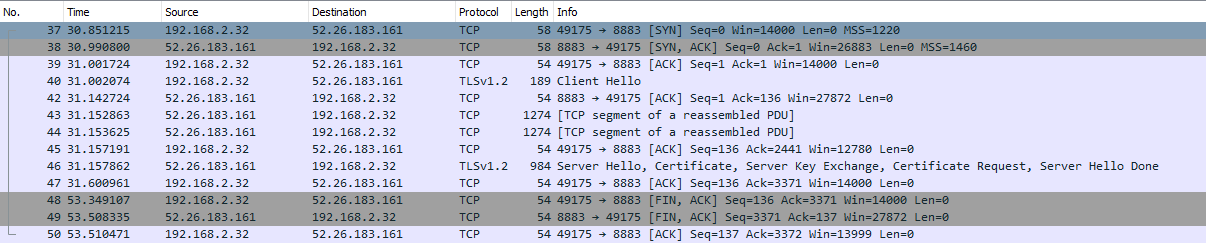
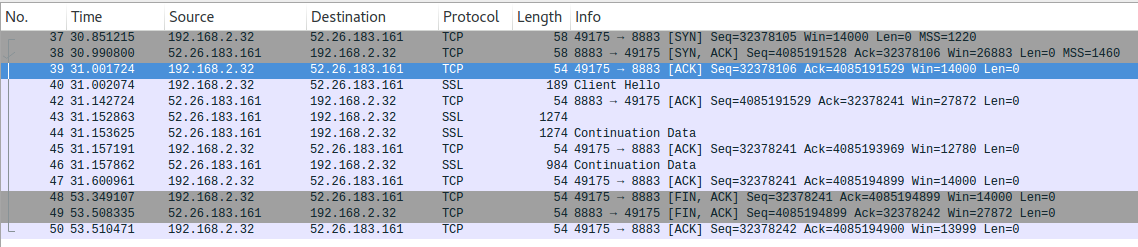
I'm trying to look at the TLS handshake messages for a session, and I am getting different results when I open the capture in Wireshark 2.2.5 in Windows 10 vs Ubuntu 16.04. In Windows it identifies the protocol as TLSv1.2 and shows the Client Hello and Server Hello messages. In Ubuntu it just shows the Client Hello, and then the rest of the messages are left uninterpreted as just SSL. I installed Wireshark from http://ppa.launchpad.net/wireshark-dev/stable/ubuntu What am I missing in my Linux install that would let it interpret the Server Hello message? Thank you so much! Screenshots of the capture are below. Capture From Windows 10: Capture from Ubuntu 16.04 asked 10 Apr '17, 16:36 DevinCallahan |
One Answer:
Given that the protocol is just "SSL" (rather than a more specific version like "TLSv1.2") and given that some packets are reported as "Continuation Data", I think that you have disabled TCP reassembly. To enable TCP reassembly, right-click on the TCP layer, select Protocol Preferences and check the Allow subdissector to reassemble TCP streams option.
answered 12 Apr '17, 14:12 Lekensteyn That was it! Thank you so much! (12 Apr '17, 14:16) DevinCallahan |

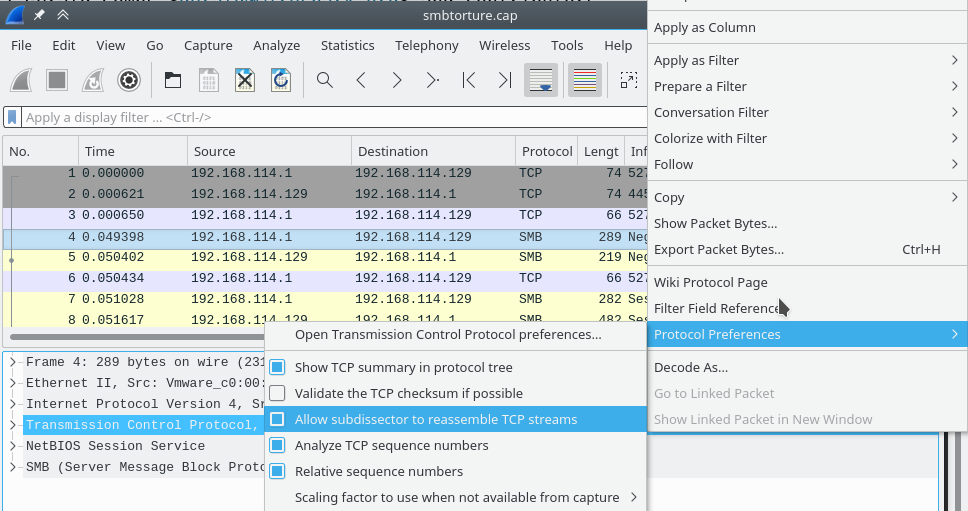
On Ubuntu it seems like reassembly is not working, is it the same Wireshark version on both systems? if so compare your preference settings.