2.35 -> 72.52.135.69 TCP 64 61481â80 [ACK] Seq=549 Ack=2761 Win=63880 Len=0
14 2.740952000 10.0.2.35 -> 72.52.135.69 TCP 64 61481â80 [ACK] Seq=549 Ack=5521 Win=61120 Len=0
15 2.741087000 10.0.2.35 -> 72.52.135.69 TCP 64 61481â80 [ACK] Seq=549 Ack=8281 Win=63880 Len=0
16 2.741091000 10.0.2.35 -> 72.52.135.69 TCP 64 [TCP ACKed unseen segment] 61481â80 [ACK] Seq=549 Ack=11041 Win=61120 Len=0
17 2.741093000 10.0.2.35 -> 72.52.135.69 TCP 64 [TCP ACKed unseen segment] 61481â80 [ACK] Seq=549 Ack=13801 Win=58360 Len=0
18 2.742424000 10.0.2.35 -> 72.52.135.69 TCP 64 [TCP ACKed unseen segment] 61481â80 [FIN, ACK] Seq=549 Ack=13801 Win=65535 Len=0
19 2.809661000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP Previous segment not captured] [TCP segment of a reassembled PDU]
20 2.809680000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
21 2.809682000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
22 2.809710000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
23 2.809774000 72.52.135.69 -> 10.0.2.35 TCP 1438 [TCP segment of a reassembled PDU]
24 2.809789000 72.52.135.69 -> 10.0.2.35 TCP 625 [TCP segment of a reassembled PDU]
25 2.809792000 72.52.135.69 -> 10.0.2.35 TCP 64 80â61481 [FIN, ACK] Seq=21268 Ack=549 Win=15344 Len=0
tshark (version 1.12.6) doesn't seem to be able to see the HTTP response, which is in packet #6:
HTTP/1.1 200 OK
Date: Mon, 30 Nov 2015 19:35:21 GMT
Server: Apache/2.4.16 (Unix) OpenSSL/1.0.1e-fips mod_bwlimited/1.4
X-Powered-By: PHP/5.4.45
Set-Cookie: _PHP_SESSION_PHP=351; expires=Mon, 07-Dec-2015 19:35:21 GMT; path=/
Vary: Accept-Encoding,User-Agent
Content-Encoding: gzip
Content-Length: 20911
Connection: close
Content-Type: text/html
I see the same thing in Wireshark 2.0. Any clue on why this isn't been seen as HTTP? Thank you.
asked 30 Nov '15, 13:19

DigiAngelXX
21●6●6●11
accept rate: 0%

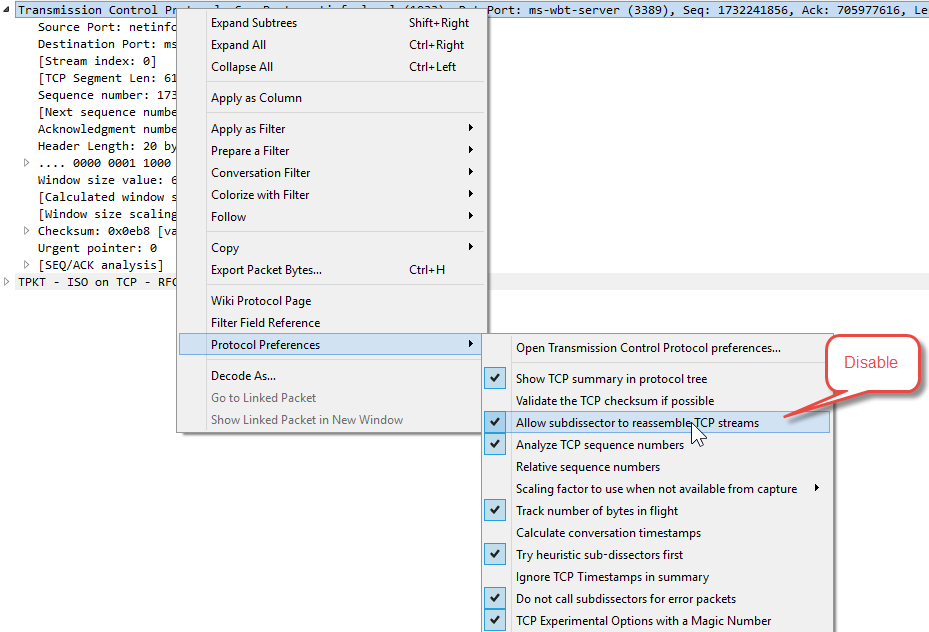
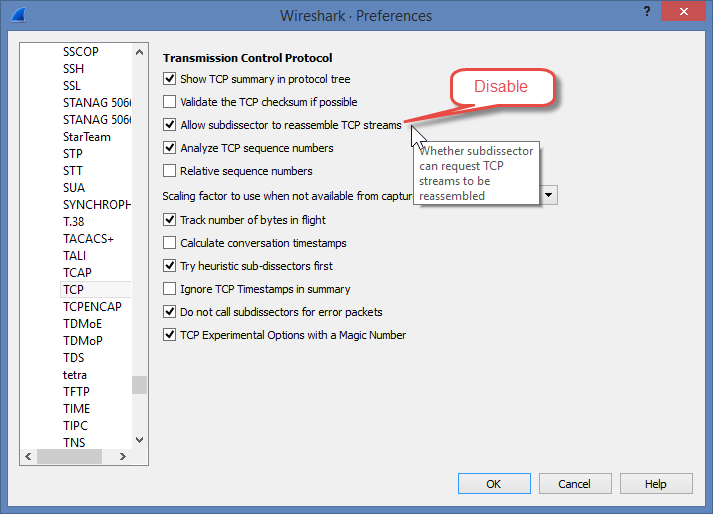
That totally did the trick...thank you very much.
Hint:
If an answer has solved your issue, please accept the answer for the benefit of other users by clicking the checkmark icon next to the answer. Please read the FAQ for more information.