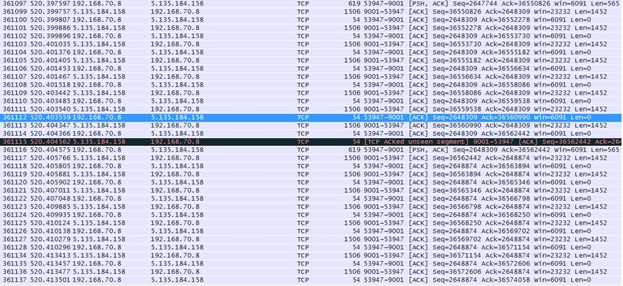
Hi i have a packet capture of a attack on our network. It was reported that users felt the network was slow for many applications and the internet. Upon starting the capture we notice the network was back to normal. I notice many ACK packet which might be normal attack but I read somewhere many ACK packet can also be DOS attack. Without the packet capture from earlier, how do i tell the difference between a normal traffic data flow and after attack from DOS ?
asked 08 Dec '16, 04:09 doran_lum |
One Answer:
I wouldn't call it as an attack. But of course you can. What you see is bandwidth consuming traffic to the internet on port 9001 (TOR). The difference of normal and not normal traffic can be only find by baseline and then defining rules out of that. And in the end you can close a lot of ports which you don't need. answered 08 Dec '16, 04:53 Christian_R edited 08 Dec '16, 23:21 |