Hi All, Just found the following thread on TNS dissecting... is it still there or TNS dissecting has been made possible by now? https://www.wireshark.org/lists/wireshark-users/201205/msg00022.html Here's the SQL transaction that I'd like dissected if possible: h̶t̶t̶p̶s̶:̶/̶/̶d̶r̶i̶v̶e̶.̶g̶o̶o̶g̶l̶e̶.̶c̶o̶m̶/̶o̶p̶e̶n̶?̶i̶d̶=̶0̶B̶3̶1̶e̶4̶7̶U̶c̶q̶t̶4̶B̶d̶m̶t̶t̶a̶G̶R̶s̶c̶j̶E̶3̶Q̶k̶U̶ Update: Correct trace this time: https://drive.google.com/open?id=0B31e47Ucqt4BaHY3dDRHczBVWDA Many thanks in anticipation! asked 11 Apr '17, 10:11 Dmitriy edited 12 Apr '17, 09:08 |
2 Answers:
Uhm... I see no TNS traffic in your capture file. However, the TNS dissector has been updated recently, if you download an automated built version from https://www.wireshark.org/download/automated/ you can see whether your TNS traffic is dissected now. Beware that the automated built versions could be buggy as are built after adding new code to the git repository. answered 12 Apr '17, 06:05 SYN-bit ♦♦ |
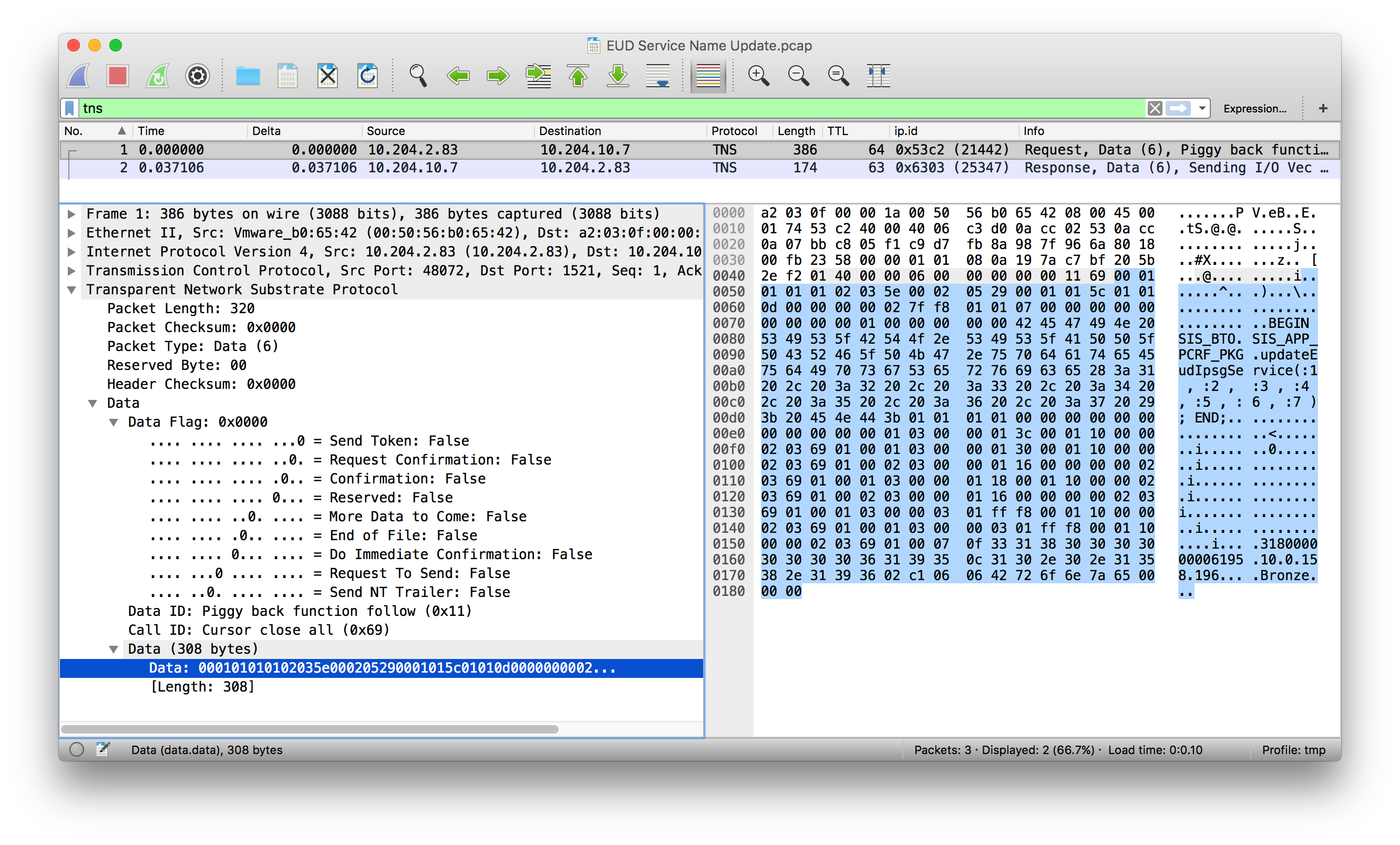
This is how the current code base dissects TNS:
The specific function numbers are now dissecteed, but for dissecting the SQL queries and response data the dissector would need to be extended some more. answered 12 Apr '17, 08:55 SYN-bit ♦♦ SYN-bit: "for dissecting the SQL queries and response data the dissector would need to be extended some more" - that's exactly what I'm after ideally. Is it realistic based on the time/effort required? (12 Apr '17, 09:04) Dmitriy Not sure what you mean by "realistic" but it would need someone to take interest in writing the code AND this person would need to have access to a lot of different TNS tracefiles to test the code against (TNS is a proprietary protocol so there are no protocol definitions to work from and everything needs to be reverse engineered). (12 Apr '17, 09:11) SYN-bit ♦♦ Are dictionaries applicable here? I have some experience tailoring RADIUS/DIAMETER ones to our specific requirements and would be happy to contribute by means of developing a custom