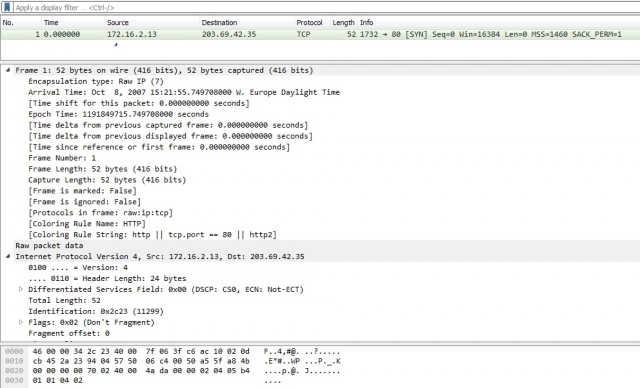
Hi, I have a problem with a Wireshark produced PCAP-file. With Wireshark I exported 1 packet in a seperate PCAP-file, which demonstrate the issue: This is a dropbox link to a PCAP File with 1 packet. If I load this PCAP in WireShark I nicely get a TCP and IP header, see sreenshot below. The problem is that if I try to load this using:
Results in: Now CAPINFOS reveals that this PCAP file is Raw IP encapsulation, where correct readable ones are Ethernet encapsulated. I tried to convert the PCAP file using: editcap -T ether t_0.pcap t_.new.pcap The encapsulation is now reported as Ethernet, however even in WireShark the TCP and IP header are now gone. So my question is: What is wrong with this Wireshark generated 1 packet file, causing that it cannot be read by WinCap/DPTK? How can I modify this pcap file to get it processed by WinPcap and get TCP and IP headers? Thanks.
asked 27 Jan '16, 23:51 Jos edited 27 Jan '16, 23:57 |
3 Answers:
No, you don't. libpcap/winPcap don't parse any headers for you.
The I.e., a pcap file with type "Raw IP" HAS packets that contain IP headers - each packet begin with an IP header. Do not look for an Ethernet header, because there are no Ethernet headers - or any other headers before the IP header.
No, you get an IP header - no Ethernet header. If JNetPcap can't handle "Raw IP" packets, then it can't handle your capture file (and it's not as good a library as it could be, because it certainly could handle "Raw IP" packets).
Don't use
Because that's what it is.
Correct pcap files can have ANY of these encapsulations; they are NOT necessarily Ethernet-encapsulated. There may be some lesser tools that can only handle Ethernet encapsulation, but the better tools can read more than just Ethernet-encapsulated pcaps; at minimum, a good tool or library should be able to handle Ethernet, 802.11, 802.11 with radiotap, Raw IP, and
Nothing. Something is, however, wrong with:
For JNetPcap, try first using the GetValue method of the DataLinkType class to get the encapsulation, and:
For DPKT, use answered 28 Jan '16, 03:00 Guy Harris ♦♦ |
Technically there's nothing wrong with the capture. What you need to appreciate is that the encapsulation is "Raw IP", while you seem to insist of getting it interpreted as Ethernet, which it is not (since there is no Ethernet header, forcing the encapsulation to 'ether' by means of editcap just makes the file header incorrect with respect to the content of the frame(s) and therefore Wireshark cannot interpret the manipulated capture file anymore either). So, whatever you are doing using WinPcap or DPTK, stop interpreting it as an Ethernet frame, which it isn't, and look at it as an Raw IP frame, which it is. answered 28 Jan '16, 00:22 Jaap ♦ Thanks, but for my research I want to get access to IP/TCP/UDP/ARP etc headers.Of course I can parse everything directly by hand, but the idea that I have lib/winpcap to do this for me. So I want to know how I can convert this RAW PCAP to a PCAP which WinPcap/LibPcap interprets as IP/TCP/UDP-headers. Since WireShark is showing TCP/IP/etc. headers in the Window, I assume there is some way to convert RAW PCAP to an "enhanced" PCAP format. Also I have multiple PCAP-captures of which the most are not raw (so I can extract IP/TCP/UDP headers with libpcap), so it would be nice if I can convert the raw ip to this form, so I can process them with 1 data extraction algo. (28 Jan '16, 00:47) Jos
You have access to them if you're willing to parse the raw packet data, and if JNetPcap can handle
No, you have JNetPcap to do it for you. libpcap/WInPcap doesn't do any parsing of packet data.
The only place where libpcap/WinPcap interprets the headers is in packet filtering, where it compiles a filter expression into BPF "machine code" to check whether the filter matches or not - and that code does handle
You assume incorrectly. For one thing, "RAW" isn't a different format of pcap, it's a different link-layer header type code; there's no "enhancement" involved. For another thing, Wireshark shows the headers because it has code to parse them - or, rather, it has code that does not try to parse link-layer headers for (28 Jan '16, 11:02) Guy Harris ♦♦ |
I found the solution. RAW IP PCAPs should first be processed by The output file has nicely some TCP and IP headers. answered 28 Jan '16, 02:06 Jos What you are doing here is adding a fake Ethernet header. While this does allow you to then not rewrite your pcap processing code to handle Raw IP, it's an extra step in your workflow that could easily be avoided if you re-read the answer from @Guy Harris on how you should handle a pcap that has either Ethernet or Raw IP. (28 Jan '16, 04:07) grahamb ♦ |

Guy,
Thanks for your comment, but:
Why should I go for your solution, and not inject fake Ethernet headers with tcprewrite as I wrote here above. If I inject fake Ethernet headers, I also get access to JNetPcap PcapPacket.getHeader(tcp) (and IP/UDP).
You wrote: "libpcap/winPcap don't parse any headers for you.". He? But I can do in JNetPcap for example myPacket.getHeader(tcp), and then I get a TCP object. So JNetPcap/WinPcap is indeed parsing.
@Jos, most people answering questions on this site prefer to provide answers which are generic in terms that someone else asking a similar question can make use of an existing answer. That's why, I guess, @Guy Harris has spent so much time to comment the individual steps of your description.
If you look for the fastest method to handle a single capture taken as "raw IP" encapsulation (to say "raw" and to say "raw IP" is quite a difference) using an existing tool which can only process ethernet encapsulation, then your approach (use editcap to augment the raw IP packets with forged, meaningless, but formally correct ethernet layer) is the correct one; if you want to handle such captures systematically, Guy's suggestion to modify your tool in such a way that it would take the information about encapsulation type into account and start parsing the packet from the corresponding layer is the correct one.
The pcap file indicates the encapsulation type in order to allow the parsing application to choose the proper entry point to the parser without need to tell it so "manually".
Yes. In JNetPcap. Are you sure that JNetPcap is a mere wrapper of WinPcap, or it also has some parsing logic in it?
JNetPcap MOST DEFINITELY has parsing logic in it. THAT is why it's doing parsing; the parsing is NOT being done by libpcap/WInPcap, it's being done by the ADDITIONAL parsing code in JNetPcap.