In a malware pcap file, saw a client keep doing DNS requests on the same hostname, wonder what could be happening? Any theories? Here is the pcap: https://www.dropbox.com/s/3a43pp28t067lyy/consecutiveDnsReqs.pcap?dl=0
asked 02 May '16, 10:08 pktUser1001 |
One Answer:
Most likely caused by a program that doesn't cache results, or which is simply coded to check for this name all the time (for whatever reason, but it ain't for stealth). answered 02 May '16, 11:00 Jasper ♦♦ |

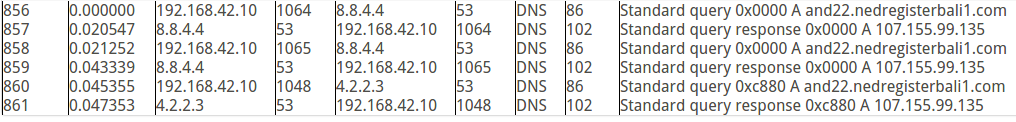
That's possible, but my problem is why the client didn't do anything (for example, start a new TCP connection) after getting the DNS response, instead it immediately sent the same DNS request.
Maybe the DNS reply is a signal and the malware will only communicate when a certain IP is returned. This sometimes happens to avoid putting suspicious TCP/UDP traffic on the internet link when there's nothing the C&C servers want to tell their bots. Mostly they return loopback IPs for those DNS queries, though (or used to), but loopback answers are suspicious enough on their own.
In the end, you can't tell without reverse engineering the binary that did the name lookups.
Again, asking for the same thing in such a quick way is stupid.