I'm facing an issue where a ftp transfer hangs sometimes when TLS records are exceeding the 2^14 limit defined in RFC5246 is exceeded. asked 26 Nov '16, 01:12 mrEEde |
One Answer:
The FTP server (or its TLS library) is faulty. RFC 5246 (TLS 1.2), page 20 explicitly forbids larger sizes ("MUST"):
The client rightfully fails the TLS session with an Alert message since larger values are illegal by the spec. answered 26 Nov '16, 02:31 Lekensteyn |

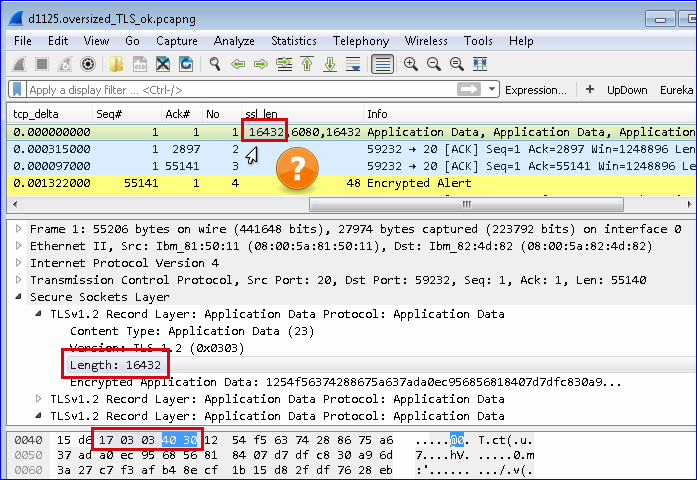
As this seems to be out in the wild, should we add an Expert Info for this?
Proposed patch that adds expert info for this: https://code.wireshark.org/review/18959