I can't find a writeup on the format of the Server Certificate - i.e. what all the bytes are and the different variations. I have a couple of TLS/SSL books and papers, but they don't have anything on the actual format of the packet. Can someone point me in that direction? I'm trying to figure out where the public key is embedded and what all the other bytes mean. Thanks. Sutton asked 05 Jul '17, 08:34 dodge55 |
2 Answers:
The Certificate message is defined in RFC 5246, Section. 7.4.2: In TLS, this notation for In Wireshark, you can select the Certificate field, expand it subfields and study the bytes view at the bottom of the screen. See for example this screenshot where the Certificate is selected with a sample file (linked at the bottom of this post): Alternatively, you can export the selected ASN.1 bytes for inspection with alternative tools. Right-click on the selected Certificate field and use the Export Packet Bytes (Ctrl-H) option. Save the file as An alternative tool that displays the mechanical interpretation, completely with offsets, lengths and the contents: Documentation for these two tools can be found here: The capture I used above is taken from the SampleCaptures wiki, http2-16-ssl.pcapng. answered 05 Jul '17, 09:21 Lekensteyn showing 5 of 7 show 2 more comments |
answered 05 Jul '17, 09:03 grahamb ♦ Thanks. Big help. Not sure why I never found that and my books and papers don't reference that RFC in the certificate section. (05 Jul '17, 09:13) dodge55 If an answer has solved your issue, please accept the answer for the benefit of other users by clicking the checkmark icon next to the answer. Please read the FAQ for more information. (05 Jul '17, 09:14) cmaynard ♦♦ |

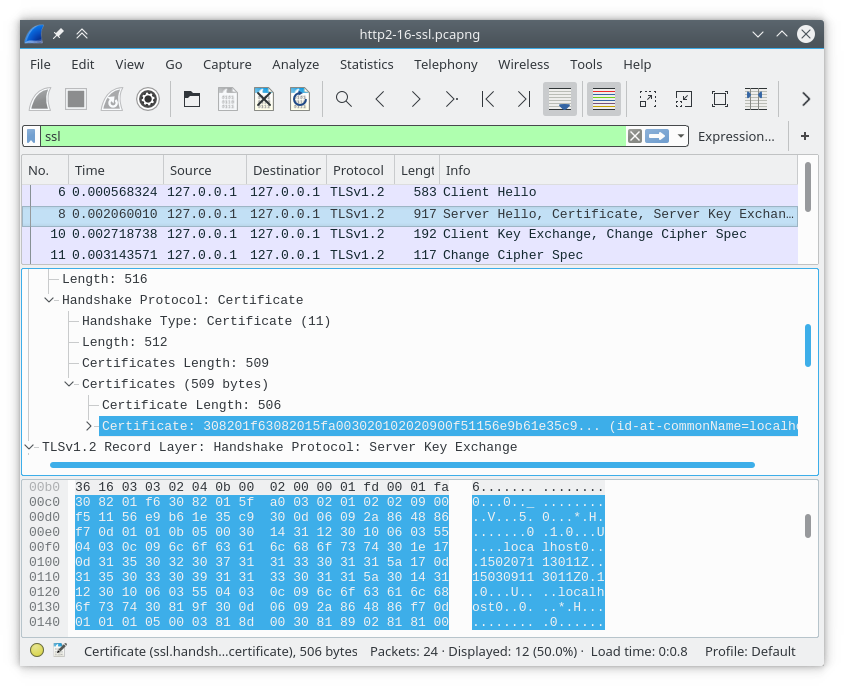
Many thanks for that. In looking at the RFC and my Wireshark output, there are several byte sequences in the Certificate that are not referenced in either the RFC or the Wireshark output. For example, between the version and the serial number, there are 2 undocumented bytes. And, the first 12 bytes of the certificate before the version number don't seem to be documented. At least WS skips over those. Any idea what those are?
Sutton
ASN.1 BER (Basic Encoding Rules) use TLV (type-length-value) encoding of fields, so in particular the two bytes you mention, "between" the version and the serial number, say the following:
02- integer09- consisting of 9 octetsThe information that the meaning of this 9-byte integer is a serial number is implicit, as the serial number is the second item of the certificate as defined in X.509:
Both the sender and the recipient know what to expect at what place as they both “know” the ASN.1 description.
Similarly, the
02:01“before” the version say that the version is a single-octet integer, and the30:82:01:5f:a0:03together say that what follows is a structure calledsignedCertificate.Most Wireshark dissectors prefer readability to detailed explanation of the structure, so this information is not added to the dissection tree.
Thanks. In many of the other packet descriptions (RFC and books), TLV bytes are explicitly mentioned. So, I thought it may be that, but I wasn’t totally sure. Being somewhat new to SSL, I like to be sure. Thanks for responding.
Actually, ASN.1 BER are more complex than just TLV, as more than a single byte may be used to encode the type and more than a single byte may be used to encode the length, or the length may not be specified at all. Second, ASN.1 has its own standard including the BER, X.690, where all this is detailed; X.509 refers to X.690 many times, often adding constraints where X.690 is not strict enough. With ITU recommendations, you rarely find everything you need in a single one, and the reference chains may be really long.
Disclaimer have not looked at the actual trace. The wiredhark ber decoder has a preference to show internal ber decoding if you are really interested in the gory details.
I see the TLV occurrences in the packet. However, still not sure how the 30:82:01:5f:a0:03 is decoded to a structure ‘signedCertificate’. Maybe you can elaborate. My packet has 2 such 30:82:… sections.
“Similarly, the 02:01 “before” the version say that the version is a single-octet integer, and the 30:82:01:5f:a0:03 together say that what follows is a structure called signedCertificate."
Follow the suggestion of @Anders: go
Edit->Preferences->Protocols->BERand click the topmost option -Show internal BER encapsulation tokens.That way, Wireshark will show you the meaning of the individual bytes.