I know how to use the filter on both Wireshark and Tshark, however, I want to go even deeper into the analysis of the data. To do this I want to access only the physical layer transmissions of the specified type. For example, the following drag-n-drop batch file will filter out all IP packets in a pcap file: My dilemma is that I only want the times at which IP packets were sent at the physical layer, not all layers. What do I need to do (/add to this batch file) to filter those packets out? A Tshark approach is much more preferred. asked 17 Feb '16, 08:27 Midimistro |
2 Answers:
If you want a general solution, there isn't one. If you want a solution for a particular link layer, try, for example, "eth.type == 0x0800 || eth.type == 0x86dd" for IPv4 or IPv6 directly atop Ethernet. However, that won't filter out Ethernet transported atop some other protocol ultimately running atop physical Ethernet. There is no solution for that. answered 18 Feb '16, 00:23 Guy Harris ♦♦ |
Could you slice the capture with editcap so there is nothing beyond the first IP layer, e.g. answered 18 Feb '16, 03:15 grahamb ♦ Thats not what I am looking for. What I am trying to do is get packet information from the PHY layer as described in this picture and only that data, no other layer info (aka I want to leave out all the layers above it):
If this is possible, let me know. Whether it be the IP packets themselves or the transport block, as long as its one or the other, and not both, that's what I am looking for. (19 Feb '16, 04:37) Midimistro Can you show a picture of the packet tree in Wireshark indicating the data you want? Even better, add a capture as well. (19 Feb '16, 04:42) grahamb ♦ I can add a small snapshot, but because the data is confidential, I cannot release the capture. (19 Feb '16, 12:19) Midimistro |

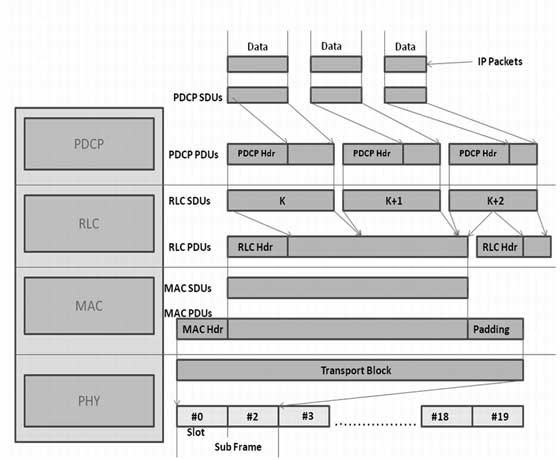
Are you saying that the timestamp you get now is something different? Are you aware where this timestamp comes from and what it represents?
I am quite aware of where these timestamps come from. The filter above includes all the instances of the IP protocol, whether the instance is in the physical layer or not. What I am looking for is physical layer IP instances, and nothing more.