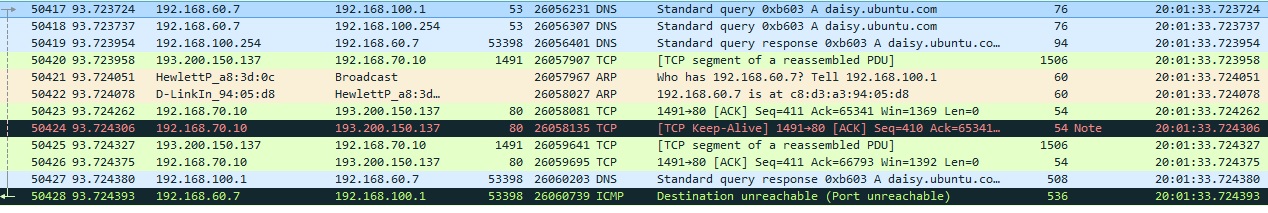
Hi all, can this be consider ARP sproofing ? How can I find ARP sproofing because when i filter by arp i couldn't see it 192.168.60.7 was able to reach 192.168.100.1 then later there's a request to ask who is 192.168.60.7 finally i can see 192.168.60.7 unable to reach 192.168.100.1 at packet 50428
asked 12 Dec '16, 04:10 doran_lum edited 12 Dec '16, 21:08 Guy Harris ♦♦ |
2 Answers:
Your screenshot looks more like a normal arp cache update as it is discussed here: https://ask.wireshark.org/questions/57174/seeing-lots-of-arp-requests-even-though-the-hosts-have-the-mac-address-in-their-arp-cache-already ARP spoof looks like this: 192.168.2.1 is at ab:ab:ab:ab:ab:ab And 192.168.2.1 is at 10:10:10:10:10:10 Where the mac addresses are just examples. answered 12 Dec '16, 04:37 Christian_R |
This is how ARP-spoofing attack looks in Wireshark: Wireshark warns you by the message "(duplicate use of <ip> detected!)". In my case I used Intercepter NG to make the attack. You can use filter expression "arp.duplicate-address-detected" to quickly find if there are any such occurences in your trace. answered 12 Dec '16, 07:01 Packet_vlad edited 12 Dec '16, 07:03 |