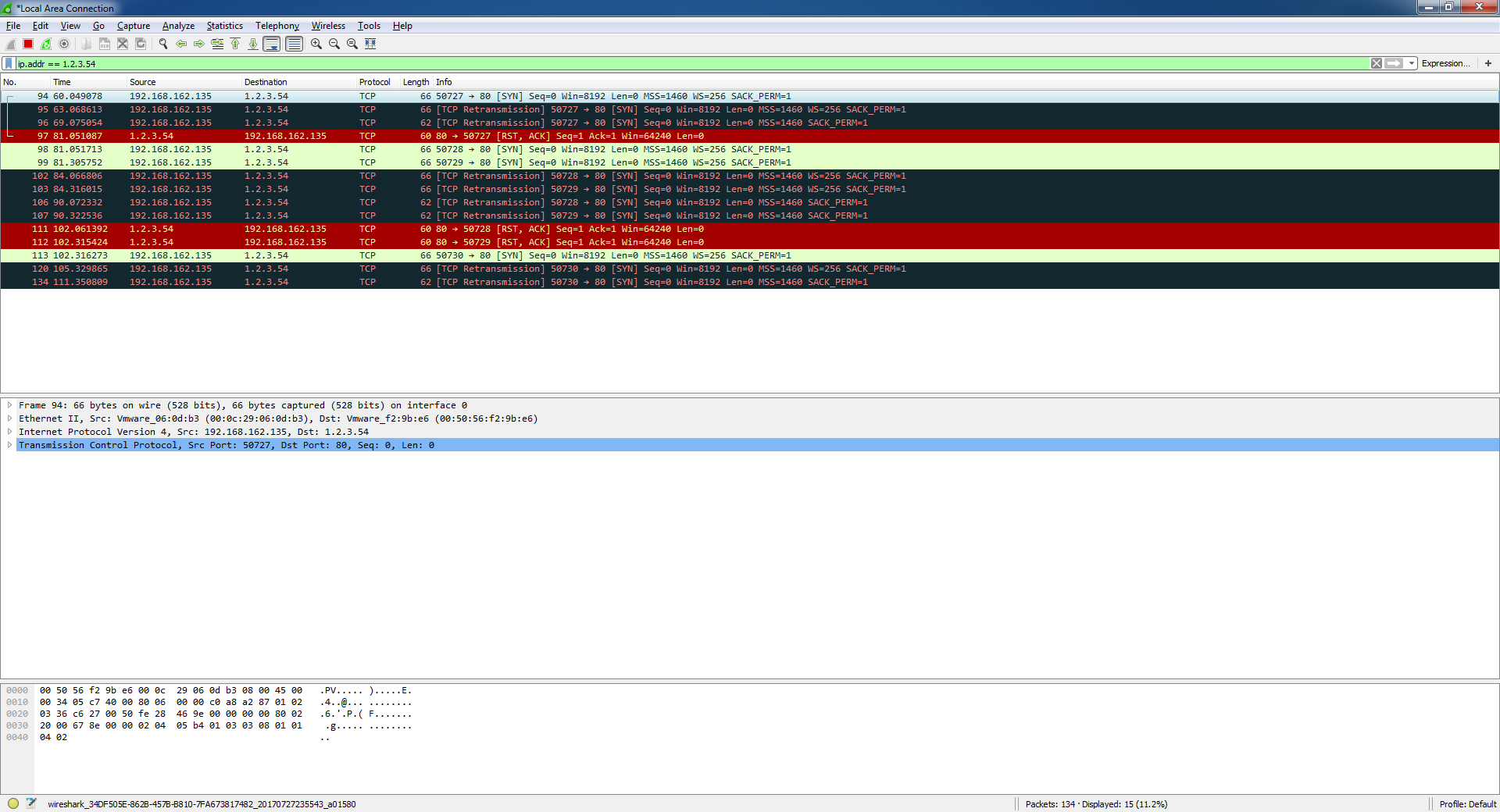
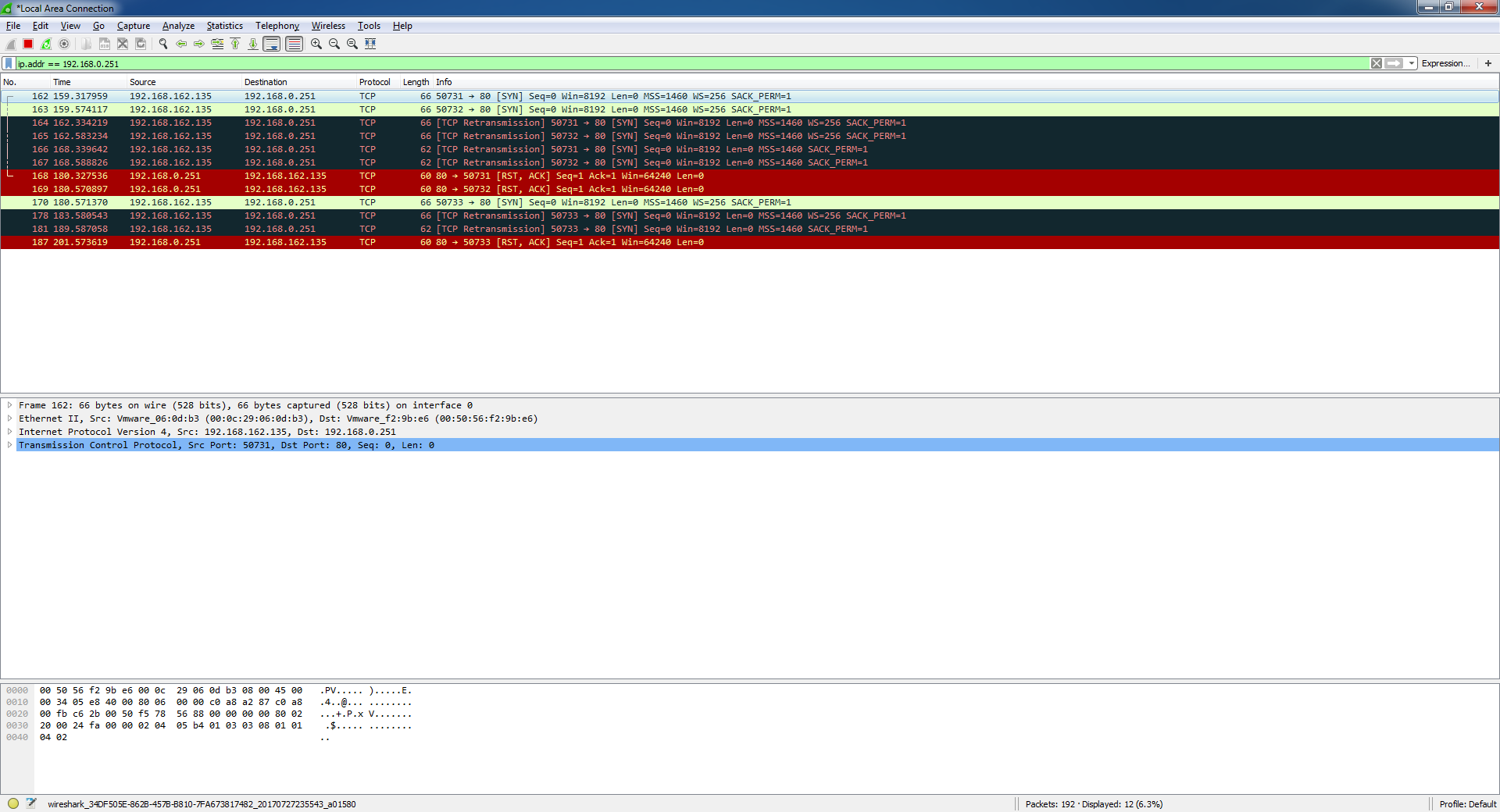
Today I had a opportunity to work with wireshark. I installed wireshark on my VMware and made some test on it. And I found a interesting thing. I sent the HTTP request to not exist computer and captured the all packet flow with wireshark. The first packet was SYN packet. And second one was re-transmission packet.(for system hadn't received any response from target computer). But surprisingly, RST packet from the target computer reached. I couldn't understand where this packet came from. I tested for 2 target computers, and in both case, I had the RST packet. So are there anyone answer about those suspicious RST packets? Thanks for reading. Regards.
asked 28 Jul '17, 00:48 Takuya Kimura |
One Answer:
The most likely explanation is that a security device exists on the route towards the IP address of the non-existent computer, and that device forges the RST packet in the name of the nonexistent computer. answered 28 Jul '17, 01:32 sindy |