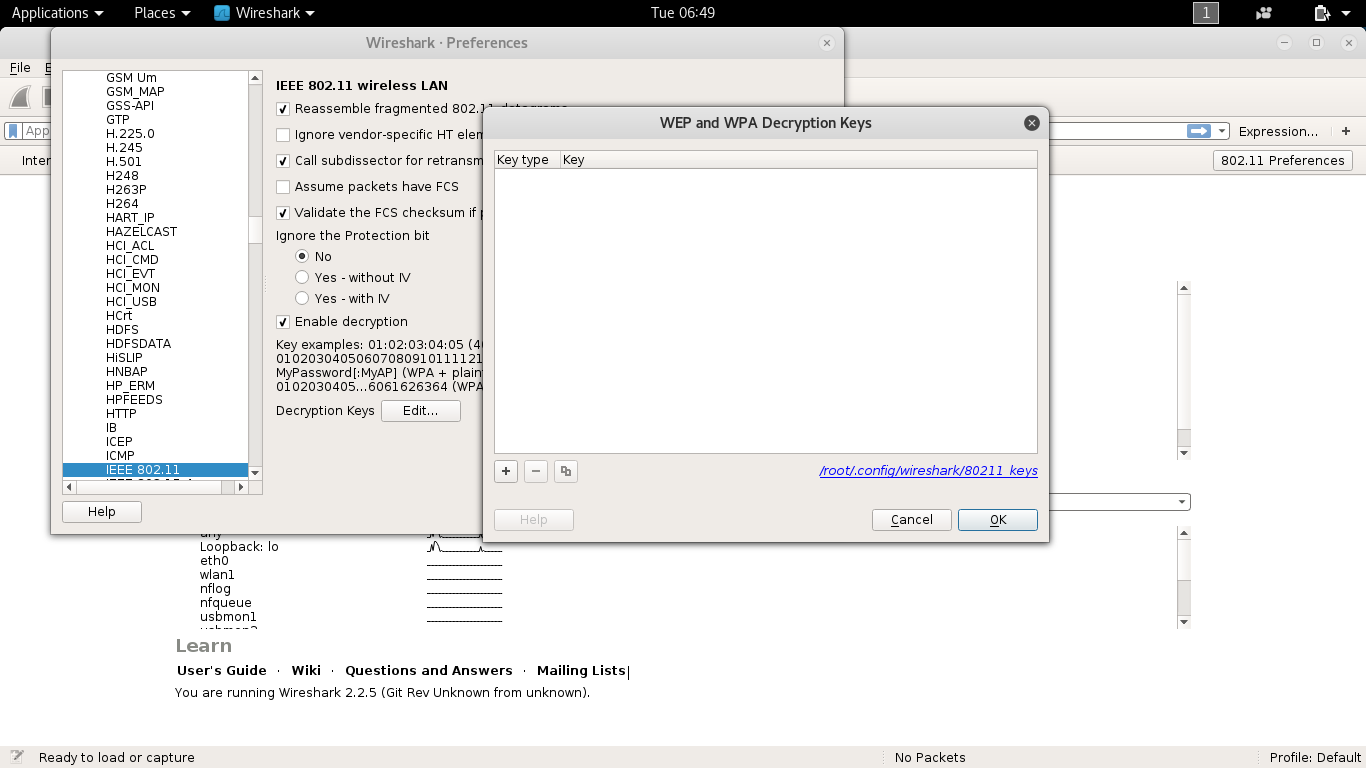
I have captured full four EAPOL handshakes. But the data captured were not decrypted (always show 802.11 protocols). Can you give me some directions, how can I decrypt the captured data. screenshot:
Thanks, --William asked 17 May '17, 19:28 dknovo edited 23 May '17, 07:29 grahamb ♦ |
3 Answers:
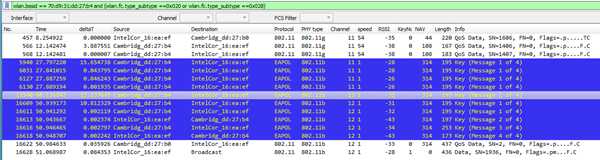
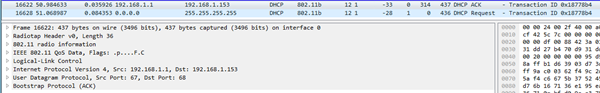
One of the common causes of possible WPA2 decryption issues is that there are, in fact, no data to actually decrypt. This is often due to modulation differences in the data frames under review, or sometimes even more fundamental issues such as sniffing on the wrong channel or band, or even not having monitor/promiscuous mode capability at all. For the sample trace provided, there is one full EAPOL handshake present with Looking at a beacon for this BSSID, no HT is supported so it would only be an 802.11b/g capable access point. filter: wlan.bssid == 70:d9:31:dd:27:b4 and wlan.fc.type_subtype == 0x08 This is somewhat good, as this type of traffic will be easier to capture. I notice the trace is taken VERY close to the AP as the RSSI is very high and I see bleed through into other channels. You might want to move away a meter or two from the AP, maybe have a -40 or so RSSI instead of -25. To see if there is anything to decrypt, we can check for any Data or QoS-Data frames, noting we will only have QoS-Data frames if WMM is available on both STA and AP (and it is if you look at the Association Request/Response frames): filter: wlan.bssid == 70:d9:31:dd:27:b4 and (wlan.fc.type_subtype ==0x020 or wlan.fc.type_subtype ==0x028) I see two possible frames to decrypt AFTER the EAPOL handshake, but that is it (frames 16622 and 16628):
After applying your SSID/Passphrase, these frames do, in fact, decrypt:
So this confirms a number of things:
Recommendations:
answered 26 May ‘17, 03:52 Bob Jones Hi Bob Jones, Thank you for your valuable inputs. I will try these recommendations and then update the result to you. Once again, thank you so much. Best and regards, –Will (27 May ‘17, 02:09) dknovo |
I have an issue with sniffing a WiFi network with the SSID = "Public Wifi". That would indicate that the network is available to many users and is not a closed, personal network. answered 25 May '17, 06:53 Amato_C Good catch (25 May '17, 07:15) Christian_R @Amato_C, "Public Wifi" is my wireless home network named by me. There are 4 devices (users) accessing the network including (2 laptops, 2 phones). And I sniffed data from a laptop as you saw on the uploaded file. The victim laptop is close to the Linux machine that I used to capture data. Any suggestion for me to decrypt the captured data, or will I capture again new file to you? Thanks, --Will (25 May '17, 08:05) dknovo Could you perform a new capture without using the word "Public WiFi". Maybe something like "Will's Home net" or something like that? Sorry for the inconvenience, but trying to protect everyone involved. (25 May '17, 08:55) Amato_C |
In some cases it helps to toggle the combo box in the wireless toolbar from "Wireshark" to "None" and back to "Wireshark": https://ask.wireshark.org/questions/60947/why-isnt-wireshark-decrypting-80211-traffic-in-my-capture-even-if-the-eapol-handshake-is-present/60951 answered 18 May '17, 13:17 Christian_R edited 18 May '17, 13:24 Hi Christian_R, Thank for your input, However, there is no combo box as you mentioned in the Wireshark version I'am using now (2.2.6 version - the latest Wireshark version). Therefore, I cannot decrypt the captured data. Any other solution can I try? Thanks, -William (22 May '17, 00:44) dknovo What OS do you use? The same combobox Canberra found in the decryption key dialogue. (22 May '17, 09:42) Christian_R Hi Christian_R, I'am using Kali Linux and the Wireshark's version is Wireshark 2.2.5 (Git Rev Unknown from unknown). I cannot find out the combo box. I attach the image below, I will present my problem again at the beginning