TNS dictionary based on the traces with our queries (unfortunately I can't do any coding)... if that helps at all. (12 Apr '17, 10:23) Dmitriy Nope, the TNS dissector does not use any dictionaries. But if you are able to create capture files with all kinds of variations of the protocol with descriptions of what means what in the tracefiles, I could help write the C code to implement it. (14 Apr '17, 00:32) SYN-bit ♦♦ Sorry what I implied was if it's possible to make that TNS dissector use dictionaries, which could then be tailored by the users to suit their needs (like other dictionaries such as RADIUS/DIAMETER ones): I thought that'd help remove the need to cover all kinds of variations at the time of working on dissector code. Meanwhile I could try obtaining various traces from our lab but doubt it'll cover all kinds of variations that exist. SQL/TNS is just one of many interfaces in our current project that I need to test as part of my job. (14 Apr '17, 04:31) Dmitriy OK I've just requested our 3rd party partner who supply their own DB for our project to supply requested traces along with the comments. It'll take them a while, so I'll be back when ready. (21 Apr '17, 04:48) Dmitriy An enhancement request should be made for this on the Wireshark Bugzilla, and any captures and comments attached to it. (21 Apr '17, 08:38) grahamb ♦ Sure: I'll take care of that. (21 Apr '17, 08:59) Dmitriy showing 5 of 8 show 3 more comments |

SYN-bit:
Thanks for your reply. I'd need my other laptop to try an automated built version as you advised (will do it soon); meanwhile is your Wireshark not showing the same as mine in this screenshot here? https://drive.google.com/open?id=0B31e47Ucqt4BaFJub1lXdXkycXM
I see a SOAP query over HTTP in your capture. I suspect you've uploaded or provided a link to, the "wrong" capture.
Sorry is this one any better? https://drive.google.com/open?id=0B31e47Ucqt4BaHY3dDRHczBVWDA (just noticed I had another trace with HTTP POST in it nearby, so I must've supplied a link to it by mistake)