Hello, I'm trying to use the remote ssh functionnality to capture CAN frames (virtual vcan0) But I have got an error message, see below :
EDIT: However, with the plain So the functionnality ssh remote does not work with your indications. The only way I found to capture these packets is describe below (as evidenced by) :
Then the packets are captured:
asked 12 Jul '17, 08:27 lamoule74 edited 25 Jul '17, 03:29 grahamb ♦ showing 5 of 22 show 17 more comments |
One Answer:
It seems to work with 2.4.0 and "Remote capture command" field set to The "Remote interface" field seems to be ignored and answered 25 Jul '17, 03:05 lamoule74 edited 25 Jul '17, 06:25 sindy |

I guess your capture filter syntax is incorrect. Can you provide all of your remote ssh options including your remote capture filter?
Actually I don't have a filter... When I'm using WS without "normally", I'm not lauching the sniffing interface without a filter, I specify the filter CAN with dissector j1939 later..
See below
A detail : I'm trying this from a virtual machine.
I'll try with a true session...
I think this is a known bug in the ssh interface. Try using a single space as "Remote capture filter".
hey Stig, it displays a different error message :
dumpcap produces pcapng by default which isn't supported for pipes, so you need to append a
-Pto the command. I'm not certain if that should be added to the "Remote capture binary" or the "Remote capture filter" fields.hey grahamb
command unknow with -P. this is a p capslock right?
Yes uppercase, see the dumpcap manpage for more info.
@lamoule74, can you request
tcpdumpinstead ofdumpcapdown there on the remote machine? For tcpdump, pcap is the default output format when capturing on a single interface. As you use no capture filter, the fact that with dumpcap it needs to be prepended with-fwhile with tcpdump it goes directly should not cause issues.@sindy tcpdump does not support the can frames apparently :
That's a misinterpretation of the error message. It says exactly what it reads: packet printing is not supported, i.e. the simple packet dissection engine of
tcpdumphas no clue about the internals of the CAN frames, but nevertheless they can be written to a file (as in this case no dissection is necessary). Same case e.g. with USB frames.So use
/usr/sbin/tcpdump -i can0 -w /tmp/can_test.pcapand then download can_test.pcap to the machine running Wireshark and open it there. If this works, remote ssh capture spawningtcpdumpshould work as well, because it does use-w -to allow piping of pcap rather than text output.@sindy The cuplrit seems to be the "Remote capture binary" text field: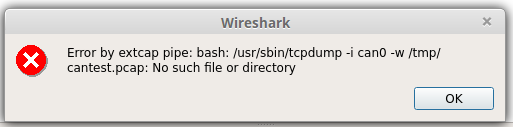
No args are allowed (I've also tried with simple and double quotes).
If I try the
/usr/sbin/tcpdump -i can0 -w -in a shell, I can capture packets.Do you know how to add args to the capture binary field?
No, the culprit of this particular failure is @lamoule74 :-)
You have logged in to the remote machine in order to test
/usr/sbin/tcpdump -i can0manually (as documented by your screenshot). So I have expected you to do exactly the same, just adding the-w /tmp/can_test.pcappart, to check that the contents of the resulting pcap file stored on the remote machine would be useful as I expected.You have instead tried to add
-w /tmp/can_test.pcapinto theremote capture binaryfield of the ssh remote capture form of Wireshark.There, you should have placed just the plain
tcpdump. The ssh remote capture will itself add-w -.What is the Wireshark version?
I must let someone else convert your Answer into a Comment, I'm getting an error when trying.
Can you log in to the remote machine, run the remote capture with "plain tcpdump" as shown below, and while it is running, use
ps axfw | grep tcpdumpon the remote machine and paste here the result?I could not convert it either. The best I could do was append the "answer" to the end of the question and delete the "answer".
@grahamb the version is 2.2.7-1 I've also tried the 2.2.6
@sindy here is the result of the command line :
[[email protected]:~] $ ps axfw | grep tcpdump 1284 ? Ss 0:00 | \_ /usr/sbin/tcpdump -i can0 -w - -f 1444 ? Ss 0:00 | \_ /usr/sbin/tcpdump -i can0 -w - -f 1522 ? Ss 0:00 | \_ /usr/sbin/tcpdump -i can0 -w - -f 1553 ? Ss 0:00 | \_ /usr/sbin/tcpdump -i can0 -w - -f 1573 ? Ss 0:00 | \_ /usr/sbin/tcpdump -i can0 -w - -f 1619 pts/2 S+ 0:00 | \_ /usr/sbin/tcpdump -i can0 -w - 1648 pts/3 S+ 0:00 \_ grep tcpdump 1111 ? Ss 0:00 /usr/sbin/tcpdump -i can0 -w - -fA bit crowded down there I'd say, I guess you are not actually running that many captures. These are most likely zombies from previous sessions so it deserves a cleanup. Most likely also their parent ssh sessions have survived so there is likely a lot of zombie processes on the machine running Wireshark.
Otherwise the command line composed by remote ssh capture seems fair to me.
-fhas a different meaning fortcpdumpthan fordumpcap, but luckily it is a harmless one (just tried).I would assume that tcpdump only has access to interfaces as root, and that is the reason why no data are received, but it is just a wild guess at the moment. So if you use the same user for direct login to beaglebone like you do for remote ssh capture, forget that I've mentioned that.
Maybe you could provide full path to
dumpcap, much like you do fortcpdump, and add the-Poption to it in the Remote capture binary field?I tried to reboot the beaglebone to prevent any side effect from the previous sessions. The
-farg is probably added by WS because I didn't try this arg on the command line.I added the
debianuser of the beaglebone to thewiresharkgroup andtcpdumpcan capture packets when launched from the command line (not with WS). There is probably no need to switch to root. But I will try.dumpcap -Pis one of the first thing I tried, but the Remote capture binary field doesn't let me add any command containing arguments (see screen capture above). If I write something else thandumpcap, WS fires an error messageError by extcap pipe: bash dumpcap -P : command is missingIf stating
"dumpcap -P"to theRemote capture binaryfield (including the"") doesn't help either, I'd say you've collected enough evidence to file a bug or even two:I can see no reason why tcpdump should not work (as said, the
-fis not harmful and the-w -is correctly added automatically as the output ofpsconfirms),I can see no reason why it should not be possible to add parameters to binary name, given that
dumpcapby default (i.e. without a command-line option) uses pcapng format, which is known not to be supported when using input pipes, even if capturing on a single interface.There is also bug 11370 asking for support of pcapng at queue input.
Ok then, let's file a bug.
Please report the bug number here in a comment.
bug 13899