I've been investigating an issue caused in combination with our proxy. During analysis it appears the TLS handshake protocol is either not followed or something else is happening. I would like to ask someone else to take a look and perhaps explain what might be happening. Filtering only on the SSL communications, it appears the first two steps go OK. There is a Client Hello, Server Hello, then there are suddenly a couple of Encrypted Handshake Messages followed by a regular Server Key Exchange + Server Hello Done. What I am missing here is the Server Certificate, which I can only assume is sent in the Encrypted Handshake Messages. I made sure to clear my cache but this keeps occuring. Is it possible to send the server Cert in an encrypted handshake? How does this work? This is a capture made by browsing to www.timeanddate.com. From my corner of the globe, it resolves to 192.33.31.72. Another server like 151.101.60.69 does not show this behavior.
asked 05 Jul '17, 00:50 JoepMeloen86 |
One Answer:
You are affected by a shortcoming in the current SSL/TLS dissector (up to version 2.4) which is tracked by https://bugs.wireshark.org/bugzilla/show_bug.cgi?id=3303 The problem is that your certificate message is quite large and spans multiple TLS records. This scenario is currently not supported in Wireshark, there is no reassembly of TLS handshake messages yet. I am working on this, hopefully it will be available in version 2.6. answered 05 Jul '17, 08:40 Lekensteyn edited 05 Jul '17, 08:41 Thanks for the answer. Looks like this is what i'm experiencing. (05 Jul '17, 23:43) JoepMeloen86 |

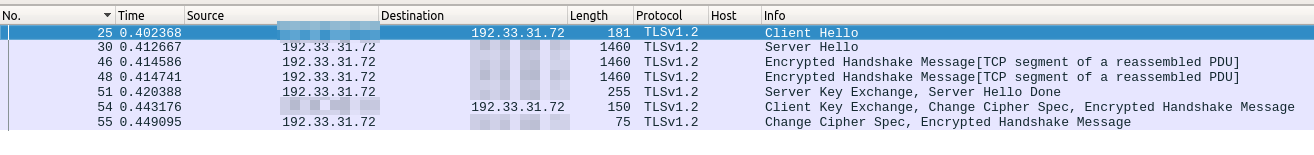
Full length frames (see the length of these frames) suggest to me that if you play with the various reassemble settings you may see something else. My assumption is that Wireshark can't make heads or tails from the individual frames, since these are part of a larger PDU. It therefore falls back to assuming that it's an Encrypted message.
Can you share a capture in a publicly accessible spot, e.g. CloudShark?
Thanks for the comments Jaap. It does appear the certificate is listed in the bytes (it's quite a long list).
Is this a shortcomming of Wireshark? Or (taking into account we have issues with this website) is the server not acting according to protocol?
https://www.cloudshark.org/captures/a274aeee01ee