step until now, so that you can trace off my problems more easily. Thanks (23 May '17, 07:04) dknovo Hi Christian_R, My problem is that: I use the TL-WLN722N wireless USB (that support Monitor mode) to sniff data from devices like laptops, smartphones or anything else accessing to my home network. I completed all steps about setting: enable 'monitor mode', use airodump-ng to view wireless data from around APs and select the AP with a specific target to test. (Here, I take my home AP to test) wpa : my wireless network name pwd : my wireless network password I use WIRESHARK tool on Kali Linux to capture data from a target laptop (at wlan1mon interface, my AP channel) then I use aireplay-ng to deauthenticate the target laptop, btw I can capture full 4 handshakes EAPOL protocol, After that, I choose 802.11 Preference view, add new key (WPA-PWD: mywirelesspassword:mywirelessname), and another try with (WPA-PSK): However, I cannot decrypt the 802.11 protols capture from the target laptop as well as from my AP. I read documents and try many solutions, but It seems hopeless, I need your help Please give me some instructions, how can I decrypt and view the data capture from the target. Let's me know if you need more information Thanks, --William (23 May '17, 07:10) dknovo Have you tried: 1. Saving only the traffic to/from the WiFi client and the AP? You can use the display filter wlan.addr== followed by the WiFi MAC address of your WiFi client. Then save that file, re-open with Wireshark.
Are you able to share the capture and provide the passphrase? I could try it on my Wireshark to see if the problem exists. (23 May '17, 10:28) Amato_C Be sure you have Data frames or QoS Data frames to decrypt... sometimes these 'can't decrypt' questions turn out to be that there is no data to decrypt due to modulation differences between the traffic flow from client to AP and what the capture adapter can pick up. (23 May '17, 12:40) Bob Jones Can you share us a small trace? (23 May '17, 12:48) Christian_R Hi All, Thank you for your inputs. @Amato_C, I have tried both your solutions, but the problem still exits, 802.11 protocols are not decrypted. @Bob Jones, I didn't capture Qos Data frames, you can check my uploaded files for more details, can you give some solutions how can I capture and decrypt Qos Data frames? @Christian_R, I uploaded my test file to the mediafire with a README file including my AP's name and my wireless network password. You can download the file to check. Please let's me know if you need more information. Link download files. http://www.mediafire.com/file/4svwj51b8sqb645/test%282%29.pcapng http://www.mediafire.com/file/8mdyofiq3jtc1wb/README.txt Thanks, --William, (24 May '17, 09:24) dknovo Your "answer" has, yet again, been converted to a comment as that's how this site works. Please read the FAQ for more information and follow the conventions. (24 May '17, 09:50) grahamb ♦ @Amato_C Looks strange. The trace is full with Deauthentication frames.... (24 May '17, 22:31) Christian_R @Christian_R, I used aireplay-ng --deauth command to force the victim client reconnect to the wireless network to capture full 4 EAPOL handshakes. Is something wrong? Let's me know if you need more information. Thanks, (24 May '17, 23:44) dknovo I think the trace contains no data. There is the EAPOL handshake and right after that the DEAUTH. (25 May '17, 00:40) Christian_R You mean that Wireshark cannot sniff wireless packets even though we capture EAPOL handshakes? After forcing the victim client reconnect to the wireless network, the victim still used internet for a while (surfing websites, reading articles, listening musics ...) before I stopped to capture the wireless packets. Any suggestion for me to capture the trace with data? Or Will I change another method to sniff wireless data like Evil Twin, MitM attacks ... Thanks, (25 May '17, 01:20) dknovo showing 5 of 13 show 8 more comments |

This question was originally posted as an "answer" to this